In today's dynamic IT landscape, efficient management of server infrastructure is paramount. Regular patching is essential for maintaining security, stability, and compliance across enterprise environments. Red Hat Enterprise Linux (RHEL) servers are widely used in business-critical operations, making timely patching a crucial task. Manual patching can be time-consuming and error-prone, especially for large server deployments. In this technical blog, we'll explore how to streamline patch updates of SELinux on RHEL servers using Red Hat Ansible Automation Platform 2.4.
Prerequisites
This article requires the following prerequisites:
- Installed Ansible Automation Platform.
- One or more RHEL machines.
- Basic knowledge of RHEL.
- Basic knowledge of Ansible.
- A no-cost Red Hat Developer Subscription for Individuals.
Register RHEL system on Red Hat Hybrid Cloud Console
To initiate registration and scanning of your RHEL machine on the Red Hat Hybrid Cloud Console, execute the following commands:
[root@server ~]# insights-client --register [root@server ~]# rhc connect
Connecting server to Red Hat.
This might take a few seconds.
Username: user1
Password:
● Connected to Red Hat Subscription Management
● Connected to Red Hat Insights
● Activated the Red Hat connector daemon
Manage your Red Hat connector systems: https://red.ht/connectorWhen accessing the Red Hat Hybrid Cloud platform, navigate to Red Hat Lightspeed -> System. This will provide you with the hostname of your RHEL server, as demonstrated in Figure 1.
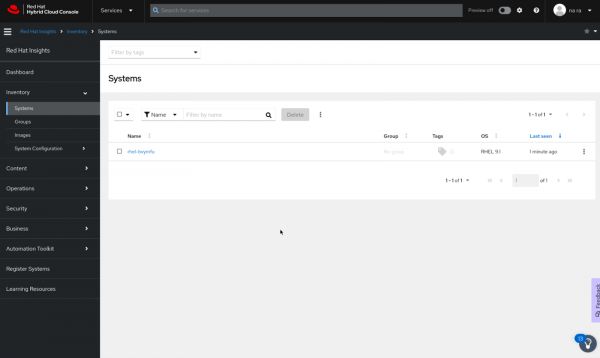
Click on the listed host and select the Vulnerabilities option from the tabs. This will display a list of all vulnerabilities present in your system, categorized by severity level.
Search for "SELinux" in the search box to filter the available vulnerabilities related to SELinux, as depicted in Figure 2.
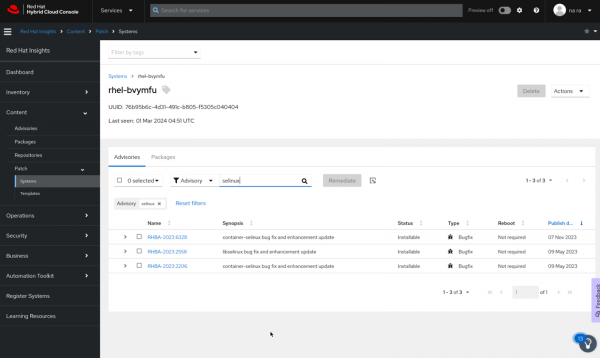
Click on the name of the vulnerability (RHBA-20236328) to access the respective RPM package necessary to patch the issue. Incorporate this RPM package into the playbook, following the example provided below.
Patch-update.yaml
---
- name: Red Hat Enterprise linux patch update
hosts: rhel-server.example.com
gather_facts: yes
tasks:
- name: selinux patch update
dnf:
name: https://access.cdn.redhat.com/content/origin/rpms/selinux-policy/38.1.23/1.el9_3.2/fd431d51/selinux-policy-38.1.23-1.el9_3.2.noarch.rpm
state: present
- name: Update all packages
dnf:
name: "*"
state: latestThis approach enables you to automate patching tasks using Ansible, which serves as the enterprise automation solution within Ansible Automation Platform. The instructions outlined below will guide you through executing the patch playbook via Ansible Automation Platform.
To execute the playbook, it's essential to satisfy the dependencies such as Machine Credentials, Project, Inventory, and Template, for that following instructions are given.
Create machine credentials
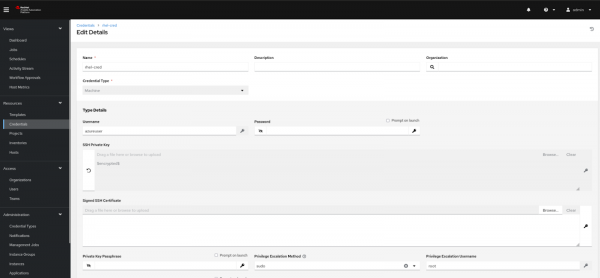
To enable Ansible Automation Platform access to the RHEL server that requires patch updates, it is necessary to define the accessibility credentials of that machine, such as private keys, root permissions, and admin user credentials. Figure 3 depicts this.
- From the left menu select the Credentials.
- Give it a Name.
- Select credentials type as Machine credentials.
- Under Type Details add the username of the RHEL server.
- Add SSH private key.
- Define sudo as Privilege Escalation Method.
- Add root as Privilege Escalation Username.
- Click on the Save button.
Add inventories
An inventory is a collection of hosts against which jobs can be launched, the same as an Ansible inventory file.
- From the left menu, select Inventories.
- Click on Add button and select Add Inventories option.
- Enter a Name to the inventory.
- Next, add the host to the inventory. Check the connectivity with the server using the ping module by clicking the Run Command button.
- Select the Run Command first.
- Select the ping module from the drop-down and choose Machine Credentials.
- Keep the rest of the details as default (you can change the settings per your requirement).
- Click Launch.
After successful run of the ping module you will get the pong response in the jobs. If it fails, kindly check the credentials and inventories, and launch it again.
Create a Project
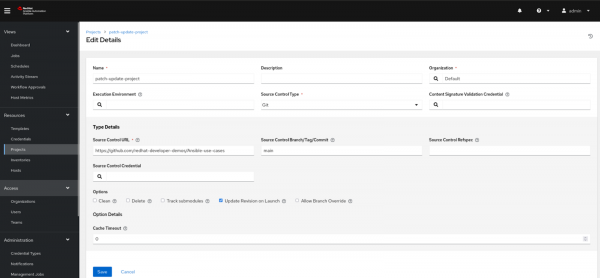
A project is a logical collection of Ansible playbooks, represented in the automation controller. You can manage playbooks and playbook directories by either placing them manually under the project base path on your controller server, or by placing your playbooks into a source code management (SCM) system supported by the automation controller, including Git, Subversion, and Mercurial. Project configuration is shown in Figure 4.
- Select the Project option under Resources from the left menu.
- Define Name of Project.
- Under Source Control Type select Git.
- In Source Control URL, define the URL of the GitHub repository.
- In the Source Control Branch define the main branch.
- Click on the Save button.
Create and launch the template
A Job template is a definition and set of parameters for running an Ansible job. Job templates are useful to execute the same job many times. Job templates also encourage the reuse of Ansible Playbook content and collaboration between teams.
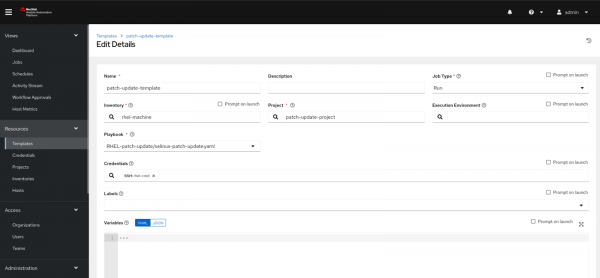
Create a template that will execute the job for us, as shown in Figure 5.
- From the left menu, select Templates and create a New template.
- Click on Add button and select the Add job template.
- Name the template.
- Select the inventory.
- Select a Project.
- Choose the playbook you want to run in the template.
- Choose Credentials.
- Click on the Save button and then click the Launch button.
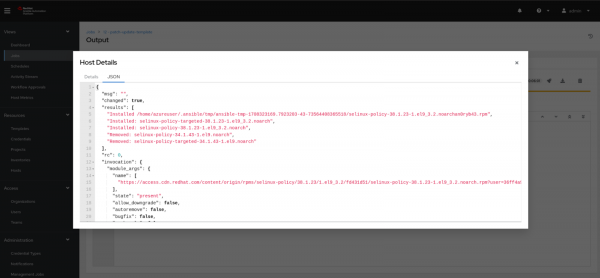
In the jobs section, you will find the following output after the successful execution of the playbook on the RHEL server.
Identity added: /runner/artifacts/12/ssh_key_data (/runner/artifacts/12/ssh_key_data)
PLAY [Red Hat Enterprice linux patch update] ***********************************
TASK [Gathering Facts] *********************************************************
ok: [rhel-server.example.com]
TASK [selinux patch update] ****************************************************
changed: [rhel-server.example.com]
TASK [Update all packages] *****************************************************
changed: [rhel-server.example.com]
PLAY RECAP *********************************************************************
rhel-server.example.com : ok=3 changed=2 unreachable=0 failed=0 skipped=0 rescued=0 ignored=0 Have a closer look in the job logs as shown in Figure 6.
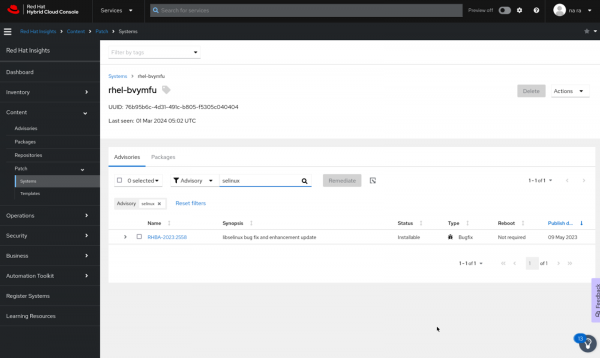
After successfully executing the playbook on the Ansible Automation Platform, we need to revisit the Red Hat Hybrid Cloud portal to verify if the vulnerability has been resolved, as depicted in Figure 7.
What's next in your automation journey?
In this article, you learned how to do a patch update on the Red Hat Enterprise Linux server with the help of Ansible Automation Platform.
Now that you have set up Ansible Automation Platform, explore our interactive labs at Red Hat Developer.
Last updated: November 5, 2025