Red Hat CodeReady Dependency Analytics, powered by Snyk Intel Vulnerability database, helps developers find, identify, and fix security vulnerabilities in their code. In the latest 0.3.2 release, we focused on supporting vulnerability analysis for Golang application dependencies, providing easier access to vulnerability details uniquely known to Snyk, and other user experience improvements.
Vulnerability analysis for Golang applications
With this release, developers can run vulnerability analyses for their Golang application stacks. The analysis identifies vulnerabilities at the Golang module and package levels, including direct and transitive dependencies. It also supports semver and pseudo versions.
go.mod file component analysis
Opening a go.mod file in the IDE editor window triggers the plug-in's component analysis. The component analysis highlights the vulnerabilities for each dependency listed in the go.mod file. The plug-in provides the option to examine each vulnerability's details. You can then remedy the vulnerability by switching to the recommended version using the Quick Fix option.
Editing, saving, or reopening the go.mod file will also initiate the component analysis.
Figure 1 shows the output from the IDE editor's component analysis, with a summary of the findings in the notification window in the bottom-right corner. This summary lists the total number of vulnerabilities and exploits found in the manifest.
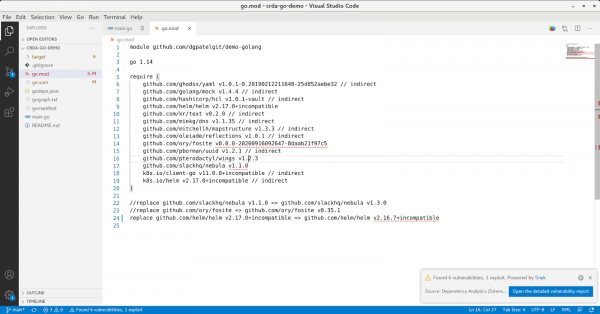
The vulnerabilities and exploits are highlighted in the IDE editor with red and blue underlines. Hovering over an issue displays a diagnostic summary of the specific package's vulnerability profile, as Figure 2 illustrates.

Each diagnostic message provides the following information:
- The total number of vulnerabilities
- The number of Snyk-specific security advisories
- A count of known exploits
- The highest severity level across all vulnerabilities
- The number of packages and modules used in the source
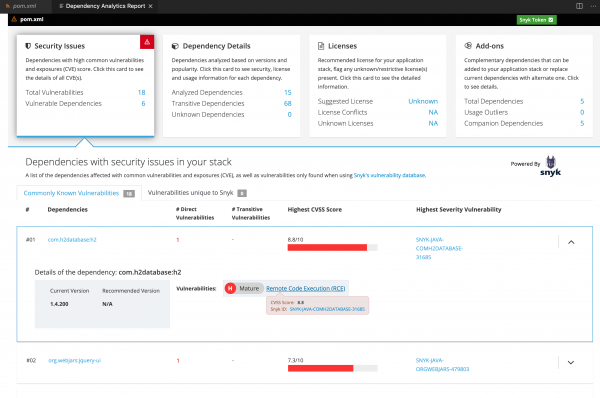
Details about security vulnerabilities
To access a detailed report of security issues in a go.mod file (see Figure 3), click the button in the notification window; then right-click the go.mod file and select Dependency Analytics Report. Alternatively, you can click the pie-chart icon labeled Open Vulnerability Report in the top-right corner.
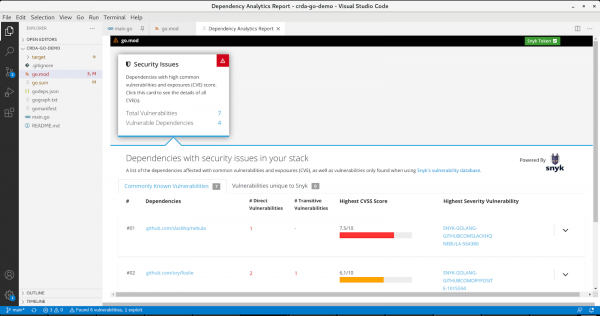
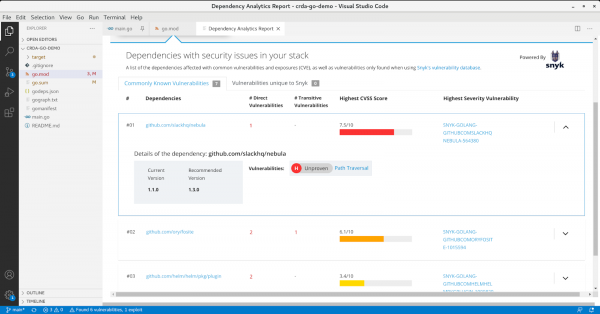
Accessing vulnerability details
The CodeReady Dependency Analytics plug-in is powered by Snyk Intel, a vulnerability database provided by Snyk. By signing up for a free Snyk account, you can view each vulnerability's known exploits and details about vulnerabilities uniquely known to Snyk.
Figure 5 shows how to register with Snyk and save your token with the CodeReady Dependency Analytics plug-in.
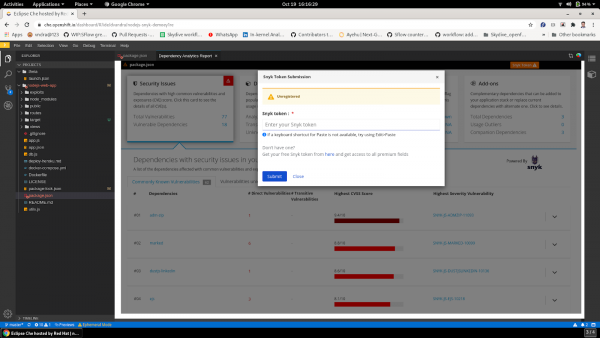
Figure 6 shows the vulnerabilities and exploit details after the Snyk token has been saved.
Enabling telemetry
The Dependency Analytics extension is now integrated with the Red Hat Commons extension. This enables Red Hat to collect telemetry specific to:
- The type of operating system running Visual Studio Code
- The development language of the manifest file scanned by Dependency Analytics
- The time and frequency of vulnerability report generation using stack analysis and component-level analysis
- Registration with Snyk
By collecting telemetry, Red Hat can gain valuable feedback about the extension's usage patterns and provide future enhancements for developers.
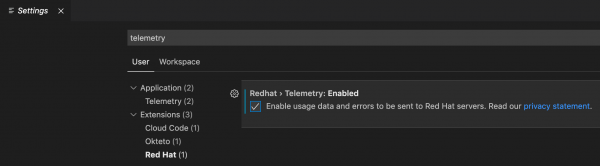
The Dependency Analytics extension only collects telemetry if developers opt in to enable it. You can opt in any time by clicking Accept (see Figure 7) or selecting the checkbox for Red Hat Telemetry under Preferences → Settings (see Figure 8).
Get started with Red Hat CodeReady Dependency Analytics
Red Hat CodeReady Dependency Analytics is available as a plug-in for Visual Studio Code, Eclipse Che, Red Hat CodeReady Workspaces, and JetBrains IntelliJ-based IDEs.
To get started with the CodeReady Dependency Analytics IDE extension or provide feedback, check out the following links.
- Get the Visual Studio Code extension for CodeReady Dependency Analytics.
- Get the IntelliJ-based IDE extension for CodeReady Dependency Analytics.
- Access CodeReady Dependency Analytics via the fabric8-analytics-server API.
- Provide your feedback via the Git issues repository.
About Snyk
Snyk is a developer-first security company that helps software-driven businesses develop fast and stay secure. Snyk finds and fixes vulnerabilities and license violations in open source dependencies and container images. Snyk's solution is built on Snyk Intel, a comprehensive, proprietary vulnerability database maintained by an expert security research team in Israel and London. With tight integration into existing developer workflows, source control, and CI/CD pipelines, Snyk enables efficient security workflows and reduces mean-time-to-fix. For more information or to get started with Snyk for free today, visit https://snyk.io.
Last updated: February 5, 2024