Security flaws in third-party libraries are so common that many organizations integrate automated dependency analysis into their development workflows. This article introduces a new GitHub Action for Red Hat CodeReady Dependency Analytics that lets you integrate code scanning into your continuous integration (CI) pipeline while you are developing your code in a GitHub repository.
Automating security in the CI/CD pipeline
Developers always hope that the dependencies that are present or added to a project's manifest are free of vulnerabilities. Over the past few years, software code security has gone from a "nice to have" addition to a necessity. Many organizations today are taking steps to ensure that code going into production does not pose any security risks.
A common solution for this problem is to integrate a code scanning tool into the continuous integration (CI) pipeline that checks for vulnerabilities in the incoming dependencies or performs nightly checks to scan for newly introduced security risks. Code scanning lets you detect vulnerabilities prior to release, eliminating the cybersecurity risks that they involve. A number of databases, notably the CVE list, provide interfaces to tools that check the databases' contents against dependencies in code.
Integrating a security analysis tool with the CI workflow augments the developers' ability to add security validation while updating incoming dependencies. The addition of the Red Hat CodeReady Dependency Analytics GitHub Action to the GitHub marketplace has made code scanning easier for users in the CI/CD process.
What is CodeReady Dependency Analytics?
CodeReady Dependency Analytics, introduced in the article Vulnerability analysis with Red Hat CodeReady Dependency Analytics and Snyk Intel, provides vulnerability and compliance analysis for your application's dependencies, along with recommendations to address security vulnerabilities and licensing issues. The Snyk Intel Vulnerability Database is a curated database of both new and previously known open source software security advisories.
CodeReady Dependency Analytics is also available as a plug-in for Visual Studio Code, Eclipse Che, Red Hat CodeReady Workspaces, and JetBrains IntelliJ-based IDEs. These integrations allow developers to "shift left" to detect and fix potential security vulnerabilities in the development process. Using the analytics in an IDE helps fix the security issues early, but adding the same tool into your continuous integration pipeline ensures that you don’t miss any security issues before the code goes into production.
Note: See Vulnerability analysis for Golang applications with Red Hat CodeReady Dependency Analytics for an introduction to using CodeReady Dependency Analytics with applications written in Go.
A GitHub Action for vulnerability analysis
The CodeReady Dependency Analytics Github Action is a vulnerability scanner that uses CodeReady Dependency Analytics in the GitHub Actions space. This action scans for vulnerabilities in the project's dependencies and uploads results to the GitHub repository as a SARIF file, which allows vulnerabilities that are found to be integrated into the project's Security tab. To date, this action supports applications written in Go, Python, Node.js, and Java.
This action also works seamlessly with pull requests, so project owners can check for vulnerabilities in the project dependencies when they are modified by a pull request.
Setting up the GitHub Action
The steps described in this article are the minimal steps required to run a CodeReady Dependency Analytics scan on any project. However, you may need to perform additional steps depending on your project requirements.
Install the command-line interface
The first thing to configure before running the action is the CodeReady Dependency Analytics command-line interface (CLI). This can be easily installed using the OpenShift Tools Installer GitHub Action as follows:
- name: Install CRDA cli
uses: redhat-actions/openshift-tools-installer@v1
with:
source: github
crda: latest
Set up the tool stack
If not already done, you must set up the tool stack based on your project. For example, if you are running a Java project, you can use the setup-java action to set up Java in the workflow.
Configure authentication
Sign up for the Snyk token, then click through the wizard. You do not need to provide it with any permissions if you don't want to. Go to Account settings to find your Synk token (also known as the key). Set this token into a repository secret and provide the created secret in the synk_token input.
The workflow looks like this:
name: CRDA scan Java project
on:
push:
pull_request:
jobs:
scan:
name: Analyse Java project
runs-on: ubuntu-latest
steps:
- name: Checkout project
uses: actions/checkout@v2
- name: Install CRDA cli
uses: redhat-actions/openshift-tools-installer@v1
with:
source: github
crda: latest
- name: Setup Java
uses: actions/setup-java@v2
with:
distribution: temurin
java-version: 11
cache: maven
- name: CRDA Scan and upload SARIF
id: scan
uses: redhat-actions/crda@v1
with:
snyk_token: ${{ secrets.SNYK_TOKEN }}
- name: Print Report Link
run: echo ${{ steps.scan.outputs.report_link }}
Once the workflow finishes successfully, the Security tab in the GitHub user interface (UI) is populated with the vulnerabilities found and has the relevant details. Figure 1 shows the details of a particular vulnerability.
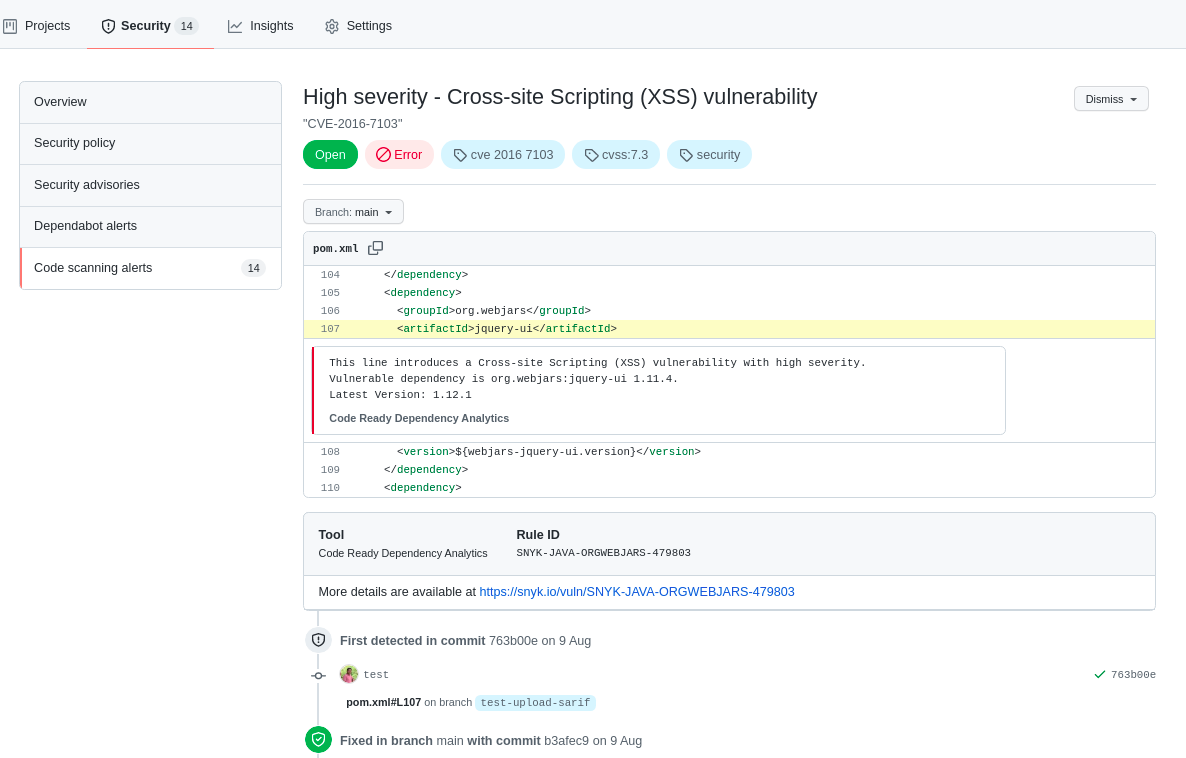
Additional features in the GitHub UI
Before we finish, let's look at some key features of CodeReady Dependency Analytics that work in the GitHub user interface instead of the CodeReady Dependency Analytics CLI.
SARIF output and upload
To support a one-stop solution for dependency scanning and uploading, this GitHub Action supports SARIF output and upload. The action uploads the SARIF file to GitHub, which then displays the vulnerabilities details in the GitHub Security tab as well as inline within pull requests.
Figure 2 shows the vulnerability details in the GitHub UI for a pull request when the code scan finishes.
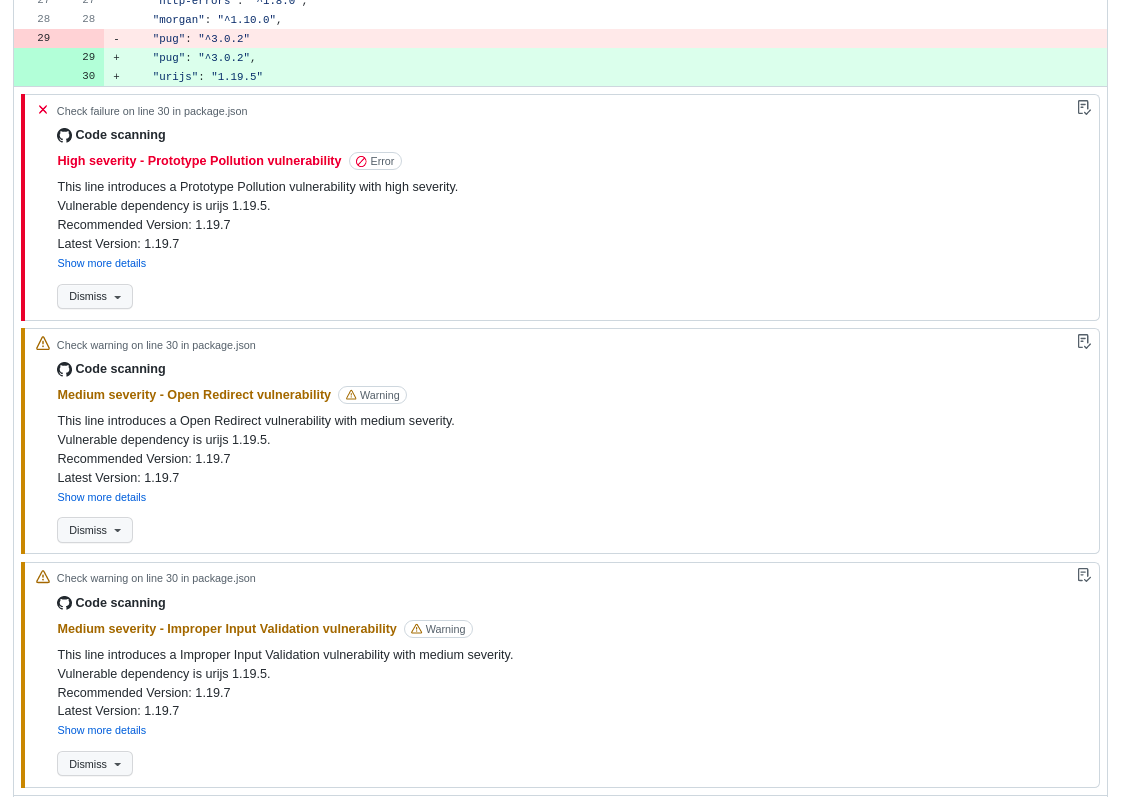
Code scanning in pull requests
Many organizations devote time to code reviews, and having another set of eyes on the modified code is always good. Organizations have also started to realize the value of reviewing security issues in the code, but not everyone has the expertise to look for them. Therefore, adding code scanning to the pull request checks substantially aids the reviews of pull requests.
The CodeReady Dependency Analytics GitHub Action can run code scans on pull requests. To scan pull requests, the pull request's code must be checked out. Therefore, to avoid running malicious code, the action comes with a preconfigured mechanism for labeling pull requests that allows maintainers to verify a pull request's code before installing any dependencies or running scans. Once the CodeReady Dependency Analytics scan is complete, the pull request is labeled according to the scan’s result, as shown in Figure 3.
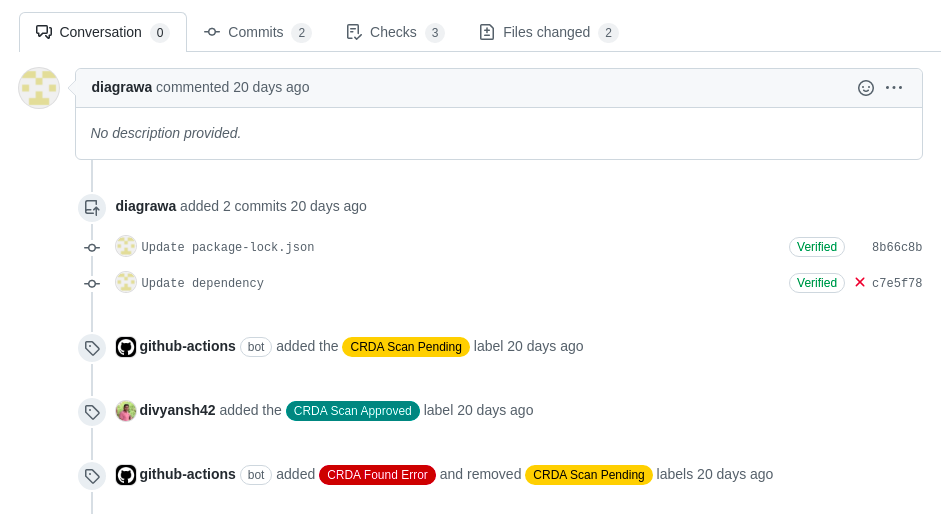
Manifest autodetection
The CodeReady Dependency Analytics GitHub Action makes it easier to scan a project’s dependencies by providing a built-in manifest detection feature. If the project uses a standard default manifest name, the user doesn’t have to explicitly provide it. However, the manifest name can be provided in the input manifest_file.
Dependency installation
The CodeReady Dependency Analytics CLI expects users to install project dependencies before running a code scan. This CodeReady Dependency Analytics GitHub Action makes dependency installation easier by automatically installing dependencies. The action has a default installation command corresponding to each supported language, which generally fulfills most projects' requirements. However, you can provide a custom dependency installation command using deps_install_cmd.
Conclusion
Millions of people use GitHub for software development, and most incorporate dependencies from open source libraries. The only way to keep up with newly discovered vulnerabilities and avoid inserting these security risks into your application is to integrate scanning into your routine workflows. The CodeReady Dependency Analytics GitHub Action provides invaluable protection to your code by finding and displaying vulnerabilities while you are developing your code on GitHub.
Last updated: November 8, 2023