Today’s modern infrastructure faces the complex challenge of managing user’s access to the resources. To protect system and data integrity, companies have implemented identity and access management (IAM) solutions for their in-house systems. IAM solutions address three major concepts: identity, authentication, and authorization. Their job is to ensure that only authenticated and authorized users have access to resources or information. Every IAM solution on the market provides a great set of features such as:
- Single Sign-On (SSO)
- Centralized policy-based authentication and authorization
- Identity federation
Sweet!! But what is the challenge here?
In the past, it was simply a matter of which users had access to which systems. Today there are multiple applications running on multiple devices that are accessing data and systems on behalf of users. There is pressure to provide APIs (such as RESTful interfaces) to all systems for agility, and to enable business process automation. As a result, it has become nearly impossible for organizations to understand which apps are accessing which resources and to provide comprehensive access controls. Fortunately, API management technology is available to provide:
- Security and authentication (API key, OAuth2.0, etc.)
- Rate limiting and throttling policies
- Monitoring and analytics
- Metering and billing (monetization)
- Developer experience (Content Management System)
- and more..
3scale by Red Hat is Red Hat's API management platform.
Some may consider IAM and API management to be separate solutions in separate domains. While each does serve a unique purpose, in my view, there is an overlap where access by client applications are concerned. See the following illustration:
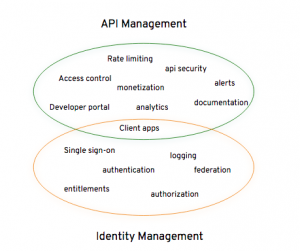
There are many Identity Providers (IdP) in the market (Red Hat Single Sign-On, Forgerock, Ping Identity, Auth0, Okta, etc.). The challenge is integration between these IdPs and an API management solution. 3scale by Red Hat, with its pluggable and scalable architecture, can easily integrate with the popular IdPs. This is my motivation to start this series of blog articles on 3scale by Red Hat integration with several different IdPs.
Below are few resources that will help you to better understand OpenID connect (OIDC) and JSON Web Token (JWT):
- OpenID connect explained
- Overview of OpenID connect
- OpenID connect core specification
- RFC 7519: JSON Web Token
Let’s dive into the technical details.
To stay consistent throughout the series, I'll stick to one use case to see how every IdP can be integrated using 3scale by Red Hat.
Use case
- A company we'll call Acme, has a subscription backend API endpoint that provides the subscriptions status for products to customers. They would like to expose the endpoint to customers, but want to do it in a secure fashion.
- Acme would like to use an existing identity provider, and use the issued token to control access.
Details
Acme would like to identify the users using OIDC and generate a JWT token:
- The JWT will be used for the API calls. The backend will extract the JWT, extract the user profile, pull the subscription information, and send back the API response.
- To complete the handshake, we will be using OAuth2 Implicit Grant flow.
Architecture
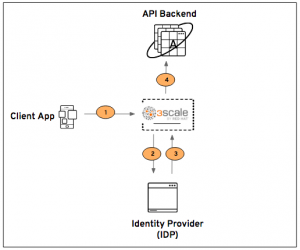
- The Client App sends an authorize request to 3scale by Red Hat.
- The 3scale (API manager and API gateway) communicates with the IdP.
- The IdP authenticates and authorizes the user. It then generates a JWT for the API back-ends to consume.
- The API back-end (the resource server) extracts the JWT and sends back a successful response.
For more information, see the tutorial written by Hugo Guerrero, "HOW-TO setup 3scale OpenID Connect (OIDC) Integration with RH SSO".
Red Hat Single Sign-On (RHSSO) is a certified OpenID Connect provider (source).
The next article in this series will demonstrate how to integrate 3scale by Red Hat and Forgerock with the above use case.
Last updated: September 3, 2019