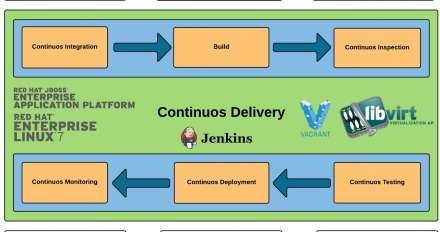
Using .NET Core in a "Disconnected" Environment
For added security, .NET Core applications that require access to external libraries can be run in a disconnected environment (one without internet access). Here's how.

For added security, .NET Core applications that require access to external libraries can be run in a disconnected environment (one without internet access). Here's how.

Red Hat Summit 2018 will focus on modern application development. Securing your applications and services is a critical part of modern applications. At Red Hat Summit 2018 developer-oriented sessions learn how to secure your applications and services, integrate single-sign on, and manage your APIs.

In this article, we’ll demonstrate how Red Hat Mobile v4 and OpenShift v3 enable customers to rapidly deploy and secure their mobile applications by integrating with a third party product provided by Intercede. We’ll be using Intercede’s RapID product to enable two-way TLS.

In a few weeks, the Fast Datapath Production channel will update the Open vSwitch version from the 2.7 series to the 2.9 series. This is an important change, a wealth of new features and fixes all related to packet movement will come into play.

This article walks through a list of recommended build flags for when you compile your C or C++ programs with GCC. Do you know which build flags you need to specify in order to obtain the same level of security hardening that GNU/Linux distributions such as Fedora and Red Hat Enterprise Linux use?

This article shows Redhat 3Scale integration with ForgeRock using OpenID Connect. We will show how to integrate ForgeRock with 3scale by Red Hat. ForgeRock is one of the popular and growing identity management companies.

Following is a diverse set of developer-related breakouts, workshops, BoFs, and labs for Red Hat Summit 2018. With these 61+ sessions, we believe that every attending application developer will come away with a strong understanding of where Red Hat is headed in this app dev space.

how to secure and connect JBoss AMQ7 Brokers with SSL

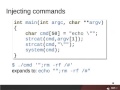
(Part 2)Learn about recommended practices for producing secure code with input validation in part one of this four-part video series.

Learn how to start adopting a security-like mentality, also known as the "security mindset" in part four of this four-part video series.

Learn how to start adopting a security-like mentality, also known as the "security mindset" in the first half of part four in this four-part video series.

Learn about authorization such as user privileges, levels of access, and how they're different in part three of this four-part video series.

Learn about numeric errors and the dangers of using incorrect data types in part two of this four-part video series.

(Part 1)Learn about recommended practices for producing secure code with input validation in part one of this four-part video series.




Keycloak is a new open source authentication server for cloud, mobile and html5. With loads of features, including single-sign on, social login, account management console, account workflows, fully featured admin console, OAuth2 and OpenShift cartridge to name a few. The first alpha has recently been released, with loads more features planned for the future. Keycloak also provides support for role based authorization and supports granting access to third party applications. This talk gives a comprehensive introduction to Keycloak and its features, as well as discuss how easily you can add authentication to your applications. There will also be an extensive live demo. Stian Thorgersen is a Senior Software Engineer at Red Hat. He co-leads the Keycloak project together with Bill Burke, and is also the security lead on another new open source project. Stian also has many years of experience in cloud solutions.