The recent release of Red Hat JBoss EAP 8.0 includes native support for OpenID Connect (OIDC) via the elytron-oidc-client subsystem. OIDC is an identity layer that enables clients, such as JBoss EAP, to verify a user’s identity based on authentication performed by an OpenID provider. For example, you can secure your JBoss EAP applications using the Red Hat build of Keycloak as the OpenID provider.
In this article, we will use the elytron-oidc-subsystem to secure a simple web application using Microsoft Entra ID (formerly Azure Active Directory) as the OpenID provider.
For more information about JBoss EAP 8.0's native OpenID Connect support, refer to the product documentation.
Prerequisites
- A local installation of JBoss EAP 8.0. Download the installation manager from Red Hat Developer.
JBOSS_HOMEenvironment variable set as the installation folder for JBoss EAP 8.0.- A Microsoft Azure account with an active subscription.
Connect a web application to Microsoft Entra ID
-
Check out the sample application here.
-
Create a file
src/main/webapp/WEB-INF/oidc.jsonwith the following contents:{ "client-id" : "<<from azure>", "provider-url" : "<<from azure>", "ssl-required" : "EXTERNAL", "credentials" : { "secret" : "<<from azure>>" } } -
In the Azure portal, go to the All Services page and click Microsoft Entra ID.
-
In the left-hand menu, select App registrations and click New Registration. You will see the Register an application page shown in Figure 1.
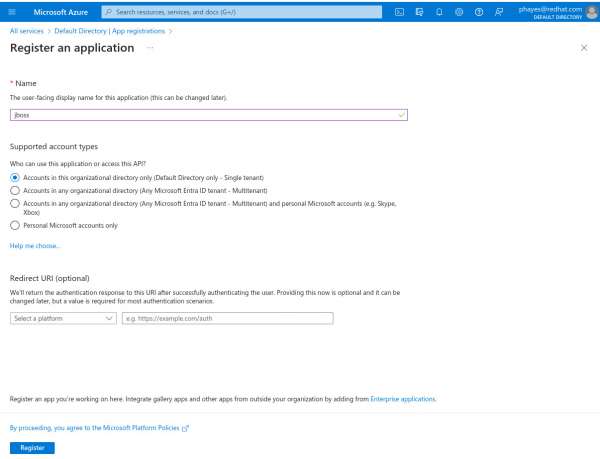
Figure 1: Register a new application Figure 1: Register a new application. -
Enter a name (e.g.,
jboss) and click the Register button. This brings you to the App registrations overview page for your application. -
Click Add a Redirect URL, then click Add a Platform.
-
Select Web; you will see the Configure Web page, as shown in Figure 2.
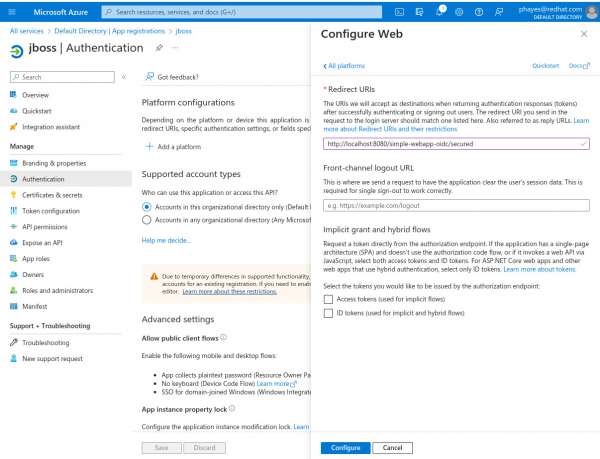
Figure 2: Configure a web application Figure 2: Configure a web application. -
Enter the following URL:
http://localhost:8080/simple-webapp-oidc/secured -
Click the Configure button.
-
Go back to the Overview page and click Add a certificate or secret.
-
Select + New Client secret. This brings you to the Add a client secret page (Figure 3).
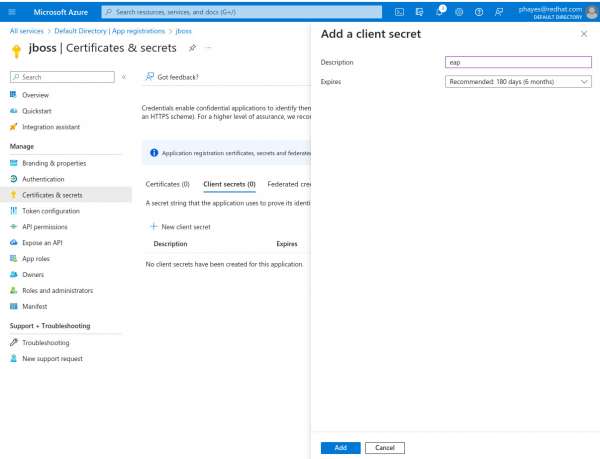
Figure 3: Create a new secret Figure 3: Create a new secret. -
Enter a description (e.g.,
EAP) and click the Add button. -
Copy the value shown on the next page and paste this value into
src/main/webapp/WEB-INF/oidc.jsonas the secret value. -
Return to the Overview page and click on Endpoints.
-
Copy the value from OpenID Connect metadata document and paste it into
src/main/webapp/WEB-INF/oidc.jsonas theprovider-url. Be sure to remove the text/.well-known/openid-configuration. -
Return to the Overview page. Copy the Application (client) ID and paste this value in
src/main/webapp/WEB-INF/oidc.jsonas theclient-id. -
Save the changes to the
oidc.jsonfile.
Our connection to Microsoft Entra ID is now configured, and we can deploy our application to JBoss EAP 8.0 and test the authentication.
Test the Azure authentication
-
First, we're going to start our JBoss EAP 8.0 instance. Run the following command to start JBoss EAP 8.0:
$JBOSS_HOME/bin/standalone.sh -
We can now deploy our app. From the folder containing the sample application source code, enter:
mvn wildfly:deploy -
We can access our application using http://localhost:8080/simple-webapp-oidc/.
Click Access Secured Servlet. Now you'll be redirected to the Azure login page (Figure 4). Log in with your Azure credentials.
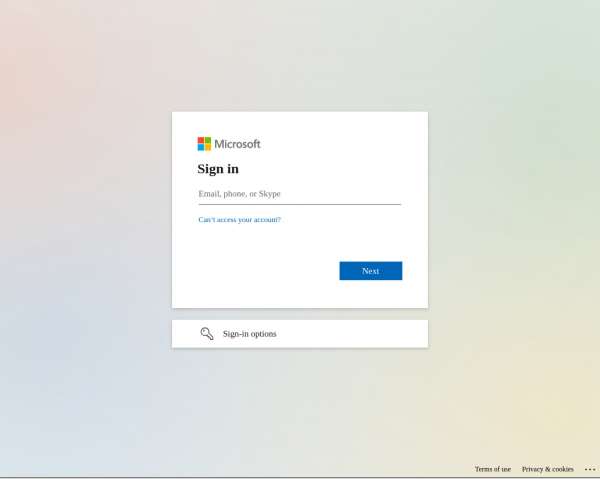
Figure 4: Azure login page Figure 4: Azure login page. -
Next, you'll be redirected back to our application and you should see the Secured Servlet page:
Secured Servlet
Current Principal 'xxxx'
We were able to successfully log in to our application via the Microsoft Entra ID provider!
Summary
With JBoss EAP 8.0, OpenID Connect support is provided by the included elytron-oidc-subsytem. In this article, we demonstrated how to secure a simple JBoss EAP 8.0 web application with Azure authentication via Open ID Connect.
For further information on JBoss EAP 8.0 OpenID support, refer to the documentation.
