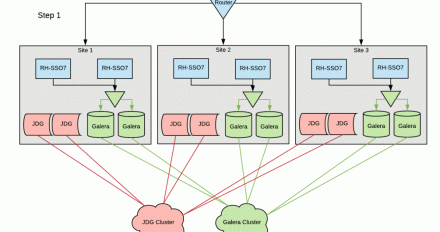
Five layers of security for Red Hat Data Grid on OpenShift
This article talks about multiple layers of security available while deploying Red Hat Data Grid on OpenShift. The layers of security offer a combination of security measures provided by Data Grid as well as by OpenShift/Kubernetes.