Secure communication with Red Hat Decision Manager
Get step-by-step instructions to install and configure a self-signed certificate for secure HTTPS communication with Red Hat Decision Manager.

Get step-by-step instructions to install and configure a self-signed certificate for secure HTTPS communication with Red Hat Decision Manager.

Extend common DevOps tools and processes with DevSecOps to improve app security. Enable security automation and help teams collaborate on security policies.

Get started with using Red Hat Universal Base Images for lightweight, secure, and free container builds, with examples based on Golang and Python.

Learn to automate dependency analytics by integrating code scanning into your CI pipeline. Use the CodeReady Dependency Analytics GitHub Action to spot flaws.

Improve security by using biometric data for user authentication. Configure Red Hat SSO to use WebAuthn and deploy test client for biometric authentication.
Set up the NVIDIA Morpheus AI application framework and NVIDIA BlueField-2 data processing units with Red Hat OpenShift and Red Hat Enterprise Linux.
Checkpoint/restore is useful when migrating containers in Kubernetes. Learn how this feature was implemented and how it's used in container migrations.

Learn how to connect to Red Hat Data Grid without using SSL. This service uses single sign-on tech (SSO) without SSL when you don't require secure connectivity.

Learn how security teams are using DevOps principles and CI/CD pipelines to

Learn how Project Thoth's new security recommender makes a recommendation, then use the Thamos CLI to find security issues in your Python library code.
Learn to write, configure, and install a webhook that intercepts and validates Kubernetes requests, stopping users from creating rules with invalid fields.
Learn how to connect to external PostgreSQL databases via SSL/TLS for Red Hat's single sign-on technology (SSO). This technique ensures secure connectivity.

Read how memory allocation, or malloc hooks, were unsafe in multi-threaded environments and why they were removed from the GNU C Library, or glibc.
Improve your data security by integrating your existing systems and using

Gather the data you collect into real-time information you can use to optimize

Learn about the tools Red Hat has available to implement GitOps workflows. Use the examples to set up control planes to gain full control of your project.

Find out what's new in Red Hat Integration Service Registry 2.0, then use the new single sign-on feature to secure your registry using OpenID Connect.
Create scanning tools that search for specific instruction sequences in binary files. These tools help you verify compiled executable security and uniformity.

Help GCC detect buffer overflows by using source-level annotations. This article describes three simple annotation types to detect out-of-bounds accesses.
Secure open source, cloud-native APIs with Authorino. This external authorization service lets you configure it quickly via the Kubernetes API for flexible use.
Follow this tutorial to size your single-sign on project. Learn how to design benchmarks and assess performance to develop an more precise estimate.
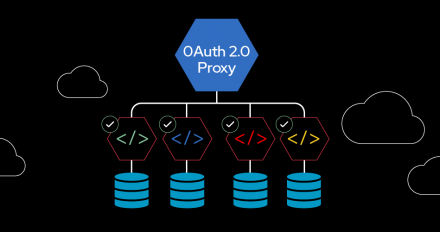
This tutorial shows how to secure multi-language microservices with oauth2-proxy and Keycloak. You can add authentication without coding OpenID Connect clients.
Pseudo-normal numbers represent a gap in floating point number classification in the long double format on Intel x86. Find out how glibc and GCC address it.
After installing Red Hat's single sign-on technology, you might want to change the default database. Here's how to configure SSO for MariaDB or MySQL.

Learn how knowledge graphs can help you address vulnerabilities in open source software dependencies quickly and efficiently.