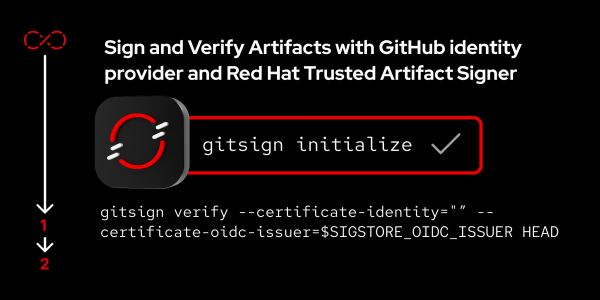
Overview: Sign and Verify Artifacts with GitHub identity provider and Red Hat Trusted Artifact Signer
The goal of this learning exercise is to explain how to set up Red Hat Trusted Artifact Signer (RHTAS) with GitHub as a federated OIDC provider. To achieve this, we'll leverage Red Hat SSO's ability to federate authentication to a third party provider (GitHub). Such a workflow enables you to use tools that you are already using to fortify your CI/CD pipelines with keyless signing.