3scale by Red Hat API and Identity Management Series
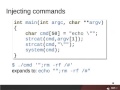
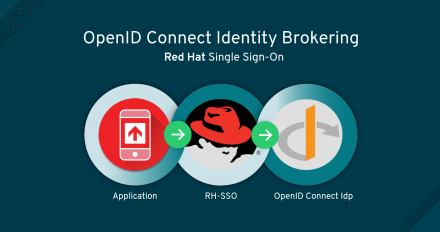
API management, such as Red Hat's 3scale evolved to meet the challenges that arise from making APIs available to client applications. Learn how how an existing Identity and Access Management (IAM) solution, can be integrated with an Identity Providers (IdP) to provide secure access to API endpoints using 3scale.