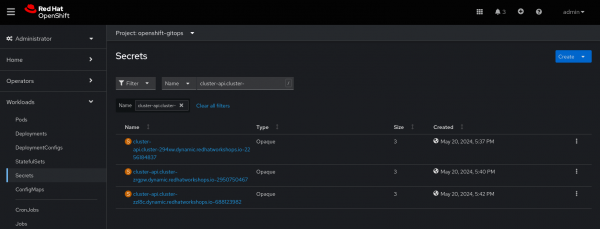
Using Argo CD to manage your Kubernetes ecosystem is an excellent GitOps approach to continuous deployment (CD). However, it can pose challenges when trying to manage multiple Kubernetes manifests for deployments, services, secrets, configurations, and other files within your Git repository.
Unlike an Argo CD Application resource that deploys resources from a single Git repository in a single cluster or namespace, ApplicationSet expands upon this use case. An ApplicationSet utilizes template-based automation to create, modify, and manage multiple Argo CD applications simultaneously, targeting multiple clusters and namespaces.
In what situations is it more convenient to use an ApplicationSet?
kind: Secret
data:
name: cluster-api.cluster-zzl8c.dynamic.redhatworkshops.io-688123982
namespace: openshift-gitops
metadata:
labels:
argocd.argoproj.io/secret-type: cluster
uat: "true"
# ...output omitted...kind: Secret
data:
name: cluster-api.cluster-294xw.dynamic.redhatworkshops.io-2256184837
namespace: openshift-gitops
metadata:
labels:
argocd.argoproj.io/secret-type: cluster
prd: "true"
# ...output omitted...You can configure ApplicationSet as follows:
apiVersion: argoproj.io/v1alpha1
kind: ApplicationSet
metadata:
name: code-with-quarkus-application-set
namespace: openshift-gitops
spec:
generators:
- clusters:
selector:
matchLabels:
dev: "true"
- clusters:
selector:
matchLabels:
uat: "true"
- clusters:
selector:
matchLabels:
prd: "true"
template:
metadata:
name: "{{name}}-code-with-quarkus"
spec:
project: default
source:
repoURL: https://github.com/luisfalero/code-with-quarkus-manifest.git
targetRevision: HEAD
path: ./cluster-generator/manifests
destination:
server: "{{server}}"
namespace: redhat
syncPolicy:
syncOptions:
- CreateNamespace=true
automated:
prune: true
selfHeal: trueCreate the following application with the parameters:
- Application name:
code-with-quarkus-application-set - Project: default
- Sync policy: Automatic
- Repository URL: https://github.com/luisfalero/code-with-quarkus-manifest
- Revision: HEAD
- Path:
./cluster-generator - Cluster: https://kubernetes.default.svc
- Namespace:
openshift-gitops
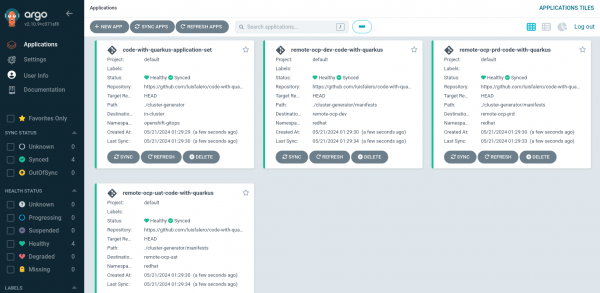
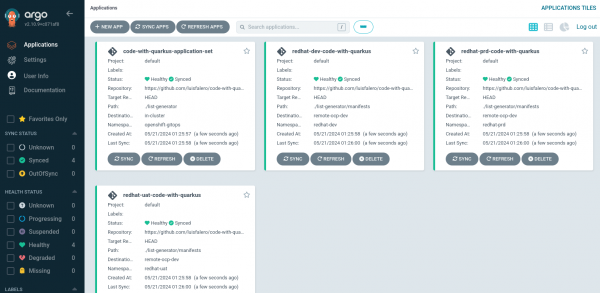
We verified the application deployed in the three different clusters, as shown in Figure 7.
Git generator
You can configure ApplicationSet as follows:
apiVersion: argoproj.io/v1alpha1
kind: ApplicationSet
metadata:
name: code-with-quarkus-application-set
namespace: openshift-gitops
spec:
generators:
- git:
repoURL: https://github.com/luisfalero/code-with-quarkus-manifest.git
revision: HEAD
directories:
- path: git-generator/manifests/overlays/*
template:
metadata:
name: "{{path.basename}}-code-with-quarkus"
spec:
project: default
source:
repoURL: https://github.com/luisfalero/code-with-quarkus-manifest.git
targetRevision: HEAD
path: "{{path}}"
destination:
server: https://api.cluster-zrgpw.dynamic.redhatworkshops.io:6443
namespace: "{{path.basename}}"
syncPolicy:
syncOptions:
- CreateNamespace=true
automated:
prune: true
selfHeal: trueWe verified the contents of the git-generator folder.
git-generator
├── application-set.yaml
└── manifests
├── base
│ ├── deployment.yaml
│ ├── kustomization.yaml
│ └── service.yaml
└── overlays
├── development
│ └── kustomization.yaml
├── production
│ └── kustomization.yaml
└── testing
└── kustomization.yamlCreate the following application with the parameters:
- Application name:
code-with-quarkus-application-set - Project: default
- Sync Policy: Automatic
- Repository URL: https://github.com/luisfalero/code-with-quarkus-manifest
- Revision: HEAD
- Path:
./git-generator - Cluster: https://kubernetes.default.svc
- Namespace:
openshift-gitops
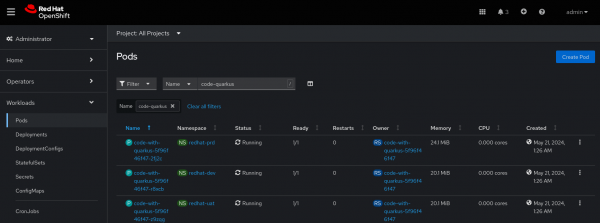
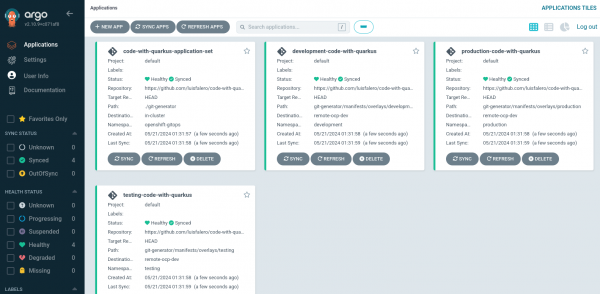
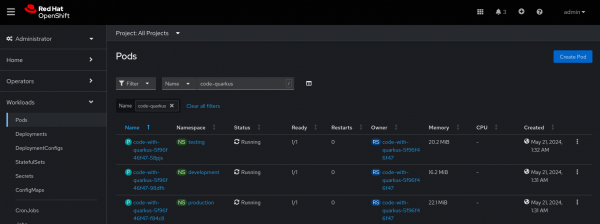
We verified that a single application was deployed in three different namespaces within a single cluster using a single procedure. See Figure 8.
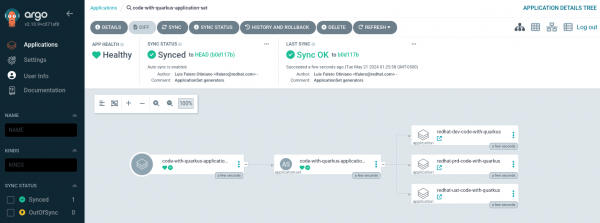
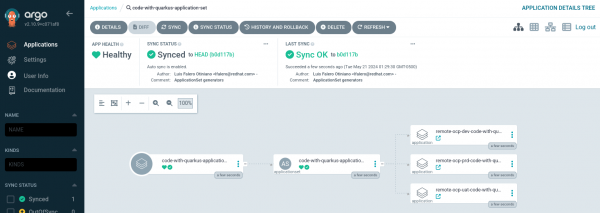
We reviewed the details of the created ApplicationSet (Figure 9).
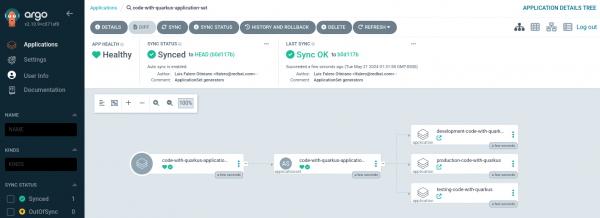
We verified the application deployed in the three different namespaces. See Figure 10.
Matrix generator
kind: Secret
data:
name: cluster-api.cluster-zzl8c.dynamic.redhatworkshops.io-688123982
namespace: openshift-gitops
metadata:
labels:
argocd.argoproj.io/secret-type: cluster
uat: "true"
remote-ocp: "true"
# ...output omitted...kind: Secret
data:
name: cluster-api.cluster-294xw.dynamic.redhatworkshops.io-2256184837
namespace: openshift-gitops
metadata:
labels:
argocd.argoproj.io/secret-type: cluster
prd: "true"
remote-ocp: "true"
# ...output omitted...You can configure ApplicationSet as follows:
apiVersion: argoproj.io/v1alpha1
kind: ApplicationSet
metadata:
name: code-with-quarkus-application-set
namespace: openshift-gitops
spec:
generators:
- matrix:
generators:
- clusters:
selector:
matchLabels:
remote-ocp: "true"
- list:
elements:
- namespace: redhat-dev
- namespace: redhat-uat
- namespace: redhat-prd
template:
metadata:
name: "{{name}}-{{namespace}}-code-with-quarkus"
spec:
project: default
source:
repoURL: https://github.com/luisfalero/code-with-quarkus-manifest.git
targetRevision: HEAD
path: ./matrix-generator/manifests
destination:
server: "{{server}}"
namespace: "{{namespace}}"
syncPolicy:
syncOptions:
- CreateNamespace=true
automated:
prune: true
selfHeal: true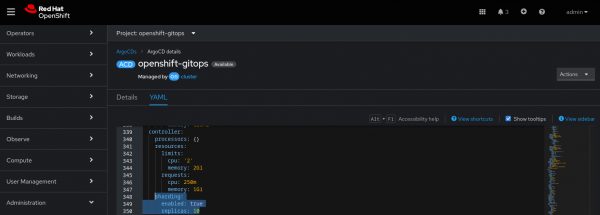
Create the following application with the parameters:
- Application name:
code-with-quarkus-application-set - Project: default
- Sync Policy: Automatic
- Repository URL: https://github.com/luisfalero/code-with-quarkus-manifest
- Revision: HEAD
- Path:
./matrix-generator - Cluster: https://kubernetes.default.svc
- Namespace:
openshift-gitops
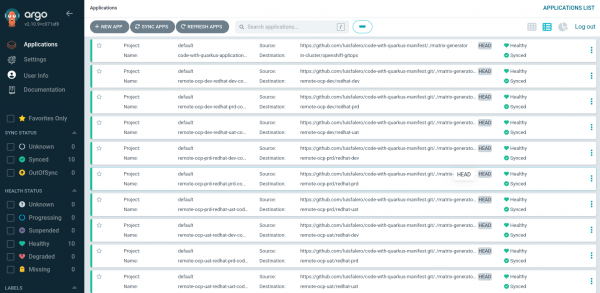
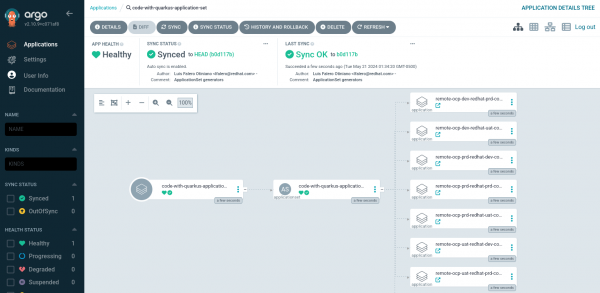
We verify that a single application was deployed in three different namespaces across three clusters with a single procedure. See Figure 12.
We reviewed the details of the created ApplicationSet, as shown in Figure 13.
Conclusion
Using Argo CD with ApplicationSet and generators provides a robust and flexible solution for managing deployments in complex Kubernetes environments. The ability to deploy and manage multiple applications across various clusters and namespaces, as well as from different Git repositories, greatly simplifies the continuous deployment (CD) process and ensures orderly and efficient management of infrastructure resources. The combination of these tools offers a comprehensive solution for deployment and management needs in Kubernetes environments, enabling development teams to maintain an agile and secure workflow.