
X.509 user certificate authentication with Red Hat's single sign-on technology
Configure a browser authentication flow using X.509 user-signed certificates with Red Hat's single sign-on technology and OpenSSL.

Configure a browser authentication flow using X.509 user-signed certificates with Red Hat's single sign-on technology and OpenSSL.

Learn how to go beyond the simple login API and enable the full force of Keycloak's authentication and authorization features using the Keycloak REST API.

Use Keycloak's authentication service provider interface to develop a custom MobileAuthenticator class that you can run in your JBoss EAP container.
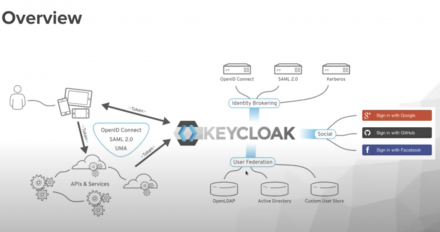
In this DevNation Tech Talk, we take a deep dive into Keycloak to handle open source identity and access management with modern applications and services.
Secure Vue.js apps with Keycloak | DevNation Tech Talk
Learn how to generate a JWT token and then validate it using API calls, so Keycloak's UI is not exposed to the public.

How to get a valid public certificate for your Red Hat Single Sign-On instance using Let's Encrypt and Lego. This avoids the inherent problems with self-signed certificates.

Learn how to configure NGINX to use Keycloak/Red Hat SSO for authentication with OAuth/OIDC for federated identity. In this setup, Keycloak will act as an authorization server in OAuth-based SSO and NGINX will be the relaying party.

How implement a Single Sign-on (a.k.a. SSO) in your application with an easy and OpenSource project? The answers is Keycloak, further info read the article!

In this session, we’ll discover KeyCloak progressively and in an interactive way: No slides, just 100% live coding; focused on the Spring Boot adapter provided by Keycloak.


Securing Microservices using JSON Web Tokens (JWT) and Red Hat SSO, by Thomas Qvarnstrom



