First to fall over when the atmosphere is less than perfect
Your sensibilities are shaken by the slightest defect
You live your life like a canary in a coalmine...
When Sting and The Police sang those lyrics, I doubt they had microservices, Istio, Kubernetes, and OpenShift in mind. Yet here we are, years later, using the Canary Deployment pattern to ease code into production.
[This is part eight of my ten-week Introduction to Istio Service Mesh series. My previous article was Part 7: Istio Dark Launch: Secret Services.]
Proceed with Caution
If you're not familiar with the Canary Deployment pattern, it's quite simple: You start up your next version of your software--a microservice, in our case--and then grant limited access to a small group of users. If that is a success, you slowly grow the group of users until the software either fails--the canary in the coal mine died--or you successfully reach 100 percent of users. By purposefully and carefully easing your software into production, and by intelligently deciding which users will request the new version, you can limit the risk and maximize the feedback.
Of course, Istio makes this easy while giving you several good options for intelligent routing. And--you may have heard this before--you can do it all without changing your source code.
Searching for Safari
One easy routing criteria is to allow only certain browers to have access to your site. For example, let's say you want to limit access to Safari users so that they use version 2 of your microservice. The following Istio route rule will do just that:
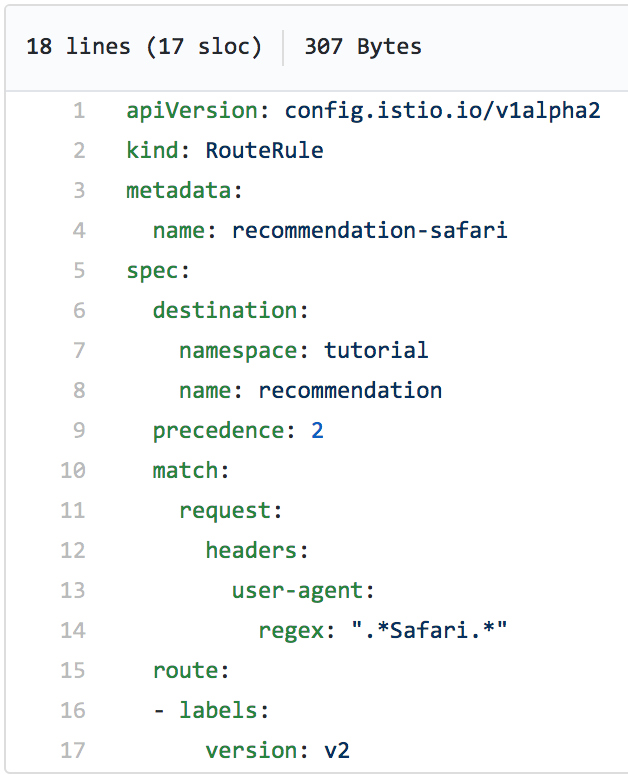
After applying this route rule, we can launch a loop of curl requests from the command line to the microservice to mimic real-life activity. The result is that only version 1 of our microservice is responding to the requests:
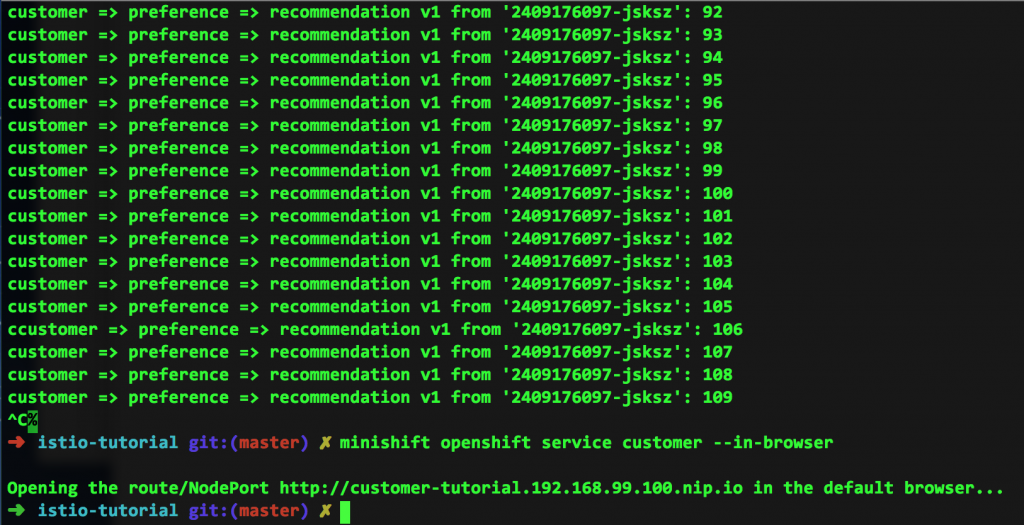
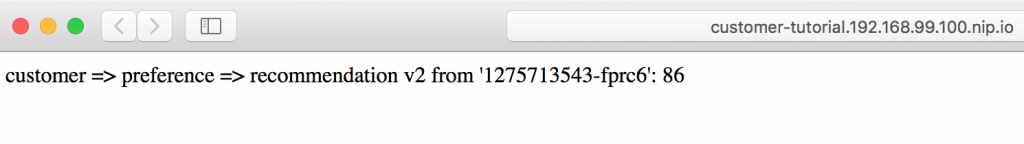
Where is the version 2 traffic? Well, in my particular case, since I'm running curl from the command line, all of the traffic is being routed to version 1. Notice that at the end of the above screen capture, I run the request from my browser (Safari), which results in this:
Unlimited Power
As you probably noticed, using a regular expression to route requests is very powerful. Consider this following example; I'm sure you can easily figure out what it does:
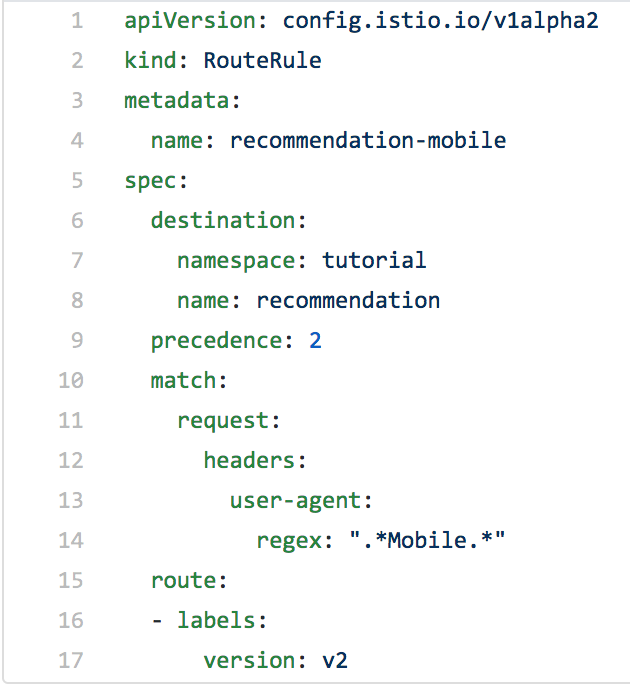
Given these examples, you are probably already imagining what you can do.
Being Smart About It
Smart routing, particularly the ability to use regular expressions against request headers, means you can direct traffic however you want as you ease new code into production. It's easy, requires no changes to your source code, and can be quickly undone if necessary.
I Want More
Want more? Want to start experimenting with Istio, Kubernetes, and OpenShift on your own PC? Perhaps follow a tutorial? You're in luck: We (the Red Hat Developer team) have put together this awesome tutorial. We also have made available all the bits you need. Simply surf over to the tutorial and knock yourself out.
I guess you could say it will really make your deployments sing.
All articles in the "Introduction to Istio" series:
- Part 1: Introduction to Istio Service Mesh
- Part 2: Istio Route Rules: Telling Service Requests Where to Go
- Part 3: Istio Circuit Breaker: How to Handle (Pool) Ejection
- Part 4: Istio Circuit Breaker: When Failure Is an Option
- Part 5: Istio Tracing & Monitoring: Where Are You and How Fast Are You Going?
- Part 6: Istio Chaos Engineering: I Meant to Do That
- Part 7: Istio Dark Launch: Secret Services
- Part 8: Istio Smart Canary Launch: Easing into Production
- Part 9: Istio Egress: Exit Through the Gift Shop
- Part 10: Istio Service Mesh Blog Series Recap
