
Gain visibility into Red Hat Quay with Splunk
Learn how to forward Red Hat Quay access logs to Splunk for long-term visibility and use Splunk queries to monitor activity like pushes and pulls.

Learn how to forward Red Hat Quay access logs to Splunk for long-term visibility and use Splunk queries to monitor activity like pushes and pulls.

Learn to configure Red Hat Quay's proxy cache for on-demand image pulls from remote registries, boosting container distribution.

Learn how to receive notifications about the status of Red Hat's services.

Learn how to automate the management of short-lived credentials to access resources within Quay using the External Secrets Operator (part 3 of 3).

Discover methods for leveraging short-lived credentials to access Quay resources securely within Red Hat OpenShift (part 2 of 3).
Learn how to increase security by enabling short-lived credentials within Quay (part 1 of 3).

See how to use oc-mirror to install OpenShift in disconnected environments and discover how the latest version simplifies the disconnected mirroring experience.

Discover how to implement a distributed transaction solution using Jakara EE Jakarta Enterprise Beans (EJB) in this in-depth guide.

Download Red Hat software for application developers at no-cost.

Demonstrate how ArgoCD with Red Hat ACM can manage different clusters and...

Learn how to build an end-to-end reactive stream processing application using Apache Kafka as an event streaming platform, Quarkus for your backend, and a frontend written in Angular.

Find out how you can track and report on vulnerabilities across a large container registry like Quay.io using Clair, the open source container security tool.
Get a hands-on introduction to Tilt, a tool that automates the inner-loop

This exercise, created by Ian Lawson, demonstrates how you can go from initial
Explore the results of performance and scale team's database profiling efforts and their strategies for optimizing overall application performance.

Explore performance and scale team's approach to optimizing Quay application performance to improve stability and cost-effectiveness.
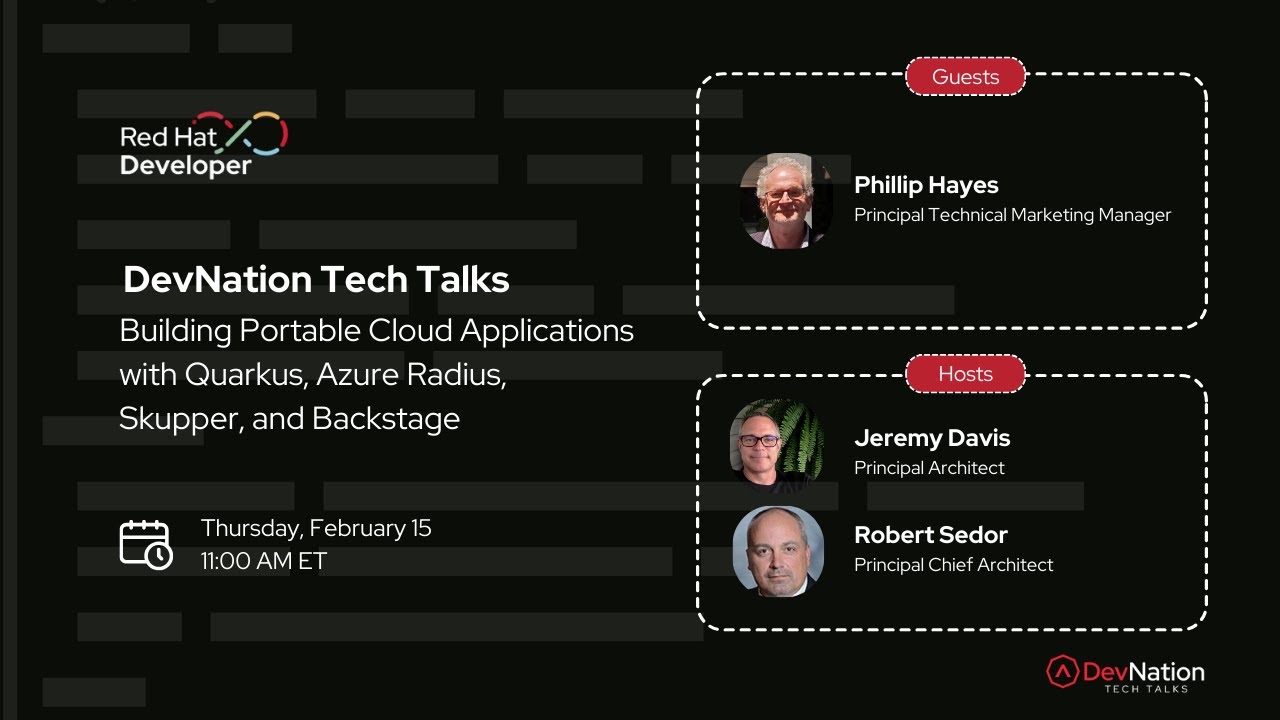
DevNation Tech Talk: Building portable cloud applications with Quarkus, Azure Radius, Skupper, and Backstage

This article demonstrates how to build the OpenShift console dynamic plugin and deploy on OpenShift.

Learn how to set up an automated method to deploy your application to OpenShift clusters using a GitOps approach.

Learn how to set up a CI pipeline to compile and package a javascript game app into a Docker image using Jenkins on OpenShift in this demo.
