Securing inter-cloud connections through end-to-end with TLS is necessary, ensuring not only the confidentiality and integrity of data exchanged between cloud environments but also safeguarding against unauthorized access. While inter-router communication in Skupper is always fortified with mutual TLS, it's essential to note that, by default, communication between services and routers does not have this encryption layer. Deploying TLS in client-router and router-service is possible to fortify the entire communication ecosystem.
Skupper ensures mutual TLS (mTLS) for inter-router communications by default, and users have the option to enhance security by enabling TLS specifically between services and the Skupper routers, with the flexibility to either auto-generate certificates through Skupper or integrate custom certificates as needed.
Enabling TLS with generated certificates
This option addresses scenarios in which services belonging to the same Skupper network communicate over TLS. To expose a service over TLS with generated certs, we will add the flag generated-tls-secrets in the skupper expose command:
skupper expose deployment payments --address payments --port 5001,5002 --protocol http2 --generate-tls-secrets
This will generate a server certificate that will be stored as a secret on each site with the name of the service plus the prefix "skupper-tls" and configured in the routers. For instance, in this example the server certificate will be stored in the secret skupper-tls-payments, as shown in Figure 1.
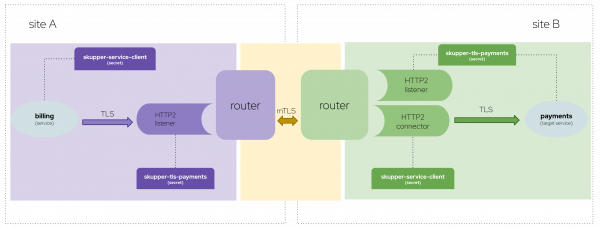
The generated certificates are not distributed within the Skupper network. They are unique to each site because they are signed with the particular site's CA, which will be stored in the secret skupper-service-client.
Following the example, the billing service must use the CA stored in the skupper-service-client secret of the same site in which it resides. The payments microservice needs to utilize the certificate stored in skupper-tls-payments, which belongs to its respective site.
With this configuration, the traffic will be encrypted between the service and the router using generated certificates, then encrypted between the routers with their respective certificates, and finally encrypted between the router and the target service with a different set of generated certificates.
Enabling TLS with custom certificates
This option is valid for establishing TLS between services within the same Skupper network or external clients sending requests to a service deployed in a Skupper network. This flexibility exists because the user has control over the certificates used.
Before exposing the service in Skupper, the user must store the server certificate and the CA in two secrets. For this example, we will call it server-cert-secret and ca-cert-secret. This has to be repeated in all the sites of the Skupper network, using the same two names for those secrets.
To expose a service over TLS with custom certs, we will add the flags tls-trust and tls-certs in the following skupper expose command (Figure 2).
skupper expose deployment payments --address payments --port 5001,5002 --protocol http2 --tls-trust ca-cert-secret –tls-cert server-cert-secret
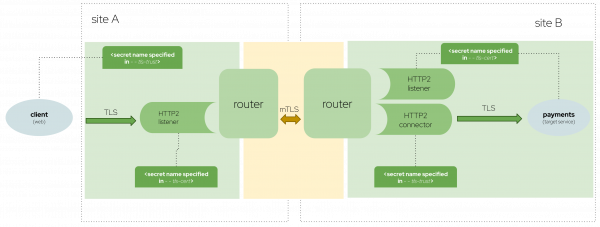
The traffic will be encrypted between the service and the router using the custom certificates, then encrypted between the routers with their respective certificates, and finally, encrypted between the router and the target service the same custom certs. For that reason, an external client only needs to use the same CA stored in all the sites, as specified in the --tls-trust flag, to send a request to a service included in a Skupper network.
