In my role as a Technical Marketing Manager at Red Hat, I take every opportunity I get to use our products and tools in the same way that we recommend a customer to use them. With that in mind, as I prepare to talk to people and demo Red Hat Lightspeed (formerly known as Red Hat Insights) and specifically the Red Hat Lightspeed compliance service, I need a number of Red Hat Enterprise Linux (RHEL) systems to be evaluated for regulatory compliance to a policy like Center for Internet Security (CIS) Level 1 Server.
To set this up, I used to build the RHEL servers. I’d configure the disks, set host names, install packages, adjust settings, then run a scan using the Red Hat Lightspeed compliance service.
After reviewing the scan, I would evaluate the results to see what I could quickly fix through Red Hat Lightspeed built-in playbooks, and then run a new scan. I’d repeat this process several times until I got the system into the state I wanted it. For a demo I wanted a few systems with a high pass rate - 95+% compliant and a few systems in need of some work.
This took me hours. I automated some of this, but I didn’t do it frequently enough to really worry about a repeatable build. That is, until I needed to build new systems with a new operating system version. For example, I had RHEL 8 systems and I needed to get to RHEL 9. I’m going to need to do this again soon with RHEL 10. I could upgrade, but for a variety of reasons I wanted to rebuild.
This iterative process is very similar to how customers perform their own "change-test-repeat" iterations to reach a final, self-validated standard gold image. This often involves multiple members within an organization providing review and sign-off. There has to be a simpler and easier way to create a compliant image.
And of course, there is.
Red Hat Lightspeed image builder includes the capability to create images that are compliant to a wide set of regulatory policies and frameworks.
Using Red Hat Lightspeed image builder
First, log in to the Red Hat Hybrid Cloud Console and find the Image Builder tile. Click the Images link (Figure 1).
Note: If you don’t see an Image Builder tile as shown, you might need to click the Add widgets button in the upper right and add it. Alternatively you can search from the menu at the top.
In the Image Builder screen, click the Create image blueprint button to launch a wizard to create a new blueprint. In the Security step of this wizard, you can type in an OpenSCAP profile. Type CIS to see all CIS policies in OpenSCAP (Figure 2). These are standard benchmark profiles.
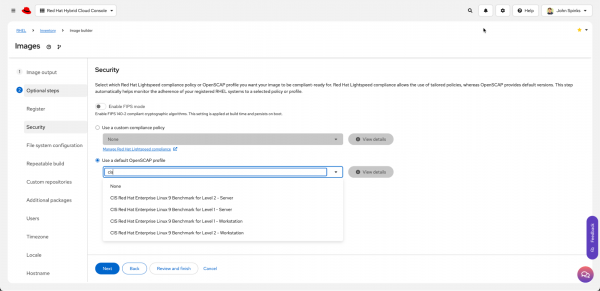
If you're already using the Red Hat Lightspeed compliance service, and you already have a policy set up and customized, then you can select Use a custom compliance policy at the top and select a policy (Figure 3).
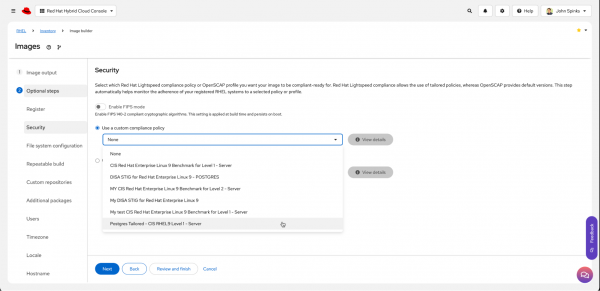
Selecting a policy will load information that Red Hat Lightspeed image builder would need to create an image that meets the specifications in the policy.
For example, CIS Level 1 Server requires /tmp to be a separate mount point. Image builder configures this automatically—I just need to adjust the partition size to my desired size (Figure 4). I could keep this smaller size and then automate expanding partition sizes at provisioning time using cloud-init, first boot scripts, or have Ansible configure it after it is provisioned.
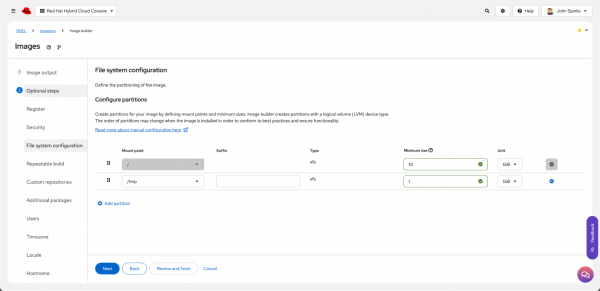
The policy rules apply changes like packages to include, services to enable or disable, and any kernel arguments.
Red Hat Lightspeed image builder allows you to make customizations as you continue through the wizard, and by the end you've created an image.
Results that work
For my purposes, I created an image in AWS and created several systems from the resulting Amazon machine image (AMI). When I used Red Hat Lightspeed compliance to evaluate these systems, the result was a system that was 100% compliant with my policy (Figure 5).
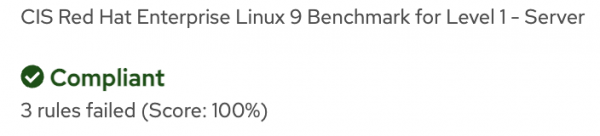
There were only 3 rules that failed (due to the way OpenSCAP weighs rules and calculates scores, a 100% compliant result is possible while still having individual failed rules). When I looked at the failures, they were all things that made sense for an AWS deployment like "Limit users’ SSH access". If I wanted to, I could further customize the policy to not scan for this rule or make changes to the system so that this rule will pass for future scans.
Interactive demos
This interactive demo walks you through evaluating and remediating for regulatory compliance. This includes creating, customizing, and viewing reports for the policy. The hosts shown in this interactive demo are RHEL 8 hosts that were built the old way with lots of failed rules.
If you want to see how to use Red Hat Lightspeed image builder to create compliant images, check out this interactive demo on Building and launching compliant images.
Compliance, simplified
A process that used to take me hours was drastically simplified down to just a few minutes. With my image built, I was able to re-deploy quickly, so when it comes time to move to RHEL 10 I know this can save me a lot of time.
Red Hat Lightspeed image builder drastically simplified how I create compliant systems in my environment. If you're struggling to create compliant images, then I encourage you to give it a try.
