Managing the security of your projects applications can be an overwhelming and unmanageable task. In today's world, the number of newly created frameworks and languages is continuing to increase and they each have their own security drawbacks associated with them.
The wide variety of security scanners available can help find vulnerabilities in your projects, but some scanners only work with certain languages and they each have different reporting output formats. Creating reports for customers or managers and viewing analytics using different security tools in different projects can be a very time-consuming task.
Enter DefectDojo.

DefectDojo is an Open Source Vulnerability Management Tool that helps to automate and reduce the time that a security engineer needs to spend in the application security process. DefectDojo will help a security engineer to spend more time carrying out security investigations and finding vulnerabilities instead of creating reports and creating metrics.
Features
DefectDojo Dashboard
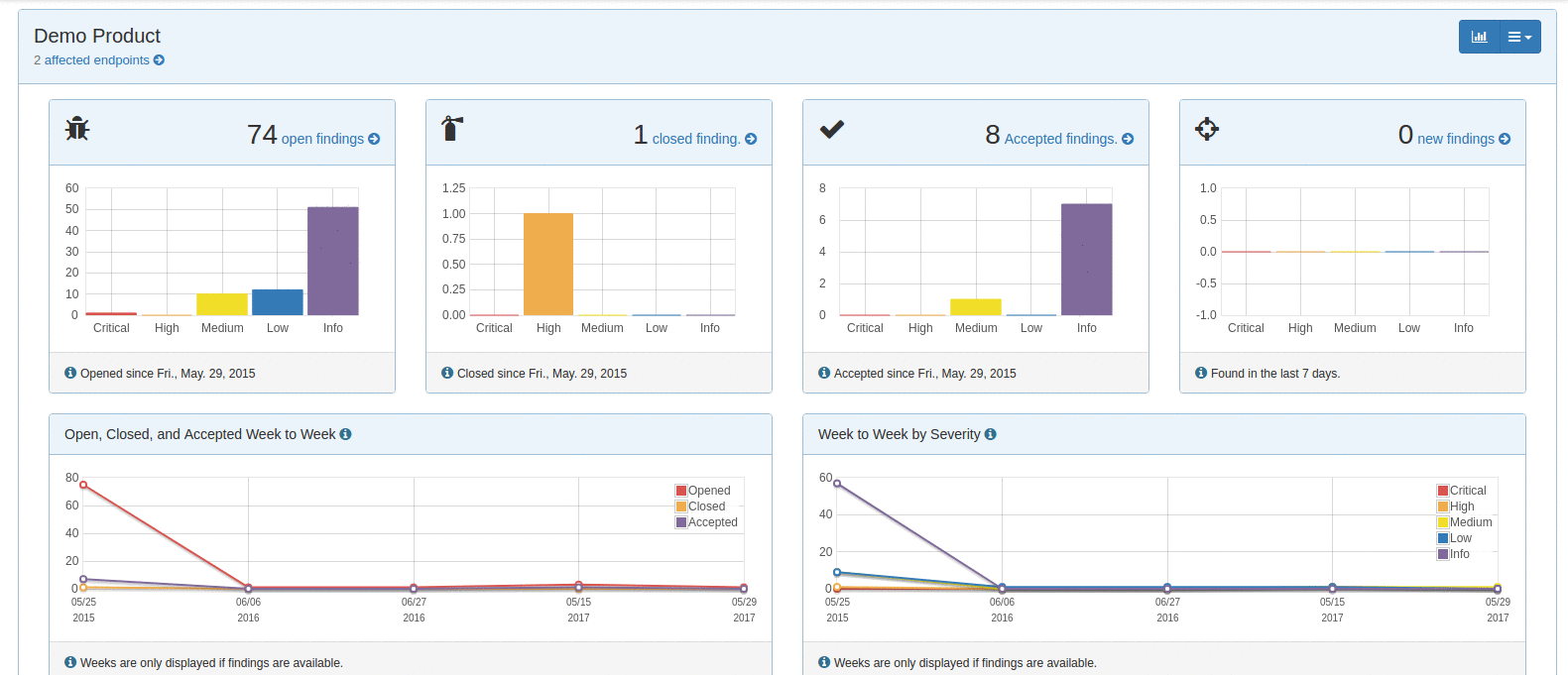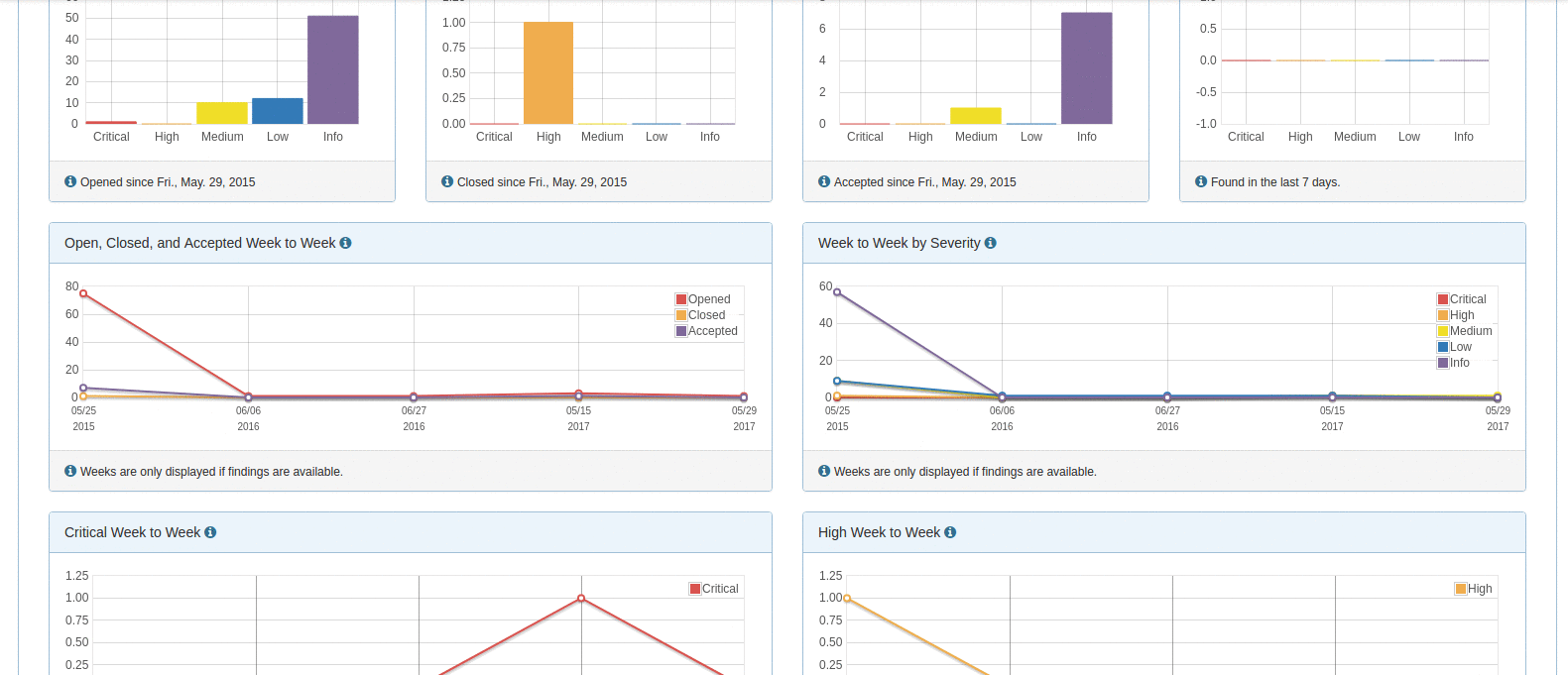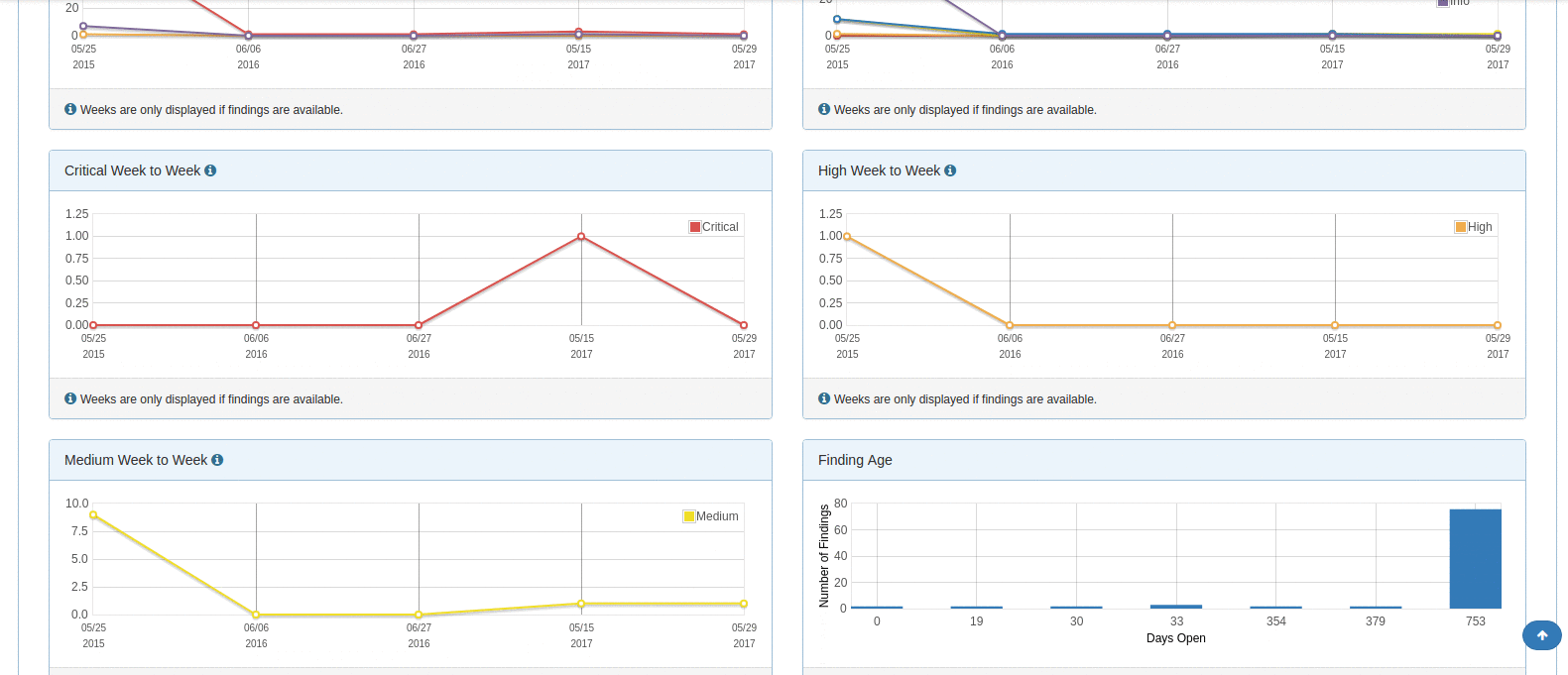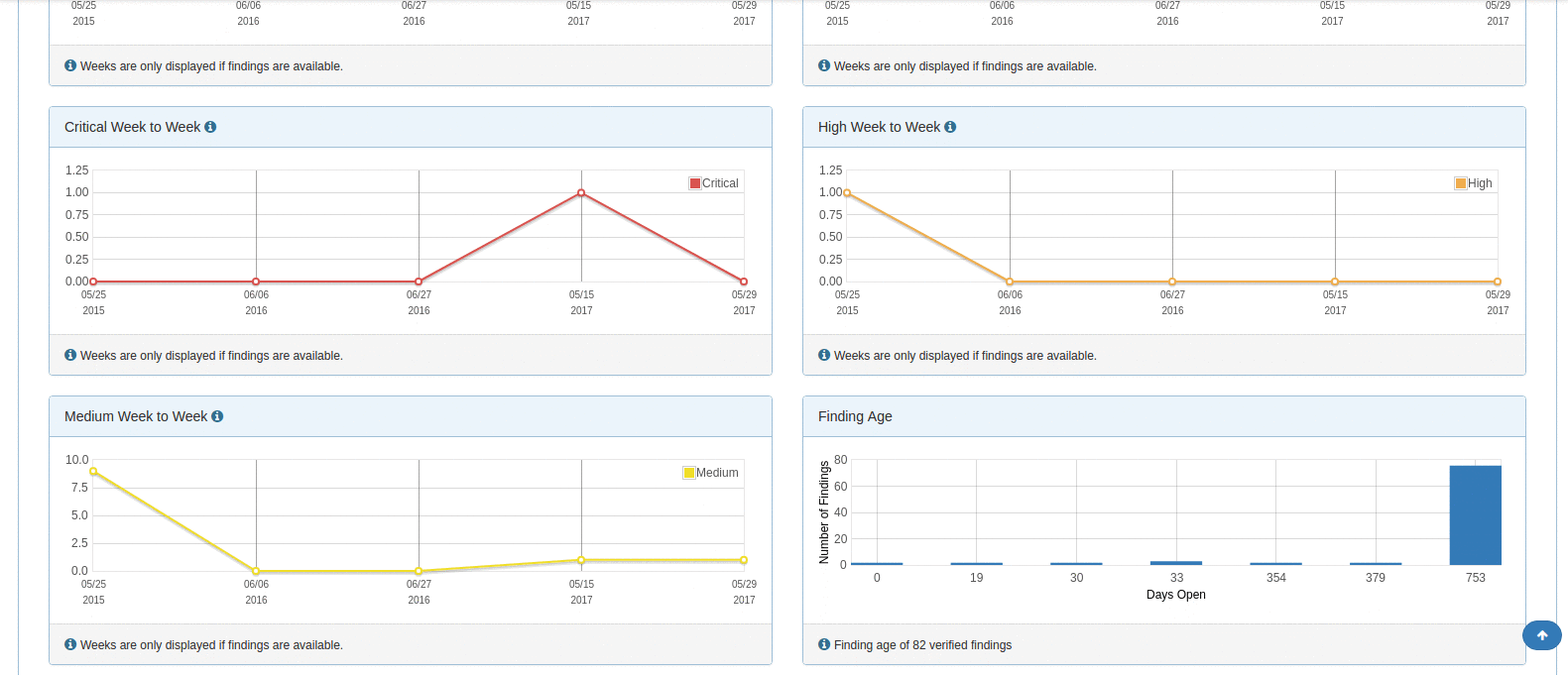
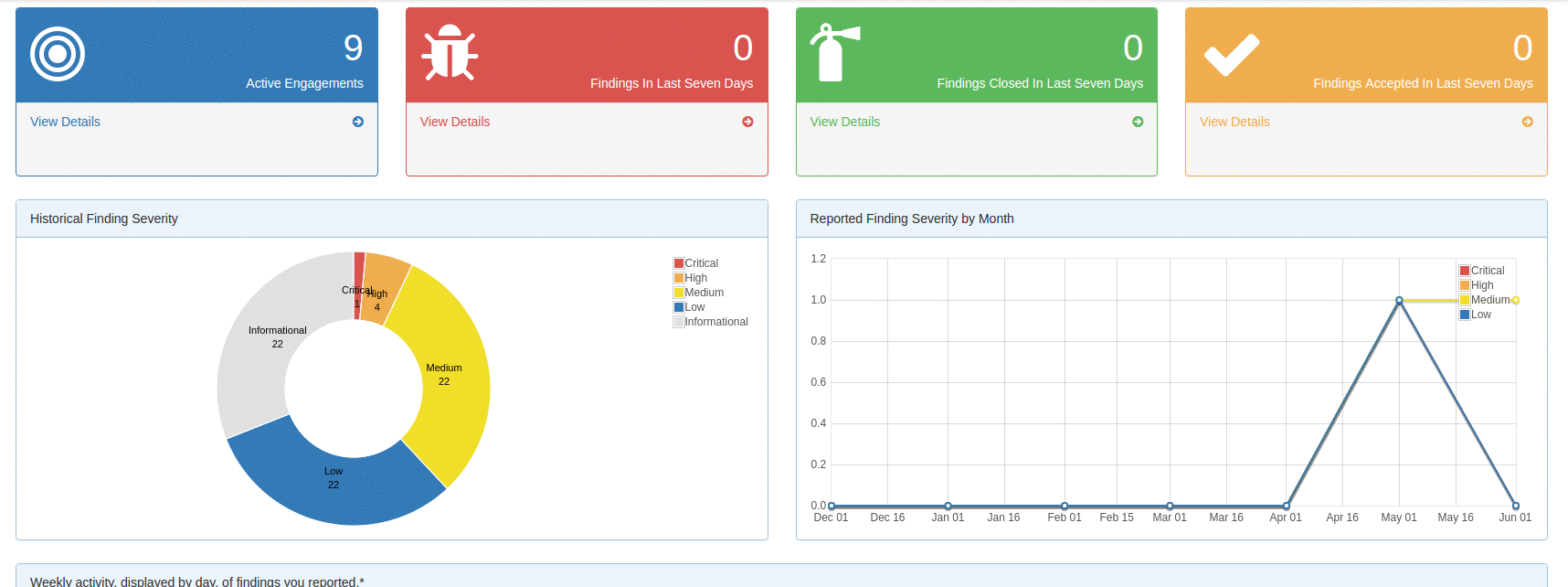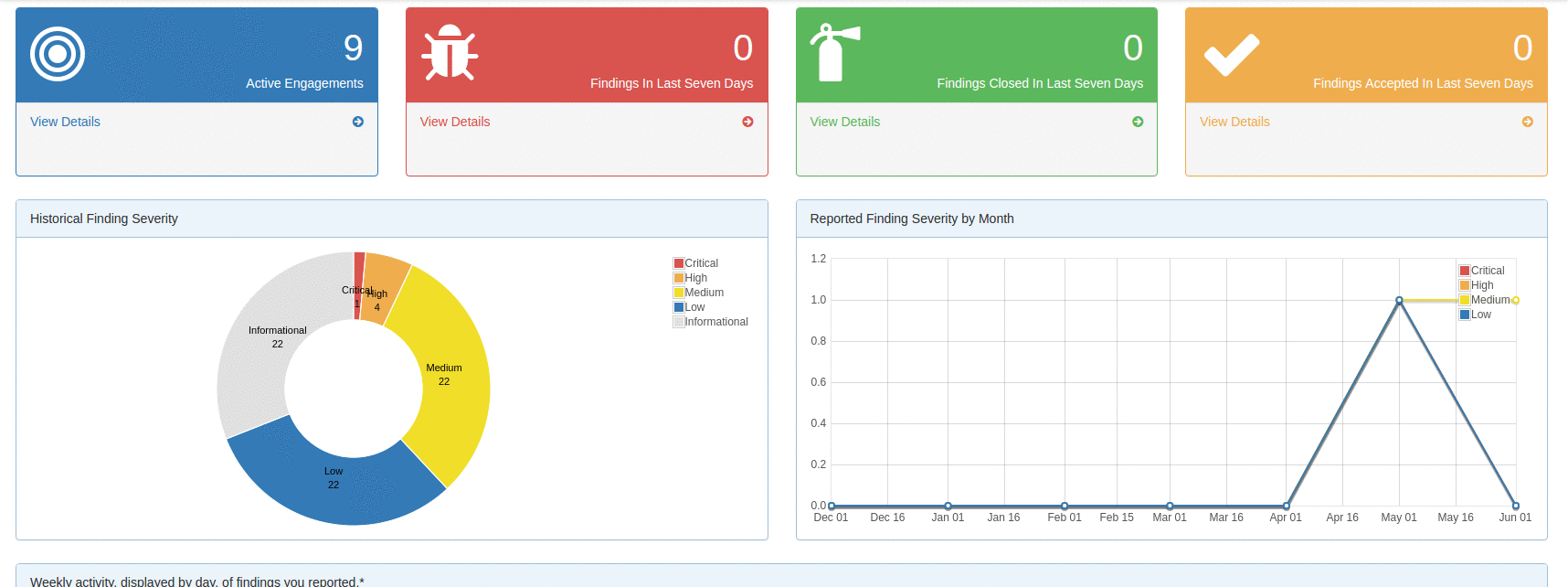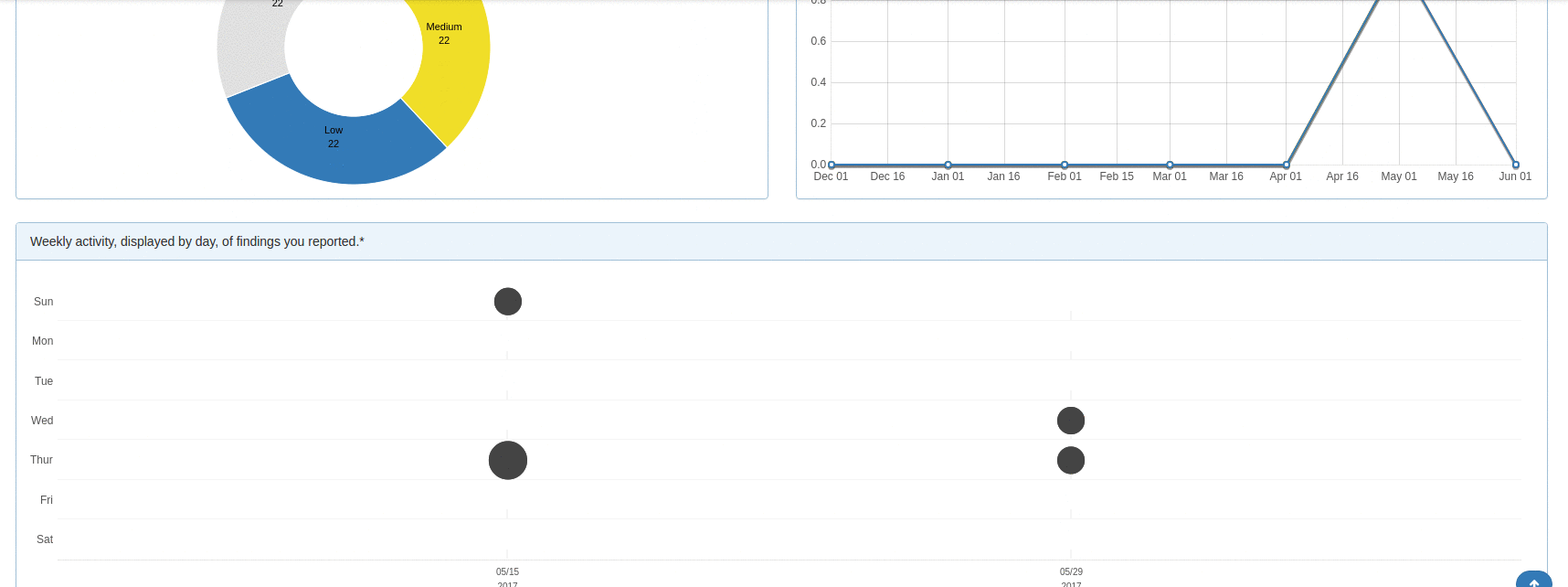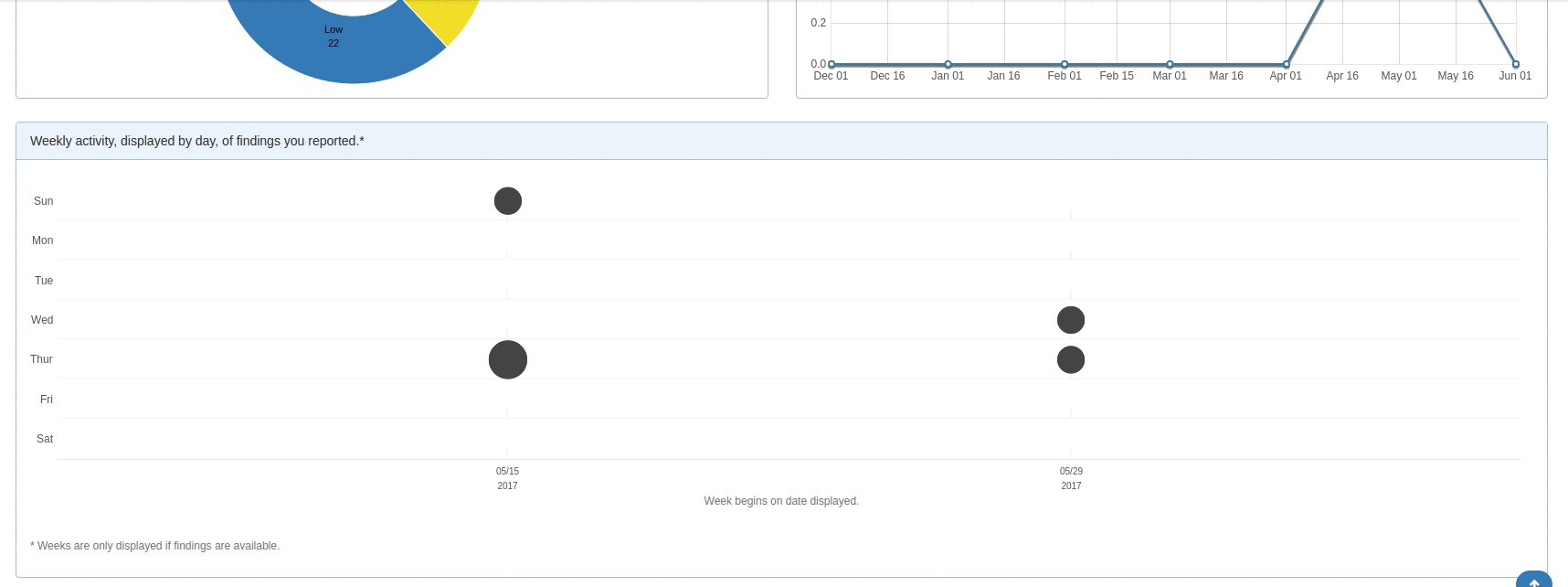
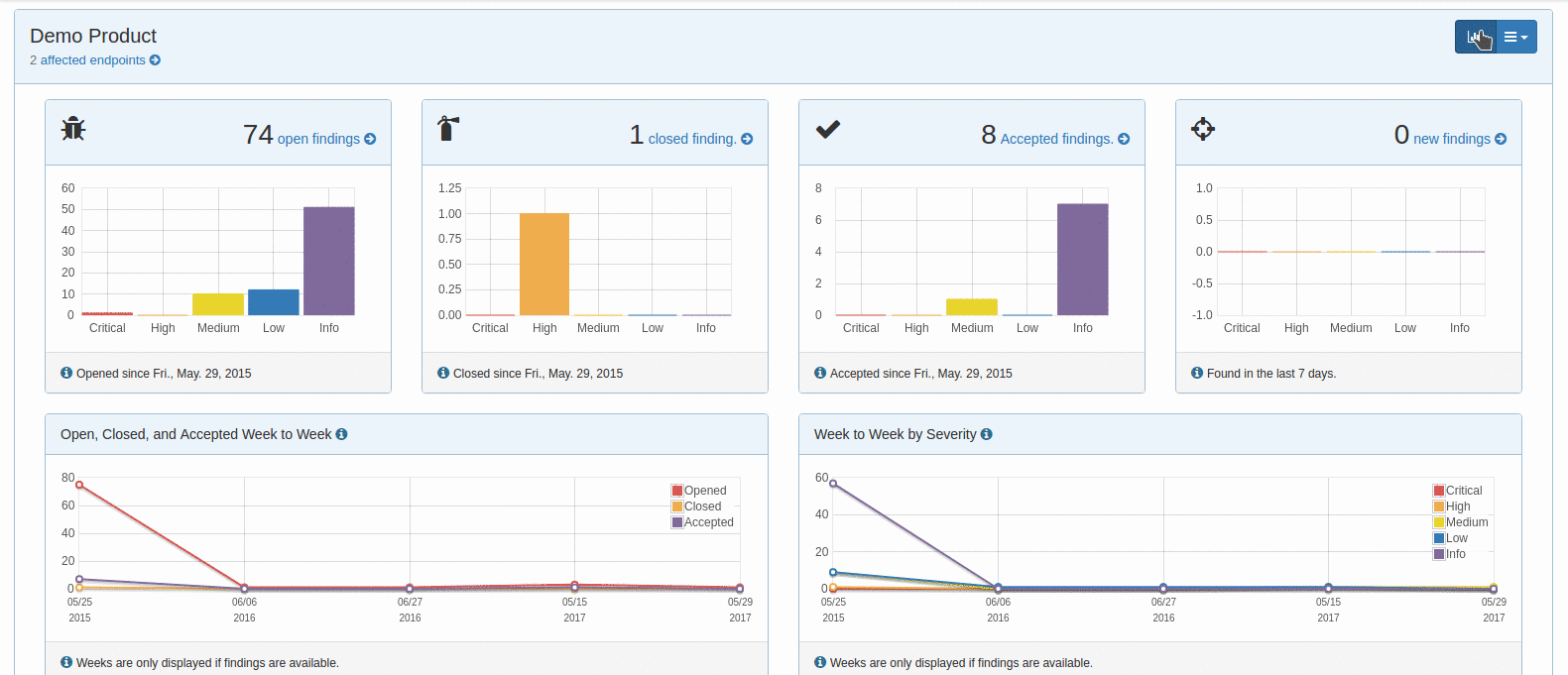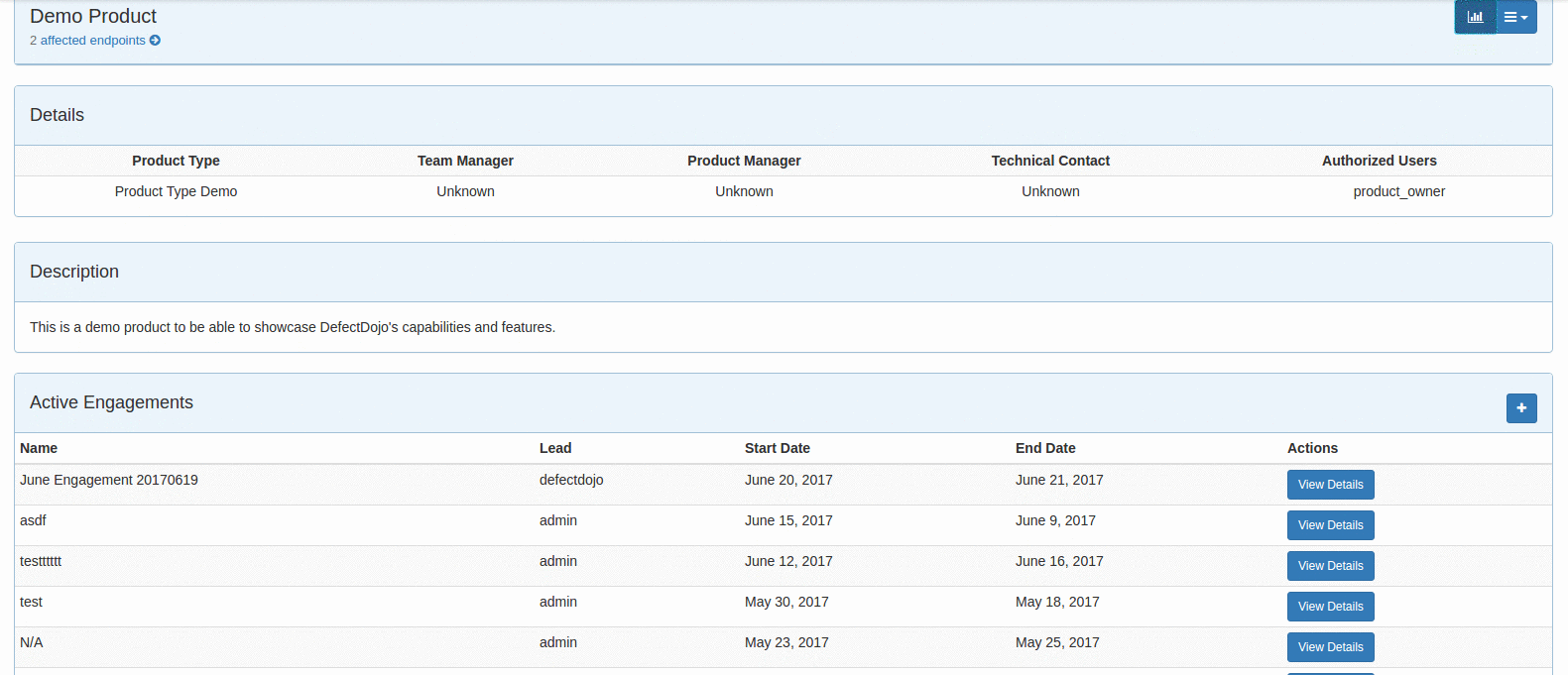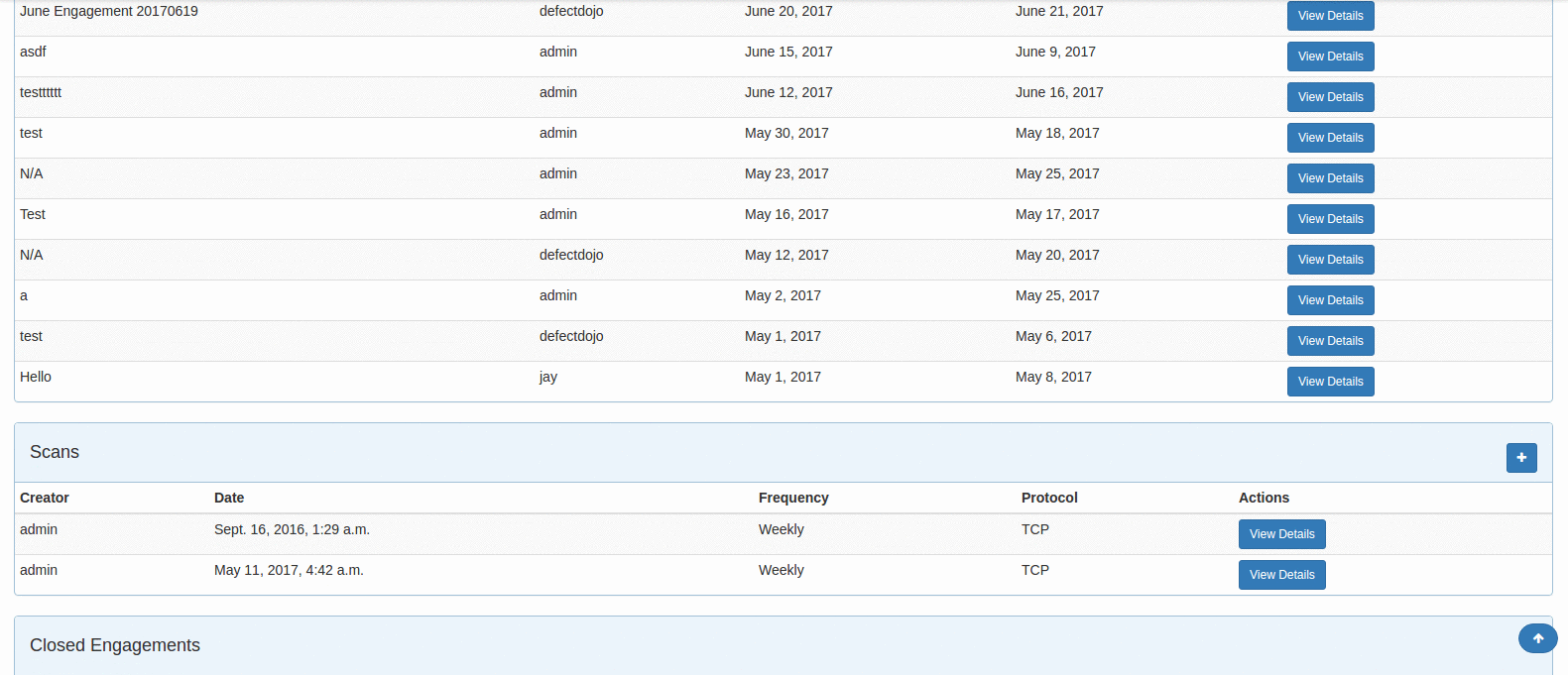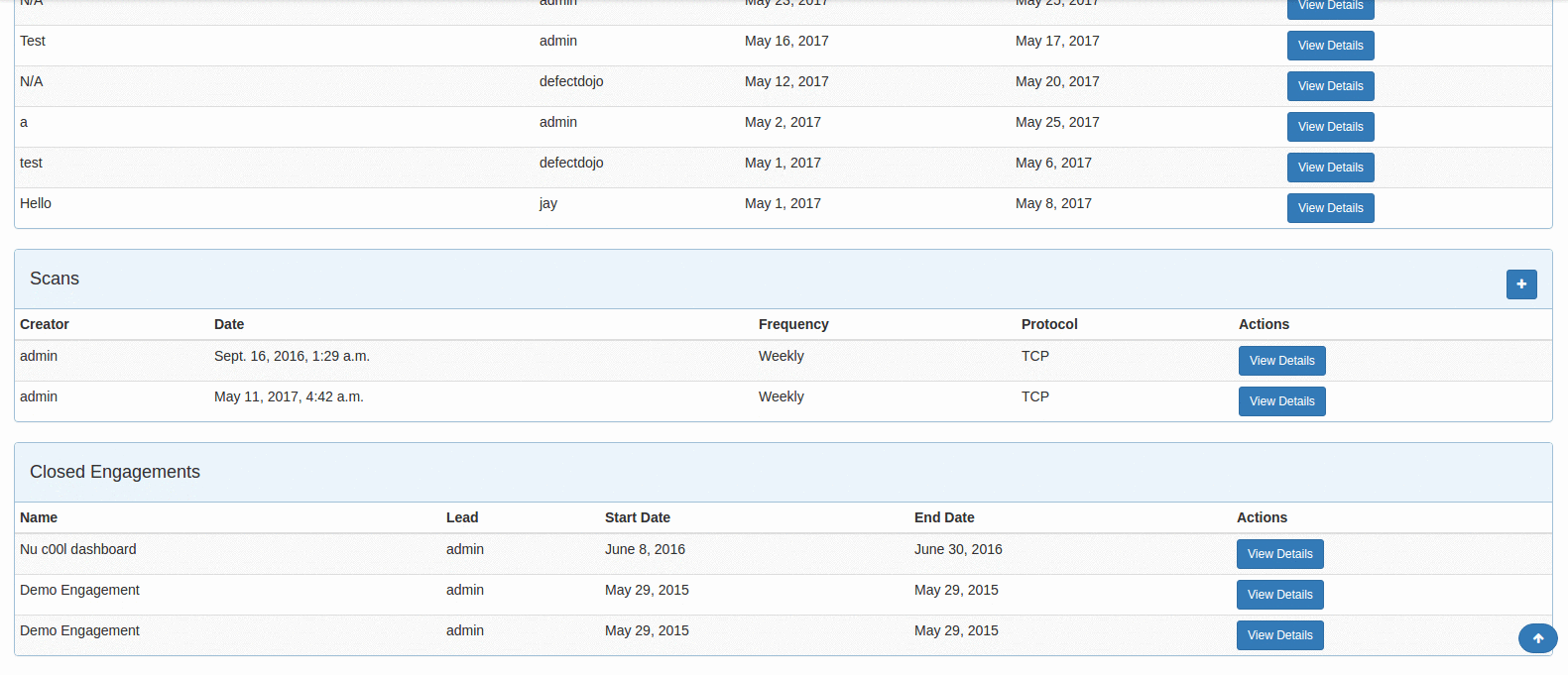
The DefectDojo dashboard gives you a summary and health check of your overall product security engagements. You can see the number of engagements that are currently taking place as well as vulnerability findings statistics for the past week.
These quick statistics can help you keep on top of recent findings, and ensure that the vulnerability count doesn't steadily creep on a weekly basis. There are also findings charts to track the severity of reported vulnerabilities by overall count and per month.
Adding Vulnerability Findings
A vulnerability 'finding' in an app or project can be added manually into DefectDojo so it can be tracked. Furthermore, in situations where you think there might be a vulnerability in an application, but you are not entirely sure if it's an issue (or needs more investigation), you can add it as a 'potential finding' where it can later be promoted to a verified finding if it is actually a security concern.
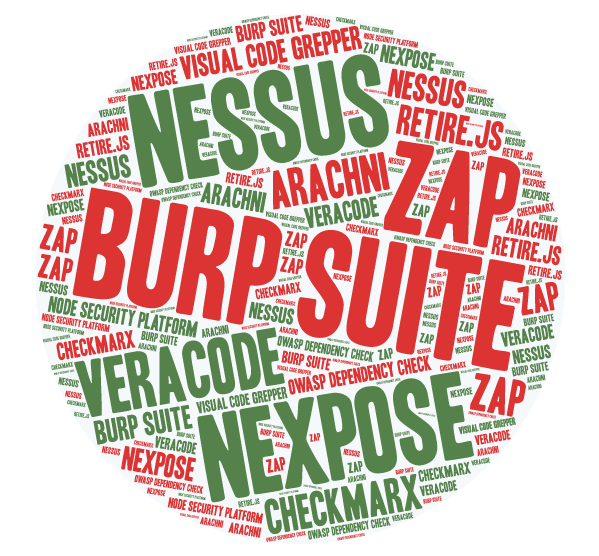
Along with manually adding vulnerability findings, DefectDojo allows you to import scan results using a number of penetration testing tools and scanners:
- Burp Suite (XML)
- Nessus (CSV, XML)
- Nexpose (XML)
- ZAP (XML)
- Veracode (XML)
- Checkmarx (XML)
- AppSpider (XML)
- Arachni Scanner (JSON)
- Visual Code Grepper (CSV, XML)
- OWASP Dependency Check (XML)
- Retire.js JavaScript Scan (JSON)
- Node Security Platform (JSON)
(There is also support for Qualys and Snyk scan imports coming soon.)
DefectDojo will parse the reports from any of the above penetration testing tools so you can have all your findings in the one place from multiple tools. The scanner consolidation feature will prevent duplicate findings being created by doing comparisons of previous findings to see if the issue has already been reported.
If you also want to add manual findings in a certain format or have a tool that outputs to CSV format, there is an option to import generic findings using the CSV import format.
Finding Templates
One repetitive task for any security engineer is having to re-explain/document re-occurring vulnerability types between applications or projects. To help save time writing the same information over and over, you can simply write a finding 'template'. With these templates, you can add information about a certain re-occurring vulnerability type to a base template, which can later be modified.
The key benefit here is the time saved when explaining common vulnerabilities. If a vulnerability needed to be manually explained each time for a different application or project, key information or explanation details can potentially be left out over time if an engineer begins to shorten down lengthy explanations.
Predefined templates will save not only a security engineer time, but it will also provide more detailed information for your popular vulnerability findings every single time.
Metrics
DefectDojo offers in-depth metrics across the board. Is very easy to see overview metrics across products, engagements, and individual scans. Furthermore, a lot of the pages allow you to see charts for the findings that are contained within tables in the user interface. This is a nice way to see a thorough visual representation of some specific findings data whether it's for an overall product or a subset of some scan findings.
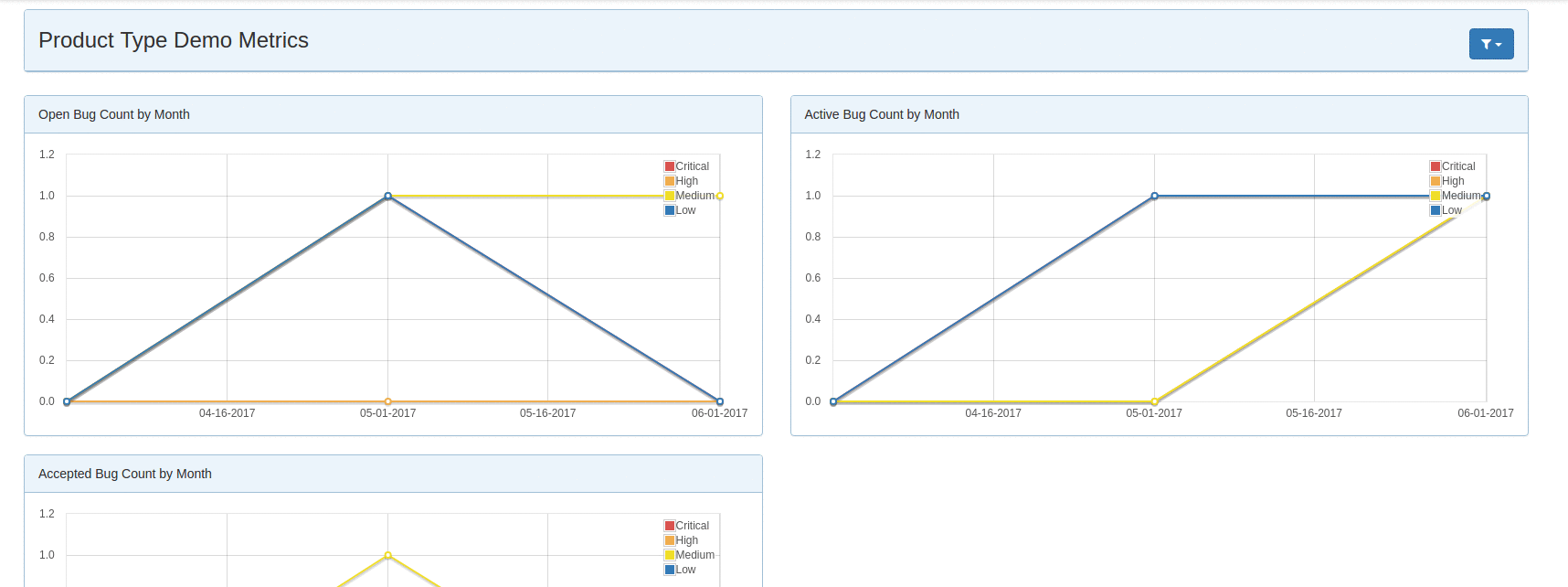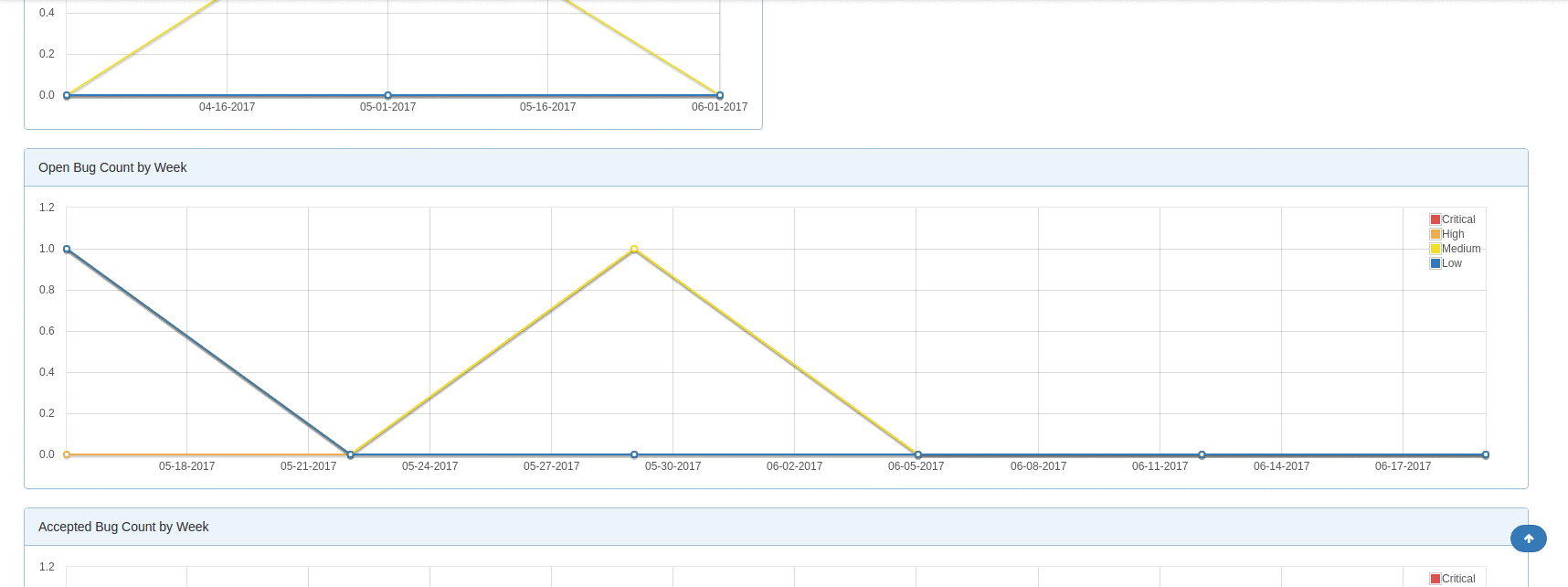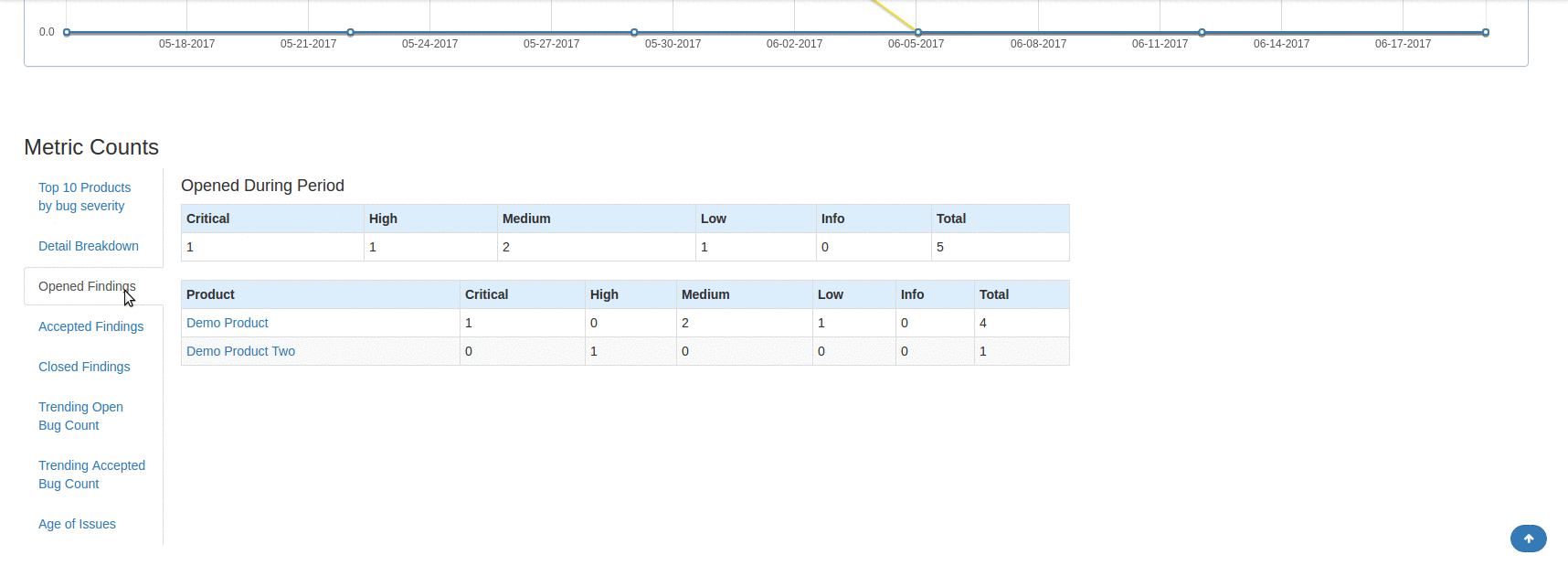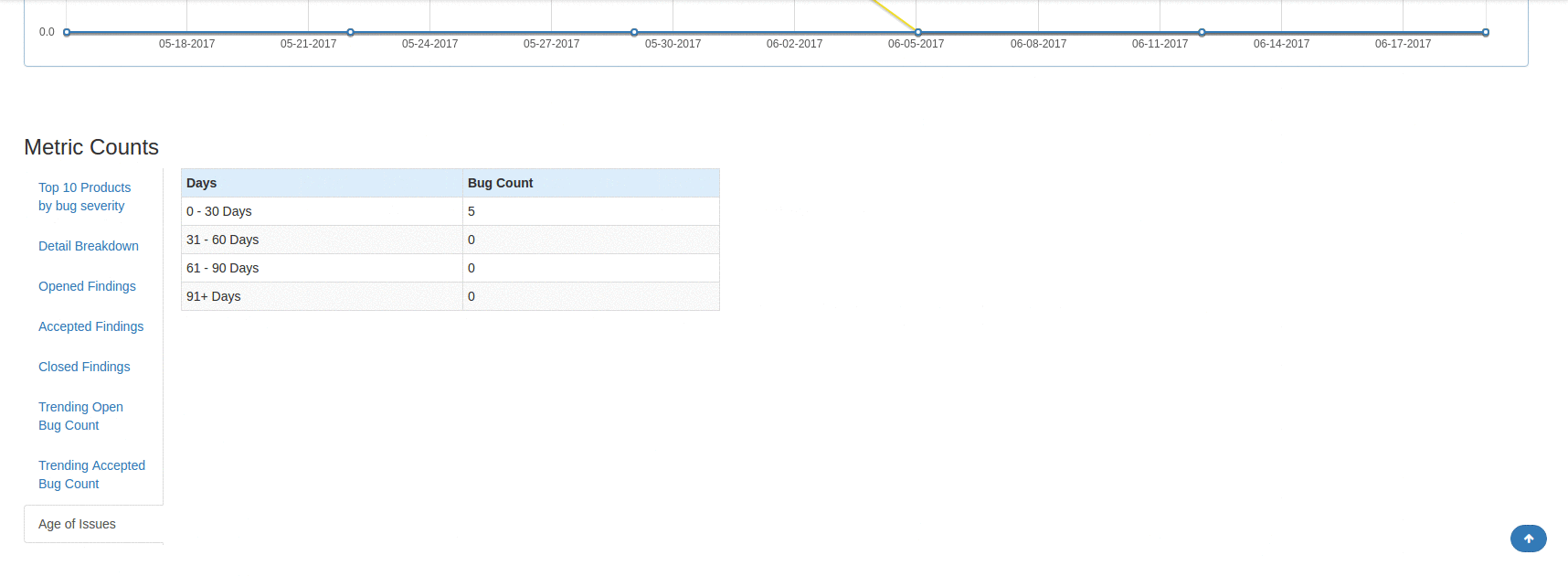
Reporting
One of the most powerful and time-saving features of DefectDojo is the reporting functionality. DefectDojo will allow you to generate reports from areas like individual scans, engagements, and products. These reports can be generated in either PDF or AsciiDoc format.

Furthermore, you can also generate tailored custom reports and use robust filtering to only document the vulnerability findings you want.
These custom reports allow you to choose what you want in the report. The report builder features an intuitive drag and drop system and allows you to include the following elements to make the report as detailed as you need it:
- Cover Page
- Table of Contents
- WYSIWYG Content
- Findings List
- Endpoint List
- Page Breaks
DefectDojo API
DefectDojo also features an API that can be used to interact with the solution. One of the most useful endpoints in the API is the importScan endpoint. This will allow you to import scan results directly into DefectDojo. This can be used to greatly enhance your security automation pipeline by automatically sending scan results from penetration testing tools to the DefectDojo API to be processed.
{
"minimum_severity": "", # Minimum Severity to Report
"scan_date": "datetime", # Date of the Scan
"verified": false, # Manually verified by tester?
"file": "", # The scanner output report file
"tags": "", # User defined tags/labels
"active": false, # Flaw active or historical?
"engagement": "", # Relevant Engagement
"scan_type": "" # Type of Scan. eg. Zap
}Scan Scheduling
As well as importing previous scan results from security tools; it also currently supports scheduling of port scans using NMAP from within the application itself. You can set up intervals of when to carry out these scans and be notified of the results via email. In the future, DefectDojo will be aiming to allow you to carry out scans using other tools from within the application and enhancing the integration ties between DefectDojo itself and the end security tools.
User Roles
Although a security engineer would primarily use this tool, other users can benefit from the insightful metrics delivered by DefectDojo. Users can be set up with limited access roles so they can only use certain functions inside the applications or view products/projects that have been authorized to them.
This is useful for allowing project managers to get quick oversights on the vulnerabilities affecting their products without the need for superuser permissions.
Jira Integration
DefectDojo also supports integration with Jira. You can create a new webhook in Jira to use this feature. Once configured correctly, you can push findings from DefectDojo into Jira. Also as an added bonus, the integration is bi-directional, so if an issue is closed in Jira, it will also be closed in DefectDojo etc.
Example Workflow
DefectDojo is designed to make tracking defects across products and engagements easy.
- The first recommended step in using DefectDojo is to create a Product Type. A Product Type can be used to group Products together.
- You can now create a new Product, which could be a project or standalone application.
- The next step is to create a new Test Type. These will help you differentiate the scope of your work. For example, you might have a Dependency Check Test Type or a Static Scan Test Type.
- Next, it would be a good idea to create new Development Environments. These are useful for tracking deployments of a particular Product.
- Once, we have the above items setup, we can add an Engagement. An Engagement captures the findings and details obtained in a certain amount of time. For example, it could list vulnerabilities found from a Nessus scan along with some notes about the assessment.
- When scan results are imported as part of an Engagement, you can then begin generating reports for the engagement or view the metrics for the assessment.
Summary
It's clear to see that DefectDojo does an excellent job of managing vulnerabilities across products and helps get the most out of your application security resources.
The simplified user interface generated reports and various metrics schemes allows non-security engineers to easily look into the findings without having to trawl through the verbose XML and JSON result files from various security tools.
From importing scan results to generating insightful reports within seconds, DefectDojo is a very useful tool that will be a notable time saver when it comes to tackling the chaos that is vulnerability management.
DefectDojo is readily available on GitHub at OWASP/django-DefectDojo.
Take advantage of your Red Hat Developers membership and download RHEL today at no cost.
Last updated: June 20, 2017