
Developing micro-microservices in C on Red Hat OpenShift
Explore the implications of implementing a REST-based web service in C by determining sun/moonrise and set for a specific location and day.

Explore the implications of implementing a REST-based web service in C by determining sun/moonrise and set for a specific location and day.

Learn how to troubleshoot, monitor, and profile your container-based Java applications with JDK Flight Recorder, courtesy of OpenJDK 8u 262.

Multipath TCP is coming as a Tech Preview on upcoming RHEL 8.3. Learn how to run a basic client/server connectivity test.

Explore the relationship between iptables and nftables, and discover how iptables-nft gives you the best of both worlds without breaking legacy code.
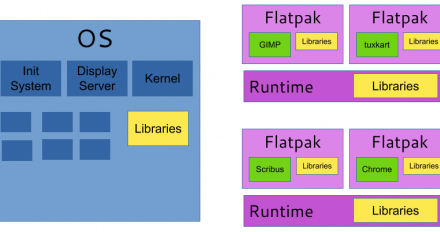
Learn how to use the new Flatpak runtime to build containerized desktop applications on top of Red Hat Enterprise Linux 8.2.
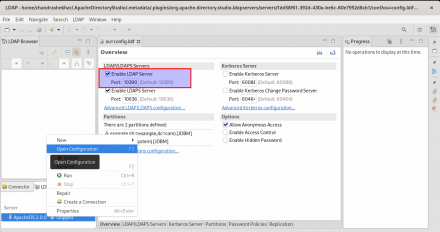
Learn how to integrate Red Hat AMQ 7.7 with Apache Directory Studio, which is an LDAP browser and directory client for ApacheDS.
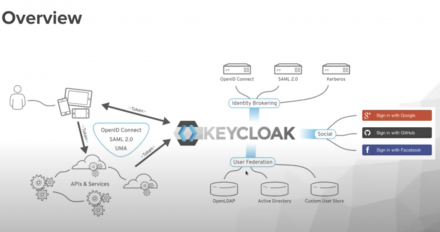
In this DevNation Tech Talk, we take a deep dive into Keycloak to handle open source identity and access management with modern applications and services.

Learn the basics of SELinux, including type enforcement, Multi-Category Security (MCS) Enforcement, and Multi-Level Security (MLS) Enforcement, with the help of some friendly cats and dogs!
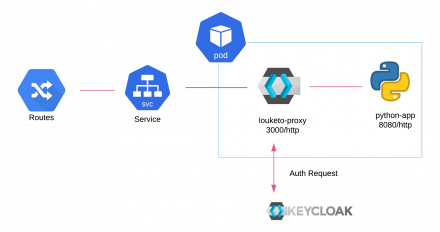
Learn how to use Louketo Proxy as a sidecar to provide authentication for your microservices that are built using multiple languages.

Discover what's new in JBoss Tools 4.16.0 and Red Hat CodeReady Studio 12.16 for Eclipse 4.16 (2020-06), from UI updates to updated JDT extensions.
Watch this session to learn the root cause of common inconsistent state-related bugs in your production Java code, and how to solve them.

Discover how to improve your code rather than over-relying on debuggers through lessons learned by a developer that didn't use a debugger for a month.

Learn how the Clang compiler implements profile-guided optimization, then explore a real-world bug that shows the pitfalls of the current approach to PGO.

Build Java applications that run inside containers in a secure, stable, and tested manner in Red Hat Enterprise Linux 8.2 with the Red Hat build of OpenJDK.

Discover how GraalVM adding DWARF debug information to its Linux images enables effective source-level Java-native image debugging through gdb.

Improve Python 3.8's run speed by 30% in RHEL 8.2 by compiling with GCC's -fno-semantic-interposition flag.
This video walks you through the "why" and "how" of Java in containers, from image sizes to the development and deployment processes.

In part 2 of this series, avoid aliasing restrictions with programming language exemptions and compiler extensions, and explore possible resulting problems.

In part 1 of this series, explore C/C++ language restrictions, their challenges and pitfalls, and examples demonstrating their benefits in optimized code.

Explore the Red Hat Enterprise Linux (RHEL) 7 language and runtime updates available in Red Hat Software Collections 3.5 and Red Hat Developer Toolset 9.1.

Get started with a new coverage counter that makes interpreting vHost user TX contention in Open vSwitch easier, especially when combined with perf.

Discover the design principles and performance improvements behind GCC's code generation strategies for defending against stack clash attacks.

Red Hat will release a Universal Base Image for Node.js 14 for Red Hat OpenShift and Red Hat Enterprise Linux, but this article gets you started today.
Learn how to seamlessly automate Google Cloud Platform resources using the new auto-generated Ansible modules and your Red Hat Ansible Tower credentials.

Learn how to use Nagios passive checks and OpenShift's Watchdog alert to make sure that alerting is still working in your cluster.