Part 1 of 2
"Docker is about running random crap from the Internet as root on your host" - Dan Walsh
Do you trust your containers?
In container-based development flows, a developer will create an image to be the base for an application. Images are stateless, read only, and they are built in layers. These layers represent everything in an application's runtime environment but the kernel, which will be “borrowed” from the hosting machine. Such layers include distribution, packages, environment, and additional configurations. It is not uncommon to see images on the Docker hub using wget to grab random stuff off the Internet to make up some of these layers.
This represents a paradigm shift over the pre container world where there was a clearer line between developers writing application code and IT specialists taking care of package upgrades. Can we trust developers to use only good packages? When the next Heartbleed is discovered will there be someone monitoring CVE streams to make sure packages are updated in a timely manner? What if the developer leaves the company?
One solution is to use a container registry from a trusted authority. Red Hat's container registry, for example, provides secure base images and removes the above concern. However, in order to have containerized applications with any value, a developer must create his own Images on top and distribute them somehow.
How can we check a given Image for compliance?
How do we even define such compliance?
Introductions to OpenSCAP and ManageIQ
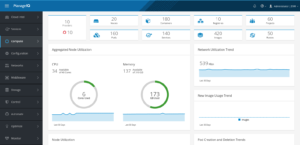
ManageIQ, the open source project that powers Red Hat's CloudForms, is a hybrid cloud management platform.
Cloud management platforms are used by organizations to control complex environments composed of nodes coming from multiple sources including traditional virtualization, private and public clouds, containers and much more. ManageIQ supports container providers including OpenShift and Kubernetes.
OpenSCAP is free software Implementation of SCAP: The Security Content Automation Protocol.
SCAP is a NIST authored set of standards. Combined together, these standards allow for:
- Naming systems components such as Operating Systems, Packages, and configurations.
- Defining possible Vulnerabilities (CVE) and Weaknesses (CWE) against those systems.
- Defining checklists (‘Content’) on systems against Vulnerabilities and Weaknesses.
With these components and content from a trusted source, we can now look at one system or a complete environment and say if they are compliant or not.
SCAP is trusted & used by many organizations including the US government & military.
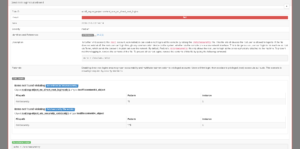
(This Result HTML produced by OpenSCAP is derived from an ARF result, part of the SCAP standard. For a specific vulnerability, it includes a severity, description, rational, links to online content definitions and even a Remediation script. This example checks that root login is disabled on a system.)
In the next part of this blog post, we will demo using ManageIQ’s Smart State Analysis to introspect container images and view SCAP results for them. We will then go further, and use the Control subsystem of ManageIQ, see how the system can monitor compliance for us, and even take authoritative action when a predefined baseline is not met.
Reference
- OpenScap Acronyms
https://www.open-scap.org/resources/acronyms/
You can read more about the Red Hat OpenShift Container Platform which is also available for download.
Last updated: August 24, 2023