Serhei Makarov
Serhei Makarov's contributions
Article
How to trace application errors using SystemTap
Serhei Makarov
Discover why the Linux kernel returns an errno code using SystemTap and how to use the whythefail.stp script in this demonstration.
Article
Detecting nondeterministic test cases with Bunsen
Serhei Makarov
A short Python script can identify tests that might break CI/CD pipelines because they return different results on identical runs. Learn more.
Article
Automating the testing process for SystemTap, Part 2: Test result analysis with Bunsen
Serhei Makarov
Once you've run your tests and collected the results, you need a way to store and analyze them—and that's where the Bunsen toolkit comes in.

Article
Automating the testing process for SystemTap, Part 1: Test automation with libvirt and Buildbot
Serhei Makarov
Find out how the SystemTap development team used libvirt and Buildbot to develop an automated testing system that accommodates nondeterministic test cases.

Article
Installing debugging tools into a Red Hat OpenShift container with oc-inject
Serhei Makarov
This article describes the oc-inject utility, which works on any Linux system that includes Python 3, the ldd utility, and the Red Hat OpenShift command-line tool oc.
Article
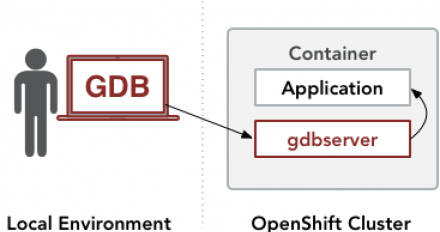
Debugging applications within Red Hat OpenShift containers
Serhei Makarov
To successfully debug a containerized application, it is necessary to understand the constraints and how they determine which debugging tools can be used.

How to trace application errors using SystemTap
Discover why the Linux kernel returns an errno code using SystemTap and how to use the whythefail.stp script in this demonstration.

Detecting nondeterministic test cases with Bunsen
A short Python script can identify tests that might break CI/CD pipelines because they return different results on identical runs. Learn more.

Automating the testing process for SystemTap, Part 2: Test result analysis with Bunsen
Once you've run your tests and collected the results, you need a way to store and analyze them—and that's where the Bunsen toolkit comes in.

Automating the testing process for SystemTap, Part 1: Test automation with libvirt and Buildbot
Find out how the SystemTap development team used libvirt and Buildbot to develop an automated testing system that accommodates nondeterministic test cases.

Installing debugging tools into a Red Hat OpenShift container with oc-inject
This article describes the oc-inject utility, which works on any Linux system that includes Python 3, the ldd utility, and the Red Hat OpenShift command-line tool oc.

Debugging applications within Red Hat OpenShift containers
To successfully debug a containerized application, it is necessary to understand the constraints and how they determine which debugging tools can be used.
