
Manage credentials with Tekton and OpenShift on IBM Cloud
Learn how to protect secrets, enforce compliance, and build a trusted software supply chain using Tekton Pipelines on Red Hat OpenShift on IBM Cloud.

Learn how to protect secrets, enforce compliance, and build a trusted software supply chain using Tekton Pipelines on Red Hat OpenShift on IBM Cloud.

Accelerate the adoption of Red Hat Developer Hub with the Adoption Insights

Go beyond performance and accuracy. This guide for technical practitioners details how to implement trust, transparency, and safety into your AI workflows.

Go from a fast Jenkins pipeline to a fast and more secure one with Red Hat Advanced Developer Suite, adding signing, SBOM validation, and runtime enforcement.
Learn about attestations from a neutral observer and how to make meaningful decisions about artifacts at release time, enabling flexibility and safety.

A comprehensive offering for developers that includes a range of tools to
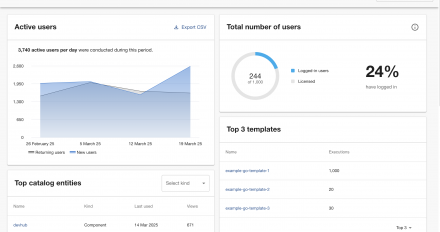
Red Hat Developer Hub 1.5 introduces Adoption Insights, a plugin that provides

As cyber threats become increasingly sophisticated, organizations need robust

1.0.2 Maintenance Release Announcement In case you were wondering why there hasn

Download Red Hat software for application developers at no-cost.

Discover how Red Hat Trusted Software Supply Chain makes it easier to create, deploy, and host security-focused applications in the container era.

Discover more about Red Hat Trusted Application Pipeline, a secure and easy solution for the DevSecOps outer loop.