
What’s new for developers in OpenShift 4.17
Find out what new features and capabilities have been provided in Red Hat

Find out what new features and capabilities have been provided in Red Hat
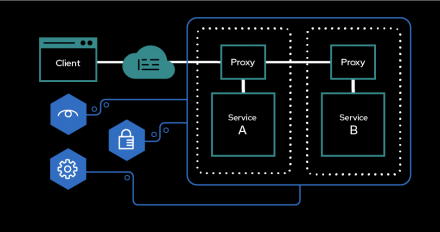
Learn how to implement the Kubernetes Gateway API 1.0 feature on Red Hat OpenShift, then use it to configure traffic into an application running on OpenShift clusters.

Download Red Hat software for application developers at no-cost.
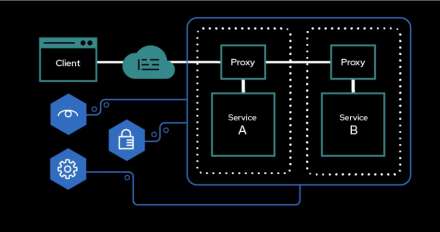
Explore OpenShift Service Mesh's multi-cluster features and learn how to enable the multi-primary deployment model, now in developer preview in OpenShift Service Mesh 2.6.

Use API management and service mesh together to setup a comprehensive service...

Learn a simplified method for installing KServe, a highly scalable and standards-based model inference platform on Kubernetes for scalable AI.

This article explores the concept of cloud-native canary deployment strategy using Argo Rollouts and OpenShift Service Mesh following a GitOps model.

Learn how to get the most from OpenShift Service Mesh tracking and monitoring.

Explore the differences between Red Hat OpenShift Service Mesh and Red Hat Service Interconnect for effectively running applications across OpenShift clusters.
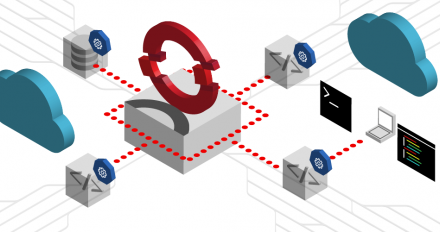
Learn about a new Istio operator that will serve as the foundation for Red Hat OpenShift Service Mesh 3, bringing simplified configuration and management.

Learn how to configure HashiCorp Vault as the PKI engine for signing OpenShift Service Mesh workloads using cert-manager and istio-csr.

This article provides resources to get you where you need to go to succeed on your container journey.

Explore the benefits of using service mesh and API management in your microservices architecture and discover useful ways to leverage both solutions together.

Learn how to configure and run an application with OpenShift Service Mesh in this 4-step demonstration.

The common "no healthy upstream" message is usually caused by configuration errors. Knowing these errors and how to find them leads to quicker fixes.
Discover 10 essential solutions and tools to mitigate security risks throughout each step of the API life cycle.

Kamesh Sampath provides an overview of Envoy and Istio, two open source projects that will change the way you write cloud-native Java applications on Kubernetes. We’ll show how to download and set up Istio on your local laptop, then deploy Java microservices as part of the Istio service mesh with Istio sidecar proxy.

Learn how to manage APIs using the Red Hat Integration adapter for Istio.

Download the Introducing Istio Service Mesh for Microservices e-book and explore key microservices capabilities that Istio provides on Kubernetes and OpenShift.

Istio Pool Ejection allows you to temporarily block under- or non-performing pods from your system.

Have you ever used an open source project? Of course you have, but have you made any contributions yourself? Filed a bug report? Submitted a patch? Have you ever started your own OSS project, or taken a closed/private project public? What licenses should you use? How do you manage contributions? How do you support contributors and still get work done? What do you do with difficult community members? In this talk we'll go over the basics of OSS: how to get involved, how to start a project, how to manage contributions. We'll discuss project lifecycles, legal CYA tips, and how to keep projects moving. You'll see the inner workings of real OSS projects, and learn how to be a better OSS user and producer.
