ServiceNow IT Service Management (ITSM) is a leading IT service support and delivery platform with a reported global market share of over 50% in its category. While ServiceNow ITSM includes some out-of-the-box automation capabilities, unlike Red Hat Ansible Automation Platform, it doesn't automate or orchestrate other IT systems.
Ansible Automation Platform transforms IT service management by deploying end-to-end automated workflows that connect cloud, operating systems, network configuration, and more with ServiceNow. This allows your IT teams to operate more efficiently and collaborate around a single, common solution.
With Ansible Automation Platform, you can collect information from existing service tickets, open and close service tickets, and enrich those tickets with data collected across your IT infrastructure. Ticket enrichment ensures that teams make better decisions by having more context and visibility into the potential cause of issues and incidents. Your organization can repetitively and consistently resolve issues faster. The result is less downtime, increased team productivity, and an improved customer and end-user experience.
Implement enterprise-wide automation with Red Hat Ansible Automation Platform
This blog explores foundational automation tasks that organizations using ServiceNow ITSM can implement to get more value from their investment:
- Gather data from your ServiceNow ITSM.
- Create a ServiceNow ticket.
- Update the ticket with information from a CVE impacting Red Hat Enterprise Linux (RHEL) systems.
We recommend these use cases because they:
- Deliver both business and technical value without risk to production systems.
- Build a sequence of automation jobs that can be aggregated into a single seamless workflow for even greater efficiency.
- Can be extended to integrate with your existing observability tools as well as AIOps workflows.
Note
If you are new to Ansible Automation Platform, we strongly recommend our free technical overview course Ansible Basics: Automation.
Let's get started.
Step 1: Gather data from your ITSM
To retrieve information from service tickets on ServiceNow that could be used in your automation or for simple data gathering, we will use the Ansible Certified Content Collection for ServiceNow.
Create a playbook to gather facts about your ServiceNow ticket:
--- - name: Retrieve ServiceNow ticket details hosts: localhost gather_facts: no vars: ticket_number: "{{ ticket }}” tasks: - name: Retrieve incidents by number servicenow.itsm.incident_info: instance: host: "{{ servicenow_instance }}" username: "{{ servicenow_username }}" password: "{{ servicenow_password }}" number: "{{ ticket_number }}" register: result delegate_to: localhost - name: print debug: msg: "{{ result }}"- Create a job template using your ServiceNow instance information gathering playbook. Save your job template as "Collect ticket information" and then select Launch to run the template.
- You can extend this playbook by using the ansible.builtin.set_fact module to allocate relevant data into ansible variables or the ansible.builtin.set_stats to allow for the data to persist between templates in an automation workflow.
Step 2: Create a service ticket
Create another Ansible Playbook using the servicenow.itsm.incident module to create service tickets within the ServiceNow ITSM:
--- - name: Create Service Ticket hosts: localhost gather_facts: no vars: SN_HOST: "{{ lookup('env', 'SN_HOST') }}" SN_USERNAME: "{{ lookup('env', 'SN_USERNAME') }}" SN_PASSWORD: "{{ lookup('env', 'SN_PASSWORD') }}" tasks: - name: Create Ticket servicenow.itsm.incident: instance: host: "{{ SN_HOST }}" username: "{{ SN_USERNAME }}" password: "{{ SN_PASSWORD }}" state: New caller: Admin impact: low urgency: low register: ticket_details delegate_to: localhost - name: print debug: msg: "{{ result }}"Create a job template using your ServiceNow ticket creation playbook. Save your job template as "Create ServiceNow Ticket" and then select Launch to run the template.
Note
You can combine the 2 job templates into a simple automation workflow to both create a ticket and then gather information for that ticket.
Step 3: Enrich a ServiceNow ticket
This video shows the ticket enrichment process in action:
- Using Ansible’s ability to operate across multiple technology domains and gather information, or using the
ansible.builtin.urimodule to interact with an API, we can write a playbook that utilizes the following modules to enrich our tickets. In this example, we reference Red Hat Lightspeed (formerly Red Hat Insights) to gather information about one of our systems and the details of a CVE that has been detected on the system. We utilize the API module from Ansible to query Red Hat Lightspeed, then use the ServiceNow incident modules to create a service ticket with the relevant data.
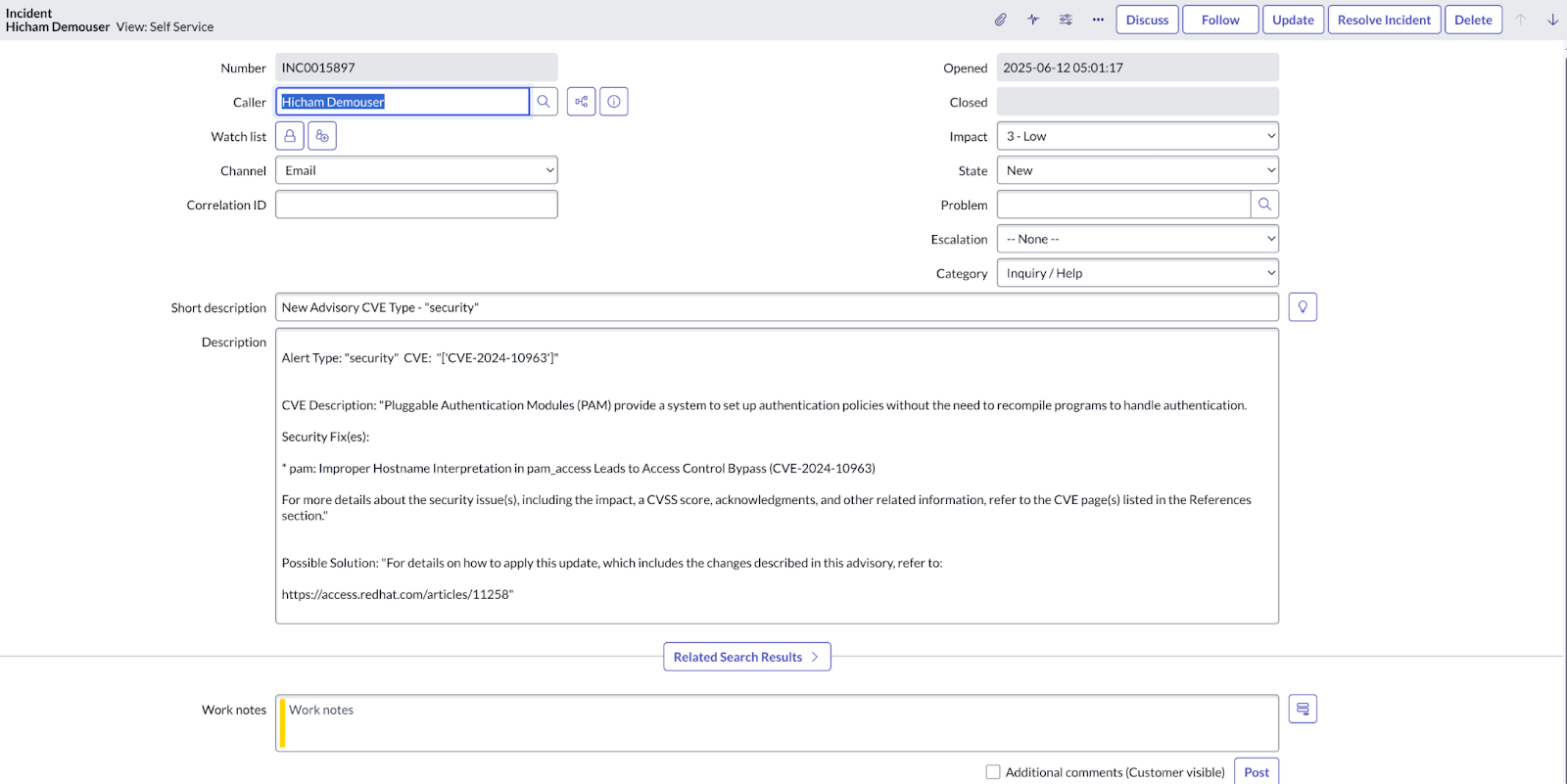
--- - name: Gather CVE Details hosts: localhost gather_facts: false vars: advisory_id: rhsm_username: rhsm_password: SN_HOST: "{{ lookup('env', 'SN_HOST') }}" SN_USERNAME: "{{ lookup('env', 'SN_USERNAME') }}" SN_PASSWORD: "{{ lookup('env', 'SN_PASSWORD') }}" tasks: - name: EDA | Insights | Retrieve related CVEs from Advisories ansible.builtin.uri: url: "https://console.redhat.com/api/patch/v3/advisories/{{ advisory_id }}/systems?page=1&perPage=20&sort=-last_upload&offset=0&limit=20" method: GET url_username: "{{ rhsm_username }}" url_password: "{{ rhsm_password }}" force_basic_auth: true status_code: 200 register: cves_list - name: Gather CVE details ansible.builtin.uri: url: "https://console.redhat.com/api/patch/v3/advisories/{{ advisory_id }}" method: GET url_username: "{{ rhsm_username }}" url_password: "{{ rhsm_password }}" force_basic_auth: true status_code: 200 register: cve_details - name: Extract type ansible.builtin.set_fact: cve_type: "{{ cve_details.json.data.attributes.advisory_type_name }}" cves_description: "{{ cve_details.json.data.attributes.description }}" solution: "{{ cve_details.json.data.attributes.solution }}" cves: "{{ cve_details.json.data.attributes.cves }}" - name: Create incident servicenow.itsm.incident: instance: host: "{{ SN_HOST }}" username: "{{ SN_USERNAME }}" password: "{{ SN_PASSWORD }}" state: new caller: "{{ SN_USERNAME }}" short_description: New Advisory CVE Type - "{{ cve_type }}" description: | Alert Type: "{{ cve_type }}" CVE: "{{ cves }}" CVE Description: "{{ cves_description }}" Possible Solution: "{{ solution }}" urgency: high register: new_incident- Create a job template using your CVE enrichment ticket playbook. Save your job template as Enrich CVE ticket.
- You can also add a Survey to the template to capture a user's input. In this example, we will submit the CVE advisory number. Then select Launch and provide the advisory from Red Hat Lightspeed to create an enriched service ticket.
- Review the ticket within ServiceNow (Figure 1).
Ready to get started with these ServiceNow ITSM automation use cases? Read our Solution Guide - ServiceNow ITSM Automation (login required).
Explore advanced automation use cases
As you expand your adoption of automation, the value and benefits to your organization actually increase while the amount of effort required to maintain ServiceNow ITSM decreases.
Once you have tackled the basics of automating ServiceNow ITSM with Ansible Automation Platform, you're ready to expand into more advanced forms of automation:
- Speed up server provisioning with Event-Driven Ansible.
- Integrate ITSM into your network workflows. Learn how Southwest Airlines tackled this use case.
- Learn how to scale automation adoption across your organization.
