2016 was certainly an interesting year and, although we could probably discuss the election alone for an hour, there is one particular epidemic which has plagued the developer community in more ways than we probably care to mention. It seems as though even the best data encryption and reformatting of SSD’s is slowly becoming not enough when it comes to the continuous evolution of the hacker community and this is a pretty unsettling situation.
In fact, in the first six months of 2016, 550 million records were stolen making it 65 percent higher than the statistics from the previous year. If this data is not enough to shake you, 45 records are stolen every second and nearly 165k are stolen every minute. In 2016 alone, 45 percent of these data breaches hit businesses specifically in the IT and development sect. On top of this, no company is safe; In September of last year, Yahoo’s data was breached in one of the largest breaches in history. This was quickly followed by a data breach on the website Krebs on Security which had an attack power of 665 Gbps and, only one month later, the same Mirai Malware created by Anna Senpai attacked DNS service provider Dyn and reached a staggering attack power of 1.2 Tbps setting a new world record. With this said, it is slowly becoming more and more important that we recognize new trends in the way data is breached, determine how we can combat these data breaches, and look towards the future in order to find solutions to the problems 2017 may have in store for developers and their data alike.
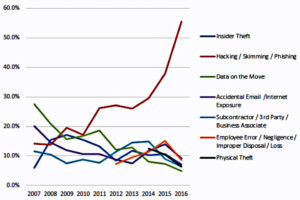
Manipulating Data Integrity and Taking Advantage of Poor Drive Disposal Techniques
Data breaches have reigned supreme when it comes to hackers for countless years, however, a new form of data intrusion may begin to take hold in 2017. In the past, data breaches have aimed to take sensitive data and share it with the world or use malware to infect connected devices and infiltrate the IoT, however, data manipulation is far more sly than that. With data manipulation, hackers aim to manipulate sensitive data in order to create chaos or gain benefits for themselves or the companies they secretly work for.
For instance, manipulated stock data could literally lead to millions of dollars lost in the blink of an eye whereas other hackers hip to this form of hacking may use it to steal and release personal data and create false data about leaders in our government and celebrities in order to damage their careers. With data manipulation, it could take years or even decades for this hack to reveal itself in some cases due to the fact that nothing is being stolen or leaked most of the time. Because of this, data integrity manipulation may just be the largest threat posed to major corporations and governments in 2017 and learning to combat it is truly the only way to stop it from gaining traction.
Although not as sneaky as data manipulation may be, hackers recently have been utilizing poor drive disposal to their advantage. Due to the growth inside SSD devices, reformatting SSD’s is simply not good enough to prevent a data breach from occurring. Although many companies have turned to IT Asset Disposition (ITAD) partners to try and combat this issue, it is still not as secure as many companies may think and data disposal may still be incomplete at the end of the process.
Similarly, Companies using data software which connects to the cloud, such as FileMaker Cloud, must be very careful about the way that they are sending encrypted data within the Cloud. In fact, countless cloud attacks in the last year cost multiple web development and IT companies some of their most crucial data and by using safe cloud techniques and encrypting data with quality data encryption software, you can avoid this in your own data analysis and ensure that your analytics are safe in the process.
The Pros and Cons of Outsourcing Your Data Security
Although it may be common to outsource your data erasure to an ITAD partner, the consequences of not looking into the quality of this vendor could quite literally mean a highly unnecessary and costly data breach for your company. When choosing an ITAD partner, you must keep in mind key factors such as their certifications, whether or not they check for and remove BIOS Freeze locks, and whether or not they store IT equipment somewhere safe before disposition. Furthermore, you must also think about whether they track IT assets in real-time to maintain records in order to ensure SSD’s are all accounted for and managed adequately as well as whether or not they discard SSD’s in an environmentally friendly way.
Once these questions have been answered, if everything appears to be in order, this information could be utilized to create a contract that holds your ITAD partner responsible for any data breaches that occur under their care.
Overreliance on Encryption Could Spell Disaster
Although the last few years of data security have focused on encryption primarily, there are many things to take into account about encryption which alter the amount in which we solely rely on it. For instance, because fully homomorphic encryption is not yet readily available to compute arbitrary functions over encrypted data without the decryption key, every time that we manipulate encrypted data, it is decrypted and this is where a cyber attack can easily occur.
However, by utilizing LUKS FDE supported by Red Hat Enterprise Linux, you can ensure that not only are your files protected but the temporary storage is likewise and you can encrypt all of your files instead of choosing which ones you want to encrypt and running the risk of forgetting one by accident. When utilizing LUKS Full Disc Encryption with Anaconda (XTS Mode), you also double your default key size likewise. The best way to protect your data from the constantly changing world of cyber attacks is simply by using a quality FDE, ensuring that your key management strategy is adequate, and implementing a two-factor authentication likewise.
How IoT, Botnets, and Security Automation and Orchestration Will Affect Data Security in 2017
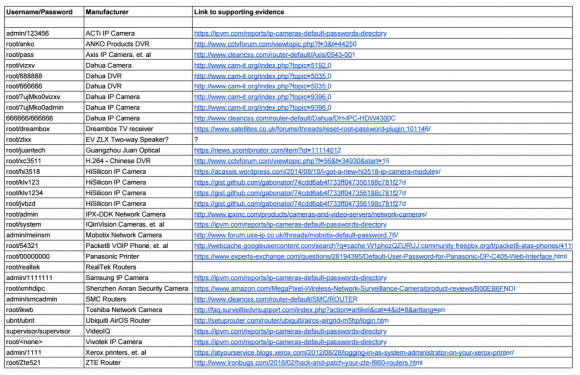
It has been predicted countless times in the last year that 2017 would be the year for IoT, however, this may not be a good thing entirely. In fact, although there are countless incredible breakthroughs in tech, including augmented reality, blockchain, edge analytics, and natural language processing, that have been made through IoT, there is a rising concern regarding cyber security that comes along with it.
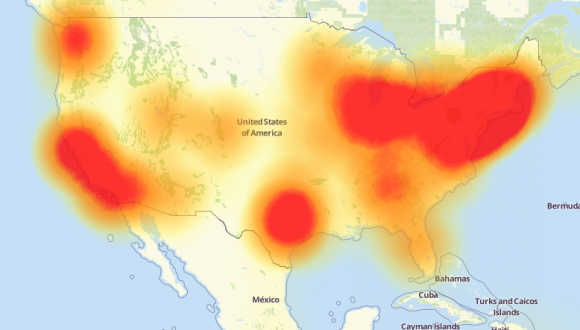
Because of the way that IoT transforms everyday life into a ‘fully functional computer network,’ so to speak, this opens up a whole new way for hackers to manipulate our world. In fact, last year alone, there were countless data breaches and hacks directed specifically towards IoT only raising the question of its safety even further. Similarly, with the DDoS attack on DNS provider Dyn which targeted weak security cameras and DVR's that used 68 factory set usernames and passwords to log into weak devices and infect them, the bar for this form of a cyber attack continues to raise. Because some of these connected ‘things’ become vulnerable, this can lead to the attack of others in its circle meaning the loss of one could mean the loss of many. For instance, some of the same infected devices from Krebs on Security's analysis of the Mirai Malware attack were found to be connected to the Dyn attack likewise proving that mass consumer technology such as AI, VR, AR, and Smart home and office devices are not only perfect targets with weak security as is but also happen to only become weaker as consumers tend to use extremely common and easily hackable usernames and passwords likewise.
Furthermore, with more and more IT and development companies using tools such as WebVR, CAVE, haptic gloves, project management programs, and AI technology, the need for security remains a major issue and our overreliance on encryption, reformatting SSD's, and sending files using steganography despite the countless hackers capable of decrypting these hidden messages is the sole cause.
On top of the question of security arising in the IoT, security automation and orchestration poses yet another threat. For instance, behavioral analytics, threat detection, and even the mere transfer of encrypted files can lead to massive data breaches and integrity manipulation. When managing projects and transferring encrypted files, these files become vulnerable and, without quality practices for compliance and security as well as partition encryption, the newest form of artificial intelligence may just lead to a series of ‘super hackers’ tearing apart and exposing any data in their path in the near future.
Lastly, through the transferring of files to external partners, these files can easily be manipulated or breached. However, by using SFTP and PGP encryption through a system such as Mule when transferring said files, you can ensure that these message payloads are compressed and encrypted to secure the sensitive information within them.
The Future of Data Security
Although this is not entirely certain, some individuals believe that Russia’s role in the election may have been in the form of a data security breach. Therefore, many believe that the future of data security may be through the manipulation of government data, in particular. Although rather subtle, this type of data manipulation could alter the future of our nation and quite literally manipulate history as well.
Furthermore, with artificial intelligence and robotics becoming more advanced every year, some speculate that hacking may soon be even more digitalized than it already is. In fact, these same individuals believe that robots and AI’s will take over the hacking aspect of data breaches in the near future making it even more difficult to trace the steps of these cyber attackers. Furthermore, many speculate that the Dyn outages prove that malware via botnets may become more serious than ever before and the inclusion of weak devices in the IoT is the primary cause.
Lastly, with the IoT becoming more and more prevalent each year, some IT professionals predict that this connection of our world could lead to the hacking of countless devices including self-driving cars, stoplights and water systems, airplanes, and even, with time, nuclear weapons. This fear has only been perpetuated with disasters such as Gmail accounts being compromised by Samsung smart refrigerators and hospital IT networks being hacked into through vulnerabilities in medical devices.
The only way to stop these types of data breaches from occurring is simply through taking the preventative actions and security measures necessary to not simply assess the situation once it occurs but rather prevent it from ever occurring in the first place. From there, the SFTP transferring of files, reformatting of SSD’s, use of the IoT securely, and FDE of sensitive data will, at last, be good enough for companies, developers, and IT professionals alike.
Last updated: September 19, 2023