Part 2 of 2
In part one of this blog post, we mentioned a pain point in Container based environments. We introduced SCAP as a means to measure compliance in computer systems and introduced ManageIQ as a means of automating Cloud & Container based workflows.
Tutorial: Using the OpenSCAP integration in ManageIQ
In ManageIQ we have been working on leveraging OpenSCAP to show container images that infringe known vulnerabilities based on the latest CVE content distributed by Red Hat. Integrating with ManageIQ’s “Control” subsystem allows defining workflows & compliance based on SCAP results. The integration was first introduced in the Darga release of ManageIQ and improved for the coming Euwe release.
ManageIQ has a mechanism for introspecting its objects - VMS, Hosts, Container Images, and much more. When running Smart State Analysis on container images, scanning containers are created on the target provider. The container Image being inspected is pulled, mounted, and analyzed for Vulnerabilities. Cluster Load is taken into account.
We will show two flavors of this integration:
- Run one scan and view result
- Full blown integration with ManageIQ ‘Control’ subsystem for a container provider
This tutorial requires a running ManageIQ instance that has a container provider. If you do don’t have such an environment but you would like to install one take a look at this link. An offering of a free test OpenShift cluster is also available at Openshift. For both, make sure your ManageIQ appliance has the ‘smartproxy’ and ‘smartstate’ roles enabled:
- Navigate to “Configuration -> Server:EVM”.
- Make sure “SmartState Analysis” and “smartproxy” roles are enabled.
Run one scan and view results:
- Navigate to “Compute” -> “Containers” -> “Container Images”.
- Select images to scan & press “Configuration” -> “Perform SmartState Analysis”.
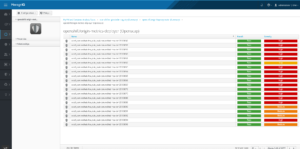
That’s it! You can now follow the scan status under “Tasks” -> “All VM And Container Analysis Tasks”. Upon completion you can view the results under the Container Image screen:
OpenSCAP results for an image, we also provide the standard OpenSCAP HTML as well as a failure summary.
Full blown integration with ManageIQ ‘Control’ subsystem for a container provider
- In ManageIQ go to Compute -> Containers -> Providers.
- Select providers -> Policy -> “Manage Policies”.
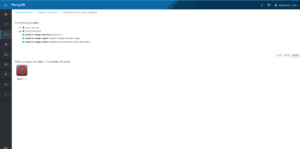
- Select the out of the box “OpenSCAP profile” & press apply changes.
- Go To “Configuration” -> “Schedules” -> “Add a new Schedule” and add a daily scan of all containers from a certain provider.
The default OpenSCAP profile.
That’s it! From this point on:
- New Images discovered will automatically be scanned.
- All provider Images will be scanned daily (with cluster load considerations in mind).
- Images with high severity failures will be marked as non-compliant.
- If a non-compliant image came from OpenShift, we will attempt to label it as non-secure and prevent its execution. This step requires additional configuration in OpenShift.
Using ManageIQ’s ‘Control’ system the sky is the limit: It is possible to define additional policies that would be executed once a compliance check failed or succeeded. It is possible to copy the ‘OpenSCAP Profile’ and create new profiles based on that. For example, a user can choose to define all images with ANY severity failure as non-compliant creating a very hardened system.
Reference
- OpenScap Acronyms
https://www.open-scap.org/resources/acronyms/
You can read more about the Red Hat OpenShift Container Platform which is also available for download.
Last updated: August 28, 2023