Web developers and IT professionals are the foundations of any quality business’ data security.
However, with technology constantly changing and evolving as well as becoming more consumer-friendly, this data’s vulnerability only increases and it can often be hard to even notice how this new technology can actually affect your company until it occurs. Despite this, ignorance to modern hacking techniques does not refute their inability to transform even the smallest of devices into a weapon with which to infect or intrude upon data and the effects of this on a company can mean massive destruction in the infrastructure and beyond.
One of the newest data security threats posed to the IoT, in particular, is the rise of the wearable technology industry. With companies like FitBit and Google developing glasses, fitness trackers, and watches that make everyday life a little bit easier, it may seem as if the wearable tech industry is nothing more than a fun and exciting way to incorporate technology into the average consumer’s life, however, this is not entirely the case.
How Wearable Tech Affects the IoT and the Cloud
The IoT and the countless devices being connected within it have been under serious scrutiny since its implementation in our society, however, wearable technology alone could lead to a myriad of data breaches putting other smart tech breaches to shame in the process. In fact, when utilizing wearable devices and connecting to your cell phone, both cyber security and the Internet of Things, which are important technological integrations in your company, are at risk.
According to a study in 2014 by Pricewaterhouse Cooper’s Report, 20 percent of US adults already owned at least one wearable technology device and now, three years later, the numbers have continued to rise. In fact, it is projected that, by the year 2020, 50 billion new connected wearable devices will have been added to the IoT. ON top of this, in 2016, the embedded technology market reached $169 billion and is expected to grow to over $200 billion by 2021, according to a study done by Reportlinker. Despite the millions of wearable tech devices worldwide already being utilized, it is apparent that these numbers only continue to increase and yet the safety of said devices is far from efficient even now.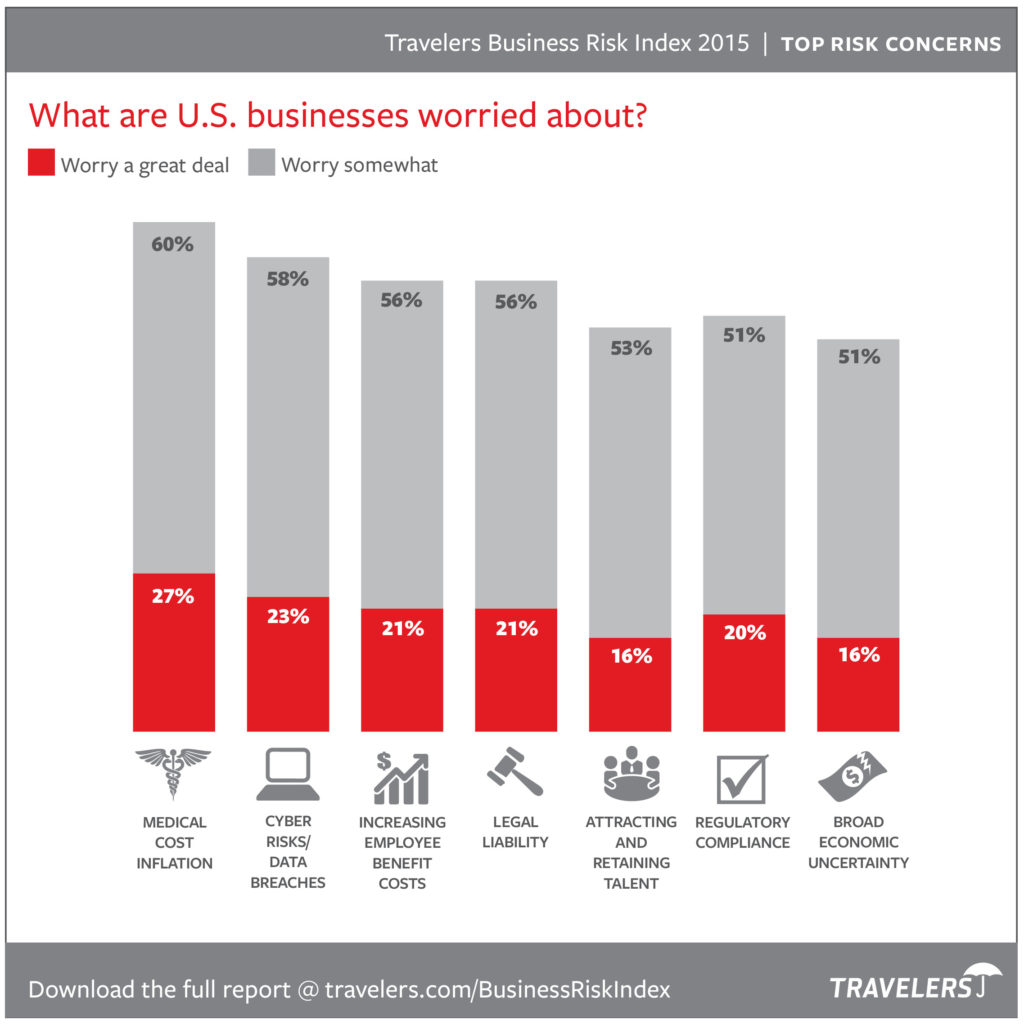
In 2015, the second biggest concern of businesses according to Travelers was cyber security and for good reason. In fact, with the Mirai Malware attacks on both Krebs on Security and DNS service provider Dyn, the fear implicated in the rise of the IoT-dependent consumer generation only continues to grow. With nearly every wearable tech device being connected to the IoT within the cloud, this opens up a massive ‘can of worms’, so to speak, for data security and web developers alike.
For instance, when using OpenShift in Google Cloud, your SSD-based persistence storage as well as other various credentials are exposed to the cloud if not handled correctly and not used in conjunction with LUKS by Red Hat Enterprise Linux or some other FDE. In turn, when an individual connects their cell phone to the cloud and uses Bluetooth to connect a wearable tech device to the phone, this creates a chain of devices leading hackers into the main data they wish to intrude upon in a far easier manner.
Although FDE can prevent many of these issues, there are still ways for hackers to infiltrate the data collected by your company via the cloud and this is the major issue wearable technology faces today. Although we now know that Mirai Malware specifically targeted hacked DVR’s and cameras, the malware could very easily affect other devices using weak usernames or passwords and manipulate the data they receive from these devices to their benefit or infect the other devices connected to the cloud in the process.
Furthermore, countless businesses have begun to focus on making the data analytics they receive more useful towards the actual improvement of their company and, with this, an entirely new concern arises regarding data security and the cloud when it comes to wearable tech. With the implementation of strategies such as CX single metrics for blended indexes or blockchain databases being introduced to the cloud, this data is now becoming far more easily accessible for hackers, and devices such as wearable tech could mean that this data could become far more vulnerable than ever before.
On top of this, multiple companies have begun to turn to integrating global payroll in the cloud which will ultimately allow for hackers to access data about finances, sensitive employee information, and even be able to surmise which banks these individuals utilize and their personal usernames and passwords to access their accounts. With the ability to use wearable tech to their benefit, hackers will have countless ways to infiltrate business data with very little effort in return causing more than just a concern for IT professionals and web developers alike.
How Wearable Tech Can Be Infiltrated and What It Could Cause
Due to the slightly small storage space of these devices, wearable tech is not truthfully the primary source of the data infiltration, in most cases. However, it is, in fact, the means with which hackers find an entry point into the actual device in question (aka a cell phone) and this is where the issue lies. Since MDM policies still do not cover wearables, the data that it is connected to is highly vulnerable. In fact, Techcrunch has said, “The data collected and stored on your mobile device can be worth ten times the value of a credit card on the black market”.
By using Bluetooth radio module devices to their advantage, hackers have the ability to ‘sniff’ for signals and collect data from any devices nearby without even infiltrating the system at all. In doing this, they can retrieve sensitive data quite easily and use this data to create a profile of the wearable tech user in question. On top of this, by using the unique hardware address these devices transmit, hackers are able to track the devices and sometimes even probe them remotely for serial numbers or other sensitive information. Furthermore, most of these devices utilize apps, which use clear text while users are asked for login credentials and these devices will in some cases, send data to up to 14 IP addresses likewise. With this information, hackers can easily manipulate data to read information about other users including users that these individuals may work with and trick databases into executing commands sent by external agents.
A great example of this ‘sniffing’ technique was actually demonstrated by Candid Wueest, a member of the Symantec team, at Black Hat 2014. Wueest and his team were able to track wearable technology in the crowd and prove the power of sniffing Bluetooth devices with a Raspberry Pi firsthand. With this said, the Bluetooth capabilities of these devices remain to be one of the most difficult aspects of wearable technology to this day. When asked about the project, Wueest said, “ These are serious security lapses that could lead to a major breach of the user database.”
Another example of hacking via wearable tech comes in the form of hacking into a Smart Watch. By using the data Smartwatches receive such as spatial info, location, temperature, heart rate, and blood oxygen levels, hackers can learn valuable information about the watch’s user. And not only use techniques such as phishing or botnets to infiltrate the watch but also use their health information to find the individual’s identity and passwords which can help them to log into work accounts, data programs, and even customer’s sensitive data likewise. On top of this, a lot of sports teams in universities have been using technology to improve youth athlete fitness, however, wearable technology connected to their phones and school forums may help them to improve their health but also lead to data breaches at their school and with their personal information alike.
Furthermore, if the device is actually a health device such as a FitBit or even a Wearable TENS for EMS therapy, hackers can use this data to actually attack your physical well-being likewise by manipulating data. On top of this, wearable sensors can diagnose diseases so by creating false positives, this can cause individuals to panic over their health for no particular reason. Although this is not as common and most health companies have begun to seriously crack down on device security, there is still a highly important threat that they pose nonetheless.
Lastly, by using a signal interceptor such as the sniffing device above, hackers can take their manipulation and intrusion to the physical level. By following a high-profile individual from the company past a RFID device such as a wireless identity authenticator which takes the individual’s code from his wearable tech, the hacker can determine this sensitive code and be given the ability to roam the business even after hours collecting data and other sensitive and valuable items with ease.
How Developers Can Tackle Wearable Tech Concerns
This new form of data insecurity can seem like a rather unfair fight for a developer. With millions of devices and only a few web developers and IT individuals in every company, the odds are most certainly against the technologically inclined. However, with every new device, the fear of security breaches looms not far behind and, like all of the devices before them, wearable tech will soon be under control for most high profile companies and consumers alike.
Although it is impossible to control the weak usernames of countless consumers around the world, building your cloud security, encrypting Bluetooth data, creating biometric authentication systems, implementing location and remote-lock capabilities. Encrypting shared data via techniques such as simple file and FDE or more complex systems such as Steganography and Single-Photon Generation are ways to keep your company safe without running the risk of being infiltrated via wearable tech in the future.
According to Deborah Bothun, PWC’s US advisory EMC leader, “Businesses must evolve their existing mobile-first strategy to now include the wearable revolution.” Therefore, improving the security of the cloud and improving upon Bluetooth encryption are two of the most substantial ways to ensure that your company’s security is intact when utilizing wearable tech.
For instance, Bluetooth offers an encryption API, which will ensure that the data being transferred between a device and the stored data location is secure although it does drain battery life of the devices slightly quicker. Furthermore, by securing the cloud using multiple diverse operating systems, you can ensure that the data being presented via Cloud-compatible programs is not an easy target for hackers looking to use wearable tech for their malicious intent.
Similarly, although multiple researchers have been developing ways to surpass face authentication security measures, biometric authentication remains one of the most reliable ways to secure devices such as wearable tech and cell phones. Equally, by implementing location and remote-lock capabilities in these devices, hackers could steal these devices from individuals and find that all data on said items is erased by the time they get home.
Lastly, by using encryption techniques such as FDE, you can ensure that your data is safe and the decryption key is only distributed between parties deserving of it. On top of this, new research suggests that fully homomorphic encryption, which allows users to analyze their encrypted data without sacrificing confidentiality through decryption, may become one of the newest and most effective encryption methods of this modern era. In fact, Charles Lickel, Vice President of Software Research at IBM says on the subject, “Fully homomorphic encryption will enable businesses to make more informed decisions, based on more studied analysis, without compromising privacy.” By using this along with encrypted data transfer processes such as steganography and single photon generation, you can not only ensure data security but also use some of the most reliable and modern applications for encryption and security likewise.
Although wearable tech is one of those double-edged swords in the IT industry, it doesn’t always have to remain that way. In fact, by implementing these strong encryption and security measures alone, you can turn the few cons involved in wearable tech into a thing of the past. From there, the implications of these devices in the IT and development industry are endless and the use of them to create a strong and well-connected development and technology department in business is at last possible.
Last updated: May 31, 2024
