
Enhance security with automation
Explore proven strategies for protecting against security threats using automation in this short e-book.

Explore proven strategies for protecting against security threats using automation in this short e-book.

Discover the gains and costs of GCC’s enhanced runtime buffer overflow protection. Level 3 _FORTIFY_SOURCE preprocessor macro may detect more buffer overflows, but there’s a cost.
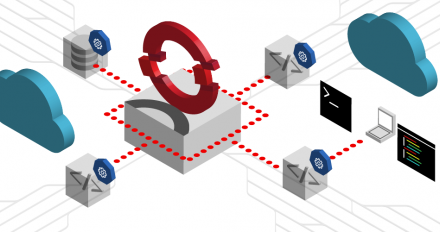
Discover how to improve the security of your Software-as-a-Service deployment at the hardware, OS, container, Kubernetes cluster, and network levels.

JSON Web Tokens (JWT) are a web standard–RFC 7519–but using them with Eclipse MicroProfile may be a mystery. This cheat sheet by Red Hat Senior Software Engineer Martin Stefanko will help you get moving immediately.

We show how to set up Red Hat AMQ Streams end-to-end TLS encryption using a custom X.509 CA certificate on the OpenShift platform.

This complete example shows how to easily set up the AMQ 7 end-to-end TLS encryption using a custom X.509 certificate on Red Hat OpenShift.

How to sign and verify signatures of container images using podman and skopeo

We show how to simplify SSL certificates using Let's Encrypt with Apache httpd on Red Hat Enterprise Linux 7.

Instructions in the NOP space are an attractive way to provide new performance and security features; we show how to use them effectively.
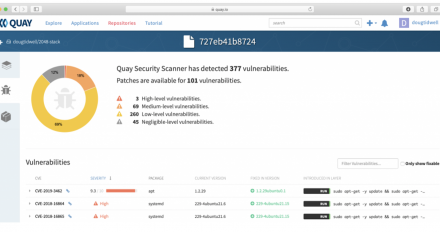
Quay.io is a container image repository that automatically scans your images for security vulnerabilities. Learn how to use this powerful feature.

We share some recent improvements for go-toolset, including a feature that lets Go call into a FIPS 140-2 validated cryptographic library.

This article covers how the -fstack-check capability in GCC works and explains why it is insufficient for mitigating Stack Clash attacks.

This article talks about multiple layers of security available while deploying Red Hat Data Grid on OpenShift. The layers of security offer a combination of security measures provided by Data Grid as well as by OpenShift/Kubernetes.

This article describes how to download and install Red Hat Single Sign-On for no cost. Red Hat Single Sign-On is an easy-to-use access management tool that takes care of the details of most authentication protocols, user consent with UMA, and even access control.

Annocheck a new utility to examine how a binary was built and to check that it has all of the appropriate security hardening features enabled. It also has several other modes that perform different kinds of examination of binary files.
Video: Security Considerations for Container Runtimes. Explains/demonstrates using Kubernetes with different security features for your container environment.

For times when you can't use ssh-copy-id to add your public key to a server, this article explains how to do it manually and set the correct permissions.

This post describes how to secure ASP.NET Core applications on OpenShift using HTTPS for two use-cases: terminating SSL in OpenShift for public routes and terminating SSL in ASP.NET Core directly using OpenShift-generated service certificates.

This post shows how to set up LDAP authentication on Red Hat AMQ 7. As part of the procees, it describes how to configure AMQ to authenticate users from LDAP and allow only users from a specified group to access the AMQ management console and publish messages in queues.

Watch this DevNation Live video to learn how to secure apps and services with Keycloak. Examples shown cover REST with Node.js, PHP, and HTML5.

For developers, sudo access can be very useful for automating steps in build scripts. Learn how to configure sudo access and enable sudo during system installation.


This post provides an example of how to configure role-based access control on top of Red Hat AMQ--a flexible, high-performance messaging platform that provides a role-based security model with built-in support for separation of duties.
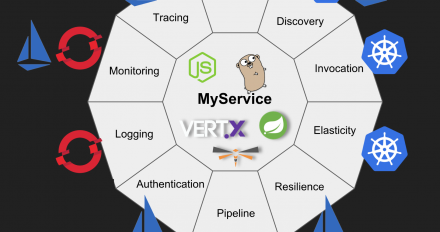
Kubernetes and related technologies, such as Red Hat OpenShift and Istio, provide the non-functional requirements that used to be part of an application server and the additional capabilities described in this article. Does that mean application servers are dead?

For added security, .NET Core applications that require access to external libraries can be run in a disconnected environment (one without internet access). Here's how.