Kubernetes admission control with validating webhooks
Learn to write, configure, and install a webhook that intercepts and validates Kubernetes requests, stopping users from creating rules with invalid fields.

Learn to write, configure, and install a webhook that intercepts and validates Kubernetes requests, stopping users from creating rules with invalid fields.
Learn how to connect to external PostgreSQL databases via SSL/TLS for Red Hat's single sign-on technology (SSO). This technique ensures secure connectivity.

Read how memory allocation, or malloc hooks, were unsafe in multi-threaded environments and why they were removed from the GNU C Library, or glibc.
Improve your data security by integrating your existing systems and using

Gather the data you collect into real-time information you can use to optimize
Learn about the tools Red Hat has available to implement GitOps workflows. Use the examples to set up control planes to gain full control of your project.

Find out what's new in Red Hat Integration Service Registry 2.0, then use the new single sign-on feature to secure your registry using OpenID Connect.
Create scanning tools that search for specific instruction sequences in binary files. These tools help you verify compiled executable security and uniformity.

Help GCC detect buffer overflows by using source-level annotations. This article describes three simple annotation types to detect out-of-bounds accesses.
Secure open source, cloud-native APIs with Authorino. This external authorization service lets you configure it quickly via the Kubernetes API for flexible use.
Follow this tutorial to size your single-sign on project. Learn how to design benchmarks and assess performance to develop an more precise estimate.
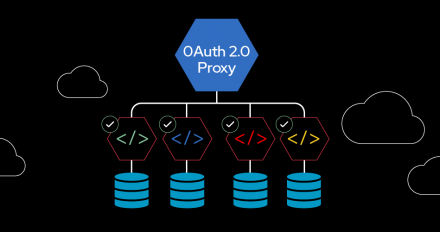
This tutorial shows how to secure multi-language microservices with oauth2-proxy and Keycloak. You can add authentication without coding OpenID Connect clients.
Pseudo-normal numbers represent a gap in floating point number classification in the long double format on Intel x86. Find out how glibc and GCC address it.
After installing Red Hat's single sign-on technology, you might want to change the default database. Here's how to configure SSO for MariaDB or MySQL.

Learn how knowledge graphs can help you address vulnerabilities in open source software dependencies quickly and efficiently.
Explore more features in GCC 11 that can help detect dynamic memory bugs in C and C++, and learn about the compiler's limitations.

Dynamic memory management bugs are hard to find and frequently targeted in C and C++ programs, but GCC 11's enhanced malloc attribute is here to help.

Learn how to set up single-use access tokens in Red Hat 3scale API Management to enhance application security with this X-step demo.
Follow the instructions in this article to quickly connect a Red Hat single sign-on technology client with a Red Hat Data Grid server on Red Hat OpenShift.

The GNU C Library's 2.33 release adds buffer overflow protection for C/C++ programs. Find out how _FORTIFY_SOURCE=3 improves overflow protection in glibc.

Get started with using Red Hat CodeReady Dependency Analytics to analyze dependency vulnerabilities in your Golang application stack.

Set up authentication and authorization to connect Red Hat Integration Service Registry with a secure Red Hat AMQ Streams Kafka cluster.

Get a quick introduction to C and C++ code analysis with clang-tidy, including checking for rule violations and integrating clang-tidy with a build system.

Improving security with Istio | DevNation Tech Talk

Discover what's new in Red Hat JBoss Enterprise Application Platform 7.4 beta, including new security, server management, and developer features.