
X.509 user certificate authentication with Red Hat's single sign-on technology
Configure a browser authentication flow using X.509 user-signed certificates with Red Hat's single sign-on technology and OpenSSL.

Configure a browser authentication flow using X.509 user-signed certificates with Red Hat's single sign-on technology and OpenSSL.

Red Hat Developer Program Terms and Conditions
Get an overview of fixes and enhancements to the -fanalyzer static analysis pass, currently being updated for security, state tracking, and more in GCC 11.

How to enable HTTPS and SSL Termination in an already running Quarkus application in Openshift.

Learn how to restrict or limit access to applications that are federated with Keycloak for users authenticating through a third-party provider.
Learn how to integrate Red Hat's single sign-on tools version 7.4 with Red Hat Directory Server 11 (LDAP), and synchronize users and groups between the two.
Discover connection pooling, and then learn how to use Oracle's Universal Connection Pool with an Oracle RAC database in a JBoss EAP deployment.

Learn how to go beyond the simple login API and enable the full force of Keycloak's authentication and authorization features using the Keycloak REST API.

Set up Multus-CNI and CDI DataVolumes in KubeVirt to configure your network and storage requirements for high performance, security, and scalability.
Set up a 3scale and OpenID Connect integration and authorization flow using Okta as your OIDC provider and JSON Web Token and Oauth2 for verification.
Explore the Red Hat 3scale API Management 2.9 highlights, including air-gapped installation on Red Hat OpenShift and new APIcast policies.

Protect your Red Hat OpenShift secrets. Learn how to use PKCS #11 URIs and libssh to store private information in highly secure hardware tokens.

Use Keycloak's authentication service provider interface to develop a custom MobileAuthenticator class that you can run in your JBoss EAP container.

Learn how to configure a Quarkus application with Red Hat Data Grid and deploy it on Red Hat OpenShift with Data Grid 8.1's new security features.

Explore the new Automatic Certificate Management Environment (ACME) protocol support available through the Open Liberty 20.0.0.10 Java Red Hat Runtime.
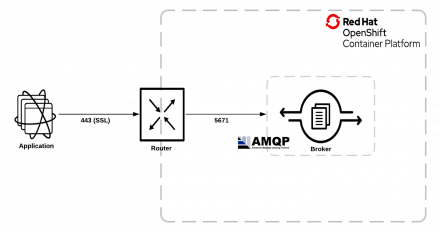
Learn how to connect external clients to Red Hat AMQ Broker using the SSL or TLS protocol when deploying on Red Hat OpenShift.

Red Hat CodeReady Workspaces 2.3 brings two ways to inject secrets, cluster-wide proxy support, devfile and IDE plugin updates, and more.

Explore the relationship between iptables and nftables, and discover how iptables-nft gives you the best of both worlds without breaking legacy code.

Compare Kubernetes development to OpenShift's CLI and native extension API resources, including build configs, deployment configs, and image streams.
Learn how to integrate Red Hat AMQ 7.7 with Apache Directory Studio, which is an LDAP browser and directory client for ApacheDS.
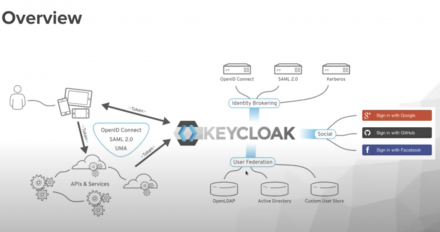
In this DevNation Tech Talk, we take a deep dive into Keycloak to handle open source identity and access management with modern applications and services.

Learn the basics of SELinux, including type enforcement, Multi-Category Security (MCS) Enforcement, and Multi-Level Security (MLS) Enforcement, with the help of some friendly cats and dogs!
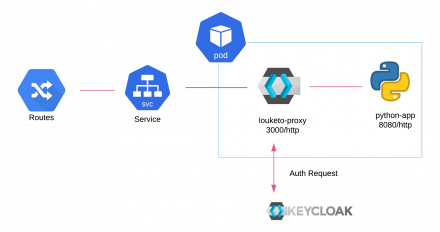
Learn how to use Louketo Proxy as a sidecar to provide authentication for your microservices that are built using multiple languages.
Secure Vue.js apps with Keycloak | DevNation Tech Talk

Discover the new features in Open Liberty 20.0.0.7, which give you more control over JWT cookies for SSO, LTPA cookies for TAI or SPNEGO, and more.