Nicolas Massé's contributions
Article
How to size your projects for Red Hat's single sign-on technology
Nicolas Massé
Follow this tutorial to size your single-sign on project. Learn how to design benchmarks and assess performance to develop an more precise estimate.

Article
Using Podman Compose with Microcks: A cloud-native API mocking and testing tool
Nicolas Massé
Get a quick introduction to Microcks—a cloud-native API mocking and testing tool—and find out how to use it in deployable containers with Podman Compose.
Article
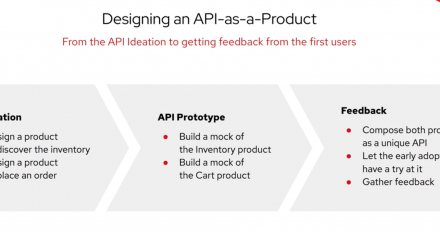
APIs as a Product: Get started in no time
Nicolas Massé
In this article, we show how to quickly get started with APIs as a Product using the new features of Red Hat 3scale API Management 2.7.

Article
APIs as a Product: Get the value out of your APIs
Nicolas Massé
Designing APIs as a Product means changing the way you craft APIs and shifting your mindset from packaging existing services to fulfilling customer needs.

Article
Using the 3scale toolbox Jenkins Shared Library
Nicolas Massé
Nicolas Massé continues the series on using the 3scale toolbox with an introduction to the Jenkins Shared Library.

Article
Deploy your API from a Jenkins Pipeline
Nicolas Massé
In this article, Nicolas Massé shows how to use the 3scale toolbox to deploy your API from a Jenkins pipeline.

Article
3scale toolbox: Deploy an API from the CLI
Nicolas Massé
This article covers the installation and use of 3scale toolbox, as a powerful basis for deploying your API from a CI/CD pipeline.
Article
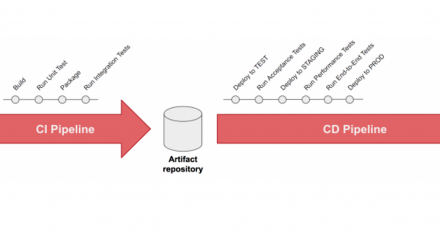
5 principles for deploying your API from a CI/CD pipeline
Nicolas Massé
In this article, Nicolas Massé covers the overarching principles and key steps for deploying your API from a CI/CD pipeline.

How to size your projects for Red Hat's single sign-on technology
Follow this tutorial to size your single-sign on project. Learn how to design benchmarks and assess performance to develop an more precise estimate.

Using Podman Compose with Microcks: A cloud-native API mocking and testing tool
Get a quick introduction to Microcks—a cloud-native API mocking and testing tool—and find out how to use it in deployable containers with Podman Compose.

APIs as a Product: Get started in no time
In this article, we show how to quickly get started with APIs as a Product using the new features of Red Hat 3scale API Management 2.7.

APIs as a Product: Get the value out of your APIs
Designing APIs as a Product means changing the way you craft APIs and shifting your mindset from packaging existing services to fulfilling customer needs.

Using the 3scale toolbox Jenkins Shared Library
Nicolas Massé continues the series on using the 3scale toolbox with an introduction to the Jenkins Shared Library.

Deploy your API from a Jenkins Pipeline
In this article, Nicolas Massé shows how to use the 3scale toolbox to deploy your API from a Jenkins pipeline.

3scale toolbox: Deploy an API from the CLI
This article covers the installation and use of 3scale toolbox, as a powerful basis for deploying your API from a CI/CD pipeline.

5 principles for deploying your API from a CI/CD pipeline
In this article, Nicolas Massé covers the overarching principles and key steps for deploying your API from a CI/CD pipeline.
