
Deeper visibility in Red Hat Advanced Cluster Security
Discover the new features in Red Hat Advanced Cluster Security that allow integrating component health and security data into Prometheus for better observability and alerting.

Discover the new features in Red Hat Advanced Cluster Security that allow integrating component health and security data into Prometheus for better observability and alerting.

Eliminate static secrets and adopt a zero trust security model in your CI/CD pipelines using Tekton, HashiCorp Vault, and user-defined networks on OpenShift.

Red Hat Advanced Cluster Security 4.8 offers external IP visibility, enabling security teams to identify external connections and validate network policies.
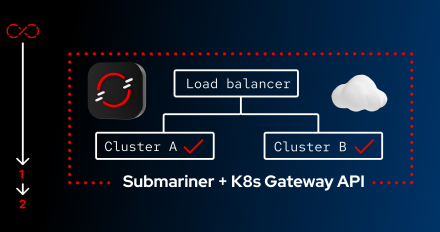
Learn how Red Hat technologies combine with open source tools to achieve

Discover how Red Hat Advanced Developer Suite helps developers strengthen their Jenkins CI/CD pipelines and innovate at speed.

This article provides a guide to integrating Red Hat Advanced Cluster Security with the multicluster global hub for centralized security data collection across managed clusters. It covers the setup requirements, configuration steps, and key annotations needed to enable seamless data aggregation and observability through a unified dashboard.
Get an introduction to the inner and outer loop framework and explore tooling and components that help platform engineers implement the DevSecOps cycle.

Download Red Hat software for application developers at no-cost.

Explores how Red Hat OpenShift technologies can aid the transition from monolith to microservices, simplifying the process and ensuring a robust and secure application.

Application security is paramount, whether deployed in on-premise, hybrid, or multi-cloud environments. The financial implications of not securing software and services can run into millions, highlighting the importance of robust protective measures.

DevNation Tech Talk: Simplifying containers and Kubernetes on your laptop with Podman Desktop

Discover the new developer-focused features in Red Hat OpenShift 4.13.
Get an overview of the GitOps principles and learn why they are essential for new IT projects in this excerpt from the GitOps Cookbook.

GitOps workflows, Go Toolset container images, SaaS security controls, and more: Explore recent popular content from Red Hat Developer.
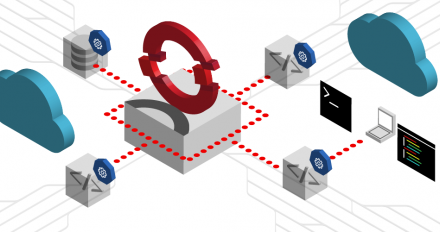
Discover how to improve the security of your Software-as-a-Service deployment at the hardware, OS, container, Kubernetes cluster, and network levels.

Learn Git best practices for GitOps deployment workflows and Git management tips, including effective usage of Git branch and trunk-based development workflows.
Security policies can be deployed through CI/CD and Red Hat Advanced Cluster Security for Kubernetes. Read on to learn how.

Select tutorials for in-person events

Download GitOps Cookbook: Kubernetes Automation in Practice for recipes and examples to help you implement GitOps and CI/CD in a cloud-native environment.
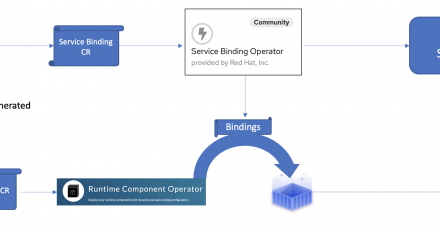
Deploy enterprise-grade runtime components into Kubernetes with Runtime Component Operator, Service Binding Operator, and Open Liberty Operator.
