Visualize Performance Co-Pilot data with geomaps in Grafana
Learn how to use Grafana geomaps to visualize performance data from systems monitored by Performance Co-Pilot (PCP) and grafana-pcp, a Grafana plug-in for PCP.

Learn how to use Grafana geomaps to visualize performance data from systems monitored by Performance Co-Pilot (PCP) and grafana-pcp, a Grafana plug-in for PCP.

Learn how to enable Red Hat Lightspeed in disconnected environments with Red Hat Satellite 6.18. Set up advisor and vulnerability services to manage risk.

Use Podman Desktop to create a bootable .NET 10-based application using image

Learn how to migrate from Red Hat Ansible Automation Platform 2.5 RPM on Red Hat Enterprise Linux (RHEL) 9 to the containerized version 2.6 on RHEL 10.

What RHEL 8 and 9 users need to know about Python 3.9 reaching the end-of-life phase upstream.

Learn how to build reproducible, container-native OS images on IBM Power Systems using bootc, from environment setup to capturing and exporting the image.
This article discusses the advantages of Red Hat's .NET container images and provides an overview of the available images.

Learn how to run Ruby applications in FIPS mode on Red Hat Enterprise Linux (RHEL) using the Ruby OpenSSL library.

This article describes the design and flow of the confidential cluster operator, focusing on its role in deploying and managing confidential Kubernetes clusters.

Learn how to use Red Hat Lightspeed image builder to create images that are more compliant to a wide set of regulatory policies and frameworks.

Download the Red Hat Lightspeed API cheat sheet to learn how to obtain Red Hat Enterprise Linux system details and interact with specific Lightspeed applications.

Discover how LF Energy SEAPATH, an open source reference design for real-time platforms, is being used on RHEL to modernize electrical substation automation.

Now .NET 10 is available for RHEL and OpenShift, bringing new features like C# 14/F# 10 support, performance improvements, and updated APIs.

Learn how to use the new RHEL 10 soft reboot feature in image mode (bootc) to significantly reduce downtime for OS updates.

Explore the top developer features in RHEL 9.7 that enhance the developer experience.

Discover the RHEL 10.1 new features and updates, designed to improve the developer experience.

Learn about the libdwfl_stacktrace initiative for the elfutils project and improvements to the kernel’s perf_events infrastructure to benefit solutions like SFrame.
Deploy image mode for Red Hat Enterprise Linux step-by-step using Kickstart, a
Use Podman Desktop to create a bootable Flask-based application using image mode

Learn how to develop Red Hat Enterprise Linux applications using Toolbx and Windows Subsystem for Linux (WSL) and how to choose the best method for your needs.
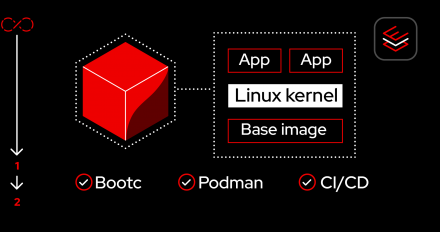
Learn how to locally build and run a bootable container (bootc) image in Podman

Learn how to use eBPF to identify which Netfilter rule caused a packet drop in the Linux kernel.

Your Red Hat Developer membership unlocks access to product trials, learning resources, events, tools, and a community you can trust to help you stay ahead in AI and emerging tech.

Celebrate our mascot Repo's first birthday with us as we look back on the events that shaped Red Hat Developer and the open source community from the past year.
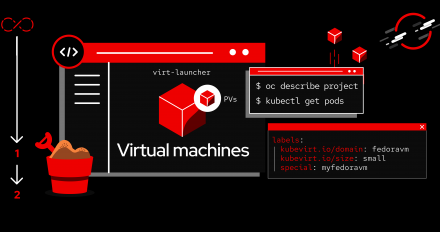
Learn how to run and analyze FIO I/O tests at scale on OpenShift Virtualization VMs to determine optimal storage backend performance.